The rise in the value of cryptocurrencies has inevitably drawn the eye of criminals, and the concentration of crypto in the cryptocurrency exchanges has focused that attention. Coinbase is the largest exchange in the U.S., and researchers have detected numerous phishing campaigns against Coinbase users.
The size/value of Coinbase is impressive. It claims to have more than 56 million verified users in more than 100 countries. Its traded volume is around $335 billion, and it has $223 billion in assets on the platform.
Researchers at anti-phishing firm INKY have discovered dozens of current phishing campaigns targeting Coinbase users. A blog post today describes just one designed to steal Coinbase login credentials for the theft of cryptocurrency, and financial and personal details.
This campaign uses a well-written and presented email supporting the Coinbase logo. There is little in the content to indicate a scam – no spelling errors or typos, and it uses acceptable style and grammar. The pitch differs slightly from the "we have detected unauthorized activity and have blocked your account" to one saying, "we have actioned your request to disable your account". Re-enabling the account requires clicking a button and re-entering credentials.
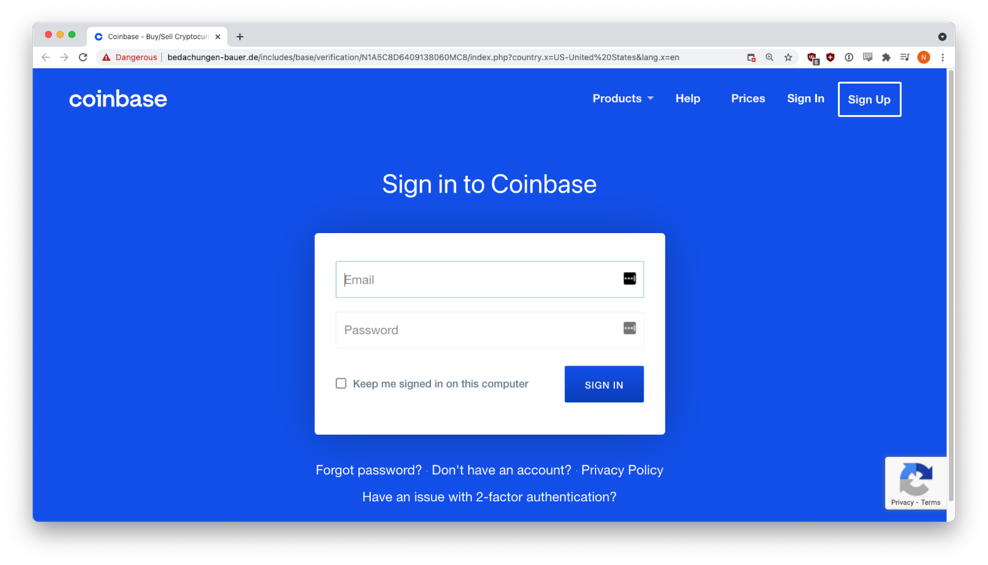
The email was sent from a hijacked email account. If targets were fooled and clicked the presented button, they were sent to a perfect copy of the real Coinbase login page. This fake page was hosted on the website of a German roof renovation company. Compromising websites and using them to host and hide material in orphan pages is a common practice among criminals.
In this instance, the only visual giveaway that the page was false was in the browser’s link address bar (‘bedachungen-bauer[.]de’ rather than ‘coinbase[.]com/signin’). Any credentials entered into this fake page was immediately harvested and sent to the criminals.
Coinbase, along with most authorities, urges users to employ two-factor authentication. INKY warns that this may not be enough. Although not used in this campaign, criminals can use man-in-the-middle attack frameworks (such as Evilginx) to capture the 2FA token sent to the phished client. Evilginx uses a Nginx HTTP server to proxy real websites to phishing victims, capturing any 2FA token that the website may send as a browser cookie to the client.
Read full article: https://www.securityweek.com/coinbase-users-face-ongoing-phishing-attacks


