Few companies experience the kind of rapid growth that Zoom saw in 2020. As a result of the COVID-19 pandemic lockdowns, this web-based video conferencing giant jumped from 10 million daily meeting participants in December 2019 to 300 million just four months later.1
With millions of remote students, companies, and workers relying on Zoom’s online services to replace their face-to-face meetings, a veritable phishing frenzy was created and cyber criminals around the globe tried to capitalize on the opportunities.
Early on, INKY began observing an explosion of fake meeting invitations that impersonate Zoom. In fact, during the first few weeks of the 2020’s summer, INKY stopped approximately 5,000 of these phishing attacks. In one of their published reports, INKY highlighted the origin and attack mechanism of 13 unique phishing templates, all designed to lure Zoom users into giving up the kinds of confidential credentials that allow cybercriminals to steal billions of dollars each year. With average losses per company of more than $96,000 per incident in 2020, these types of phishing attacks spell Zoom and doom for many small-to-mid-sized businesses.
So, how is it done? Let’s start by looking at the origins of the phish. The sender’s IP address is used to determine the origin of each phishing email. However, this is not a concrete method to reveal a cybercriminal’s physical location. Sophisticated attackers can conceal their location by leveraging compromised servers or using cryptocurrency to purchase virtual private servers from hosting providers. These methods also allow a cyber attacker to evade geographic filters.
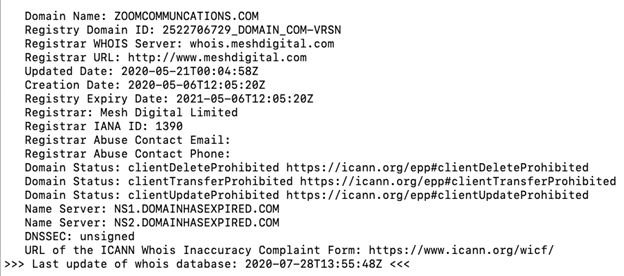
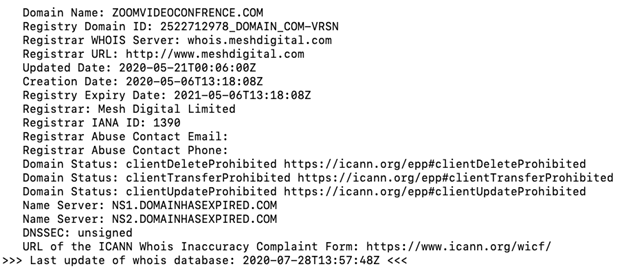
At INKY, most of the Zoom impersonator phishing emails we have seen came from hijacked accounts, but we also saw newly created domain names like zoomcommuncations.com and zoomvideoconfrence.com. As disturbing as that is, it’s also what makes these fake meeting invitations so easy to fall for and so difficult for traditional Secure Email Gateways (SEGs) to catch.
Fake attachments and malicious links make up the next chapter of this phishing tale. These phishing emails may appear to be from Zoom, but they were actually part of a credential harvesting operation targeting Microsoft users. Victims that clicked on either malicious links or HTM/HTML attachments were directed to spoofed Office365 and Outlook login pages, like the ones shown below. If the hacker includes a fake attachment, it leads to a fake login page that’s locally hosted on the recipient’s computer, not the internet. To make matters worse, the HTML, JavaScript, and PHP code is usually encoded so it’s unreadable to humans and automated security tools. It’s is a clever way to remain undetectable and evade URL reputation checkers. Similarly, if the hacker includes a malicious link, these redirect to a fake login that’s hosted on a compromised server or a hosting service the attacker paid for.
Wouldn’t you say the login screens below look pretty convincing?

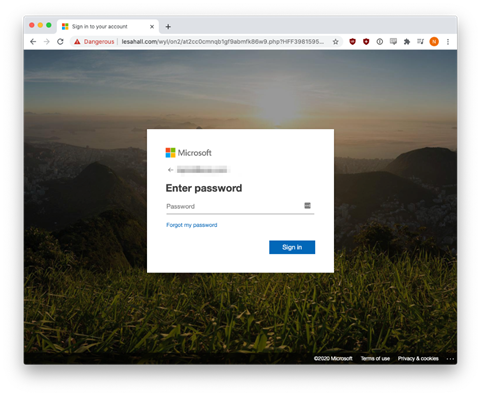
If the victim entered login credentials, that data is directly emailed to the hacker or stored on a compromised server. These fake login pages look very convincing because hackers simply copy and paste real source code from Microsoft.
Sadly, as you’ll see in a minute, these Zoom impersonating cybercriminals are hard at work in every corner of the world. But before we wrap up with a story with some more Zoom impersonation phishing examples, we’d be remiss if we didn’t remind every reader about the importance of protecting your employees and your company from the perils of email phishing. While it may be easy to think it could never happen to you, the more than $4.2 billion in losses to individuals and businesses in 2020 says otherwise.2 Fortunately, when it comes to email phishing, INKY seeks everything. We are well poised to protect your best interests and we’re only a phone call and a demonstration away.
On that note, here are just a few more examples of the Zoom phishing emails INKY has caught.
 Country of origin: Australia
Country of origin: Australia
Attack mechanism: Malicious link
Country of origin: Germany
Attack mechanism: Malicious link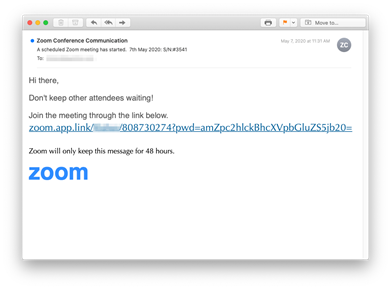
Country of origin: Hong Kong
Attack mechanism: Malicious link
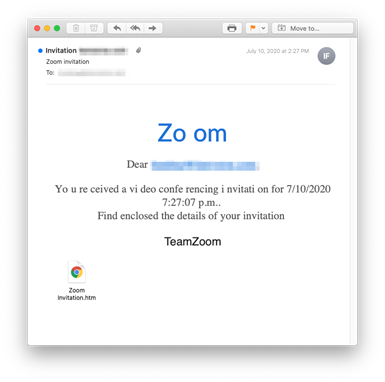
Country of origin: United States
Attack mechanism: HTM attachment
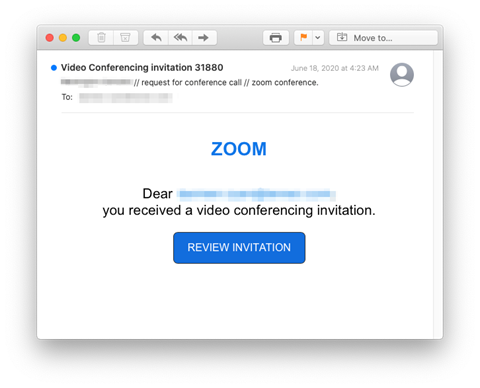
Country of origin: United States
Attack mechanism: Malicious link
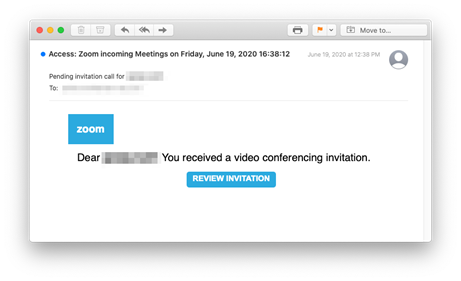 Country of origin: Spain
Country of origin: Spain
Attack mechanism: Malicious link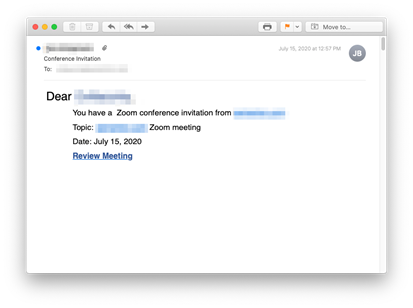
Country of origin: Australia
Attack mechanism: Malicious link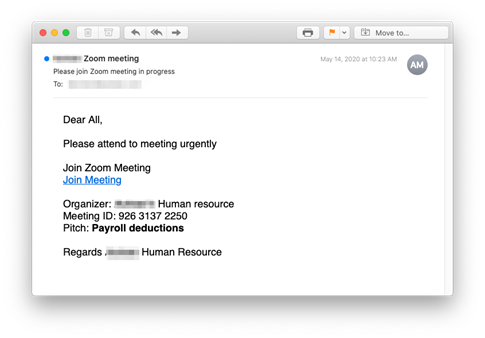
Country of origin: South Korea
Attack mechanism: Malicious link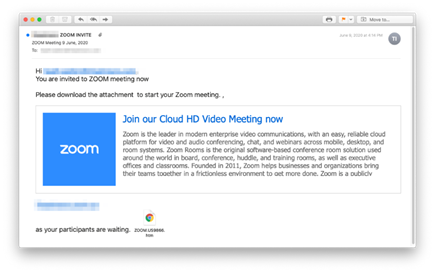
Country of origin: United States
Attack mechanism: Malicious HTM attachment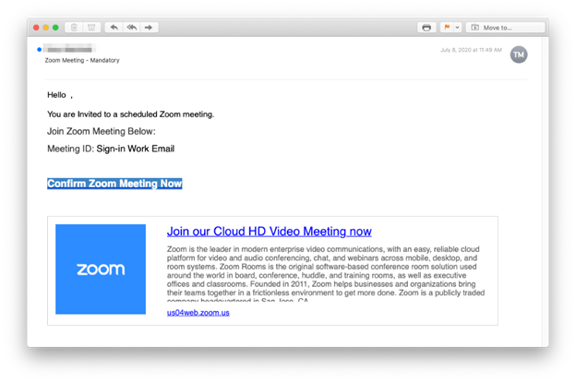
Country of origin: Finland
Attack mechanism: Malicious link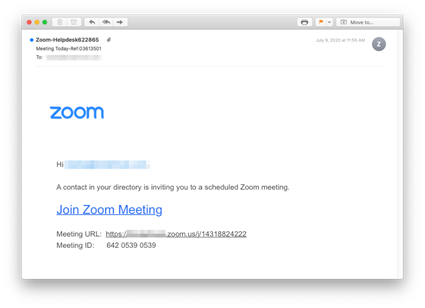
Country of origin: United States
Attack mechanism: Malicious link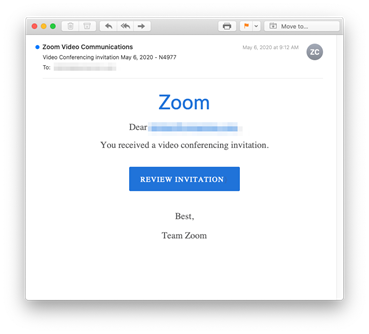
Country of origin: Germany
Attack mechanism: Malicious link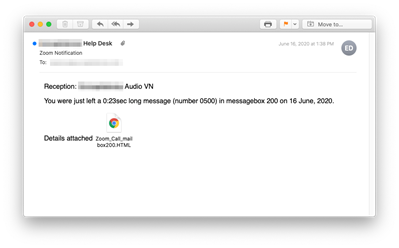
Country of origin: Germany
Attack mechanism: Malicious HTML
Interested in taking an in-depth look at how INKY works? Request a demo today.
----------------------
INKY® is the most effective hero in the war against phishing. An award-winning cloud-based email security solution, INKY® prevents the most complex phishing threats from disrupting or even immobilizing your company’s day-to-day business operations. Using computer vision, artificial intelligence, and machine learning, INKY® is the smartest investment you can make in the security of your organization. INKY® is a proud winner of the NYCx Cybersecurity Moonshot Challenge and a finalist in the 2020 RSAC Innovation Sandbox Competition. Learn more about INKY® or request an online demonstration today.
1Source: https://www.businessofapps.com/data/zoom-statistics/
2Source: https://www.ic3.gov/Media/PDF/AnnualReport/2020_IC3Report.pdf



