July 13, 2022
INKY data analysts recently detected a new variant of the tried-and-true phone scam. This time, the perps abused QuickBooks, an accounting software package used primarily by small business and midmarket customers who lack in-house expertise in finance and accounting. QuickBooks is a core offering of Intuit, which fields a range of digital financial products.
All versions of QuickBooks have the ability to send invoices, and in this case, the bad guys turned this capability into an attack vector for a low-tech phone scam. In the past year, phone scams have been on the rise as phishers respond to the increasing sophistication of anti-phishing defenses: defenders go high, phishers go low. A simple mechanism is a phone number that the phishers want the mark to call. When they do, an operative will try to extract valuable information from them.
INKY began to see instances of this particular attack in December 2021. They accelerated significantly in March 2022. Although we have detected 2,272 to date, that number is surely an undercount. The exact count is difficult to determine since the subtle scam emails and legitimate QuickBook notifications all originate from the real QuickBooks notification site: quickbooks@notification.intuit[.]com.
Quick Take: Attack Flow Overview
- Type: phishing
- Vector: a legitimate email notification from QuickBooks
- Payload: a phone number in the email
- Techniques: brand impersonation, credential harvesting, voice phishing (vishing)
- Platform: Google Workspace and Microsoft 365
- Target: Google Workspace and Microsoft 365 users
The Attack
Between December 2021 and the present, INKY detected thousands of legitimate QuickBooks notifications that were impersonating retail brands in voice phishing (vishing) attacks.
These attacks were highly effective at evading detection because they were identical to non-fraudulent QuickBooks notifications, even when examining the emails’ raw HTML files closely. All notifications originated from authentic Intuit IP addresses, passed email authentication (SPF and DKIM) tests for intuit[.]com, and only contained high-reputation intuit[.]com URLs.
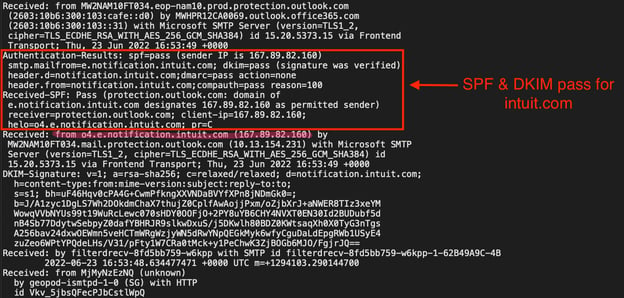
Under the hood, the authentication looked good
QuickBooks offers free trials for 30 days. Bad actors created free accounts and sent fraudulent invoices from QuickBooks.
Our analysis turned up the following impersonated brands:
- Amazon
- Apple
- Best Buy (and Geek Squad)
- PayPal
- Norton
- McAfee
In these scams, a recipient was presented with an invoice or order confirmation indicating that their credit card had already been charged and that if they wished to dispute the charge, they should contact the phone number in the email. Once a victim called, a scammer attempted to extract information (login credentials, credit card info, other personally identifiable information) or directed them to a spoofed site to extract it.
Below are two firsthand victim accounts of successful exploits, found on the Better Business Bureau’s Scam Tracker:
“When I called them, they requested that I go to the website (refund7860[.]webs[.]com), where they requested all the bank information or Paypal account information.”
“I called the number on the email to say I did not order it. To resolve this, I was supposed to purchase an Amazon security card at Safeway (or other stores) and the money would be refunded to me. They stayed on the line as I went to make the purchase. (Feeling stupid). Since the store didn't have the right card (haha), I was to purchase an Apple gift card. When I got into the parking lot, I read the number to the person. $500!!. They said they credited my account.”
In other cases, the operative claimed that they needed remote access to the victim’s computer to resolve the issue.
This example from late April claims to be an Amazon Prime shipping notification with $1,013.88 due. Phishers used the strings “amazn” and “amzn” to evade detection filters.

Not from Amazon
If the target clicked on the big black button that said “Print or save,” they were taken to intuit.com, where bad actors had created a fraudulent invoice.
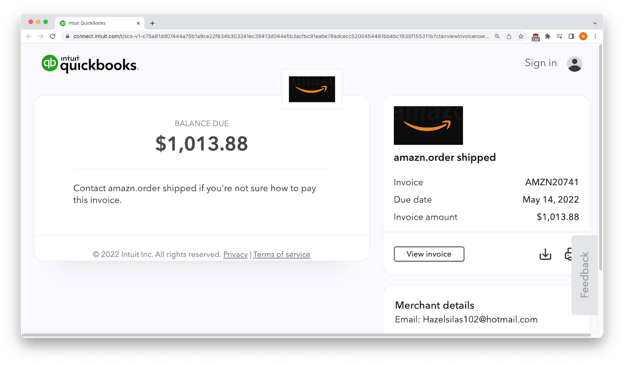
Real QuickBooks; fake invoice
If the victim then clicked on the “View invoice” button, they were shown more details about this fake purchase.
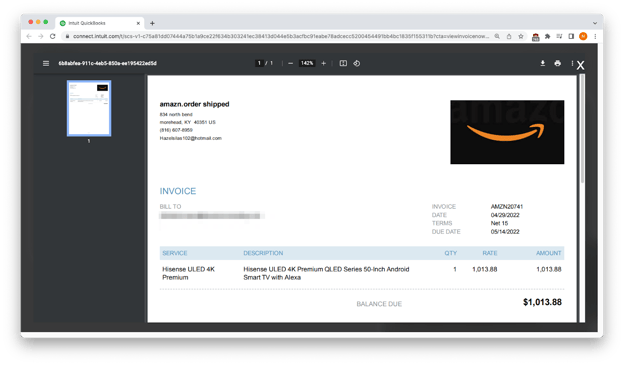
Lots of detail is not necessarily an indication of legitimacy
The effectiveness of these techniques relies on the panic a victim might feel if they received an invoice for goods or services that they did not purchase. The emotional reaction to notification of this sort can be strong and may impair judgment. The natural response is to get right on the phone and try to back the order out or find a way to obtain a refund. The phishers take advantage of this disrupted emotional state to extract personal or financial information before the victim realizes that something is off.
Recap of Techniques
- Brand impersonation — uses elements of a well-known brand to make an email look as if it came from that company
- Vishing — impersonates a brand to steal information via a phone call
- Threat of financial loss — creates cognitive dissonance in the mind of the recipient, who may be disoriented enough by the message to miss small discrepancies that could tip them off to the fraud
- Time pressure — adds a sense of urgency to the potential loss, again steering the target away from doing a common-sense analysis of the situation
Best Practices: Guidance and Recommendations
Recipients of such notifications should always be cautious of requests for payment in the form of gift cards. Real businesses do not use this method of transfer, which is essentially like cash and expensive to trace.
It is unwise to call any phone number given in an unsolicited email. Anyone wishing to call a company should use the number on the firm’s official site.
No one should give sensitive information over the phone to an unknown party.
In this situation, remote access to the recipient’s device should not be granted, as it is not needed to receive a refund or rectify an issue.
If there is any doubt about a charge, it is best to contact the relevant credit card company to see if there really is a charge in that amount. Any real charge would be shown as “pending.”
Ready to see INKY in action? Start a free trial or schedule a demo today.
----------------------
INKY is an award-winning, behavioral email security platform that blocks threats, prevents data leaks, and coaches users to make smart decisions. Like a security coach, it signals suspicious behaviors with interactive banners that guide users to take safe action on any device or email client. IT teams don’t face the burden of filtering every email themselves or maintaining multiple systems. Through powerful technology and intuitive user engagement, INKY keeps bad actors out for good. Learn more about INKY™ or request an online demonstration today.


