Kidnapping your files and data and then holding it hostage until a ransom is paid. That pretty much sums up your basic ransomware attack, the effects of which can be devastating.
In many cases, if the ransom is not paid, the victim’s data remains inaccessible. To further motivate a victim to pay the ransom, the hacker might also threaten to destroy the files or release them to the public. This poses an even bigger problem for companies who hold sensitive data as part of their everyday operations, such as healthcare companies and financial institutions.
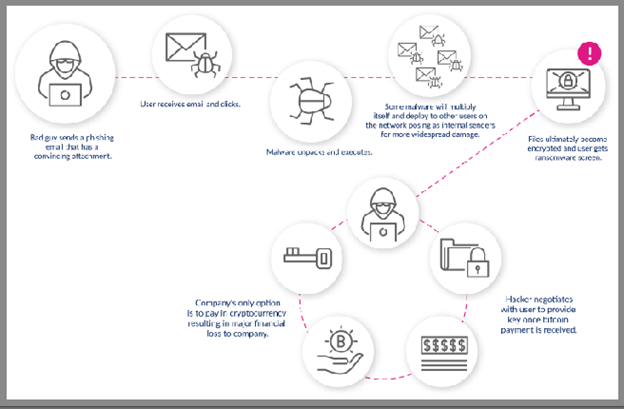
If you’re wondering exactly how these heinous attacks are perpetrated, consider the anatomy of a ransomware attack.
Step 1. The cybercriminal sends a very convincing phishing email to an employee which contains an attachment they need to open.
Step 2. The unsuspecting employee makes one fatal click of the mouse.
Step 3. The malware unpacks and executes. In many cases, the malware is programmed to multiply itself, pose as a colleague (which can look like a CEO impersonation, business email compromise (BEC), or account takeover) and do additional damage.
Step 4. Company files become encrypted. This means only the hacker can access them and they can’t be fixed by using a mathematical key known only by the attacker.
Step 5. The company then must make the hard decision whether or not to pay the expensive ransom. This is done with difficult-to-trace cryptocurrency.
Step 6. If the ransom is paid, the files can be decrypted using the key provided by the cybercriminal.
No matter how much ransom you agree to pay there is no guarantee your files will be returned. After all, you’re dealing with criminals. So, what should you do? The FBI urges all organizations who are victims of a ransomware attack to report it to the FBI’s Internet Crime Complaint Center (IC3). Their investigators are your best bet when it comes to tracking down cybercriminals. They’ll attempt to identify the hackers responsible for the ransomware attack, recover your ransom, hold the cyber thieves accountable under U.S. law.
Of course, that will not keep you safe from the next ransomware or other cyber threats. To do that, you need to protect your business around the clock with the type of email security software that recognizes and stops ransomware attacks from happening in the first place.
INKY provides the most comprehensive email phishing protection available – capable of stopping malware and ransomware before it has the opportunity to fool your employees into making that one fatal click that can bring your business to an end. How? INKY scans every sent and delivered email automatically and flags malicious emails, protecting you from even the most complex threats. INKY’s intelligent machine learning algorithms identify abnormalities in emails, even if the threat has never been seen before. INKY’s Banner warns employees of threats while protecting and training them at the same time.
Installation is simple too. INKY is compatible with just about every email platform and our installation team has most customers are up and running in under an hour – even with remote employees. Do your part to prevent a ransomware attack by scheduling a demo or inquiring today.
INKY® is the most effective hero in the war against phishing. An award-winning cloud-based email security solution, INKY® prevents the most complex phishing threats from disrupting or even immobilizing your company’s day-to-day business operations. Using computer vision, artificial intelligence, and machine learning, INKY® is the smartest investment you can make in the security of your organization. INKY® is a proud winner of the NYCx Cybersecurity Moonshot Challenge and a finalist in the 2020 RSAC Innovation Sandbox Competition. Learn more about INKY® or request an online demonstration today.



