This holiday shopping season, two trends are converging that have forced phishers to shift tactics.
- Improved anti-phishing technology has become more effective at warding off even the most sophisticated attacks, and
- People anxious about the approaching holiday shopping season are increasingly dependent on the online channel to buy big ticket items.
In this environment, some phishers have moved their technical approach down market. New campaigns are eschewing pyrotechnics for an approach that the black hats hope will be innocuous enough to slip beneath the defenders’ radar.
INKY data scientists began to see a run of these attacks toward the end of summer, and soon thereafter INKY engineers created a new threat model called Phone Scam to capture these attempts. Their volume has only been increasing going into the holidays. They present such a minimalist surface that they could easily evade a detection system not on the lookout for them.
The essential nature of a phone scam email is that it is a plain note from what appears to be a legitimate source, with no suspicious links or malware attachments, featuring a simple pitch and a phone number.
The target is supposed to be convinced by the pitch to call the number. At the other end of the line, someone working for the phishers tries to extract information from the caller.
Just in time for the holidays, phishers are cranking up their phone scams to fit the spirit of the season. They are impersonating a wide variety of consumer brands — including Amazon, eBay, PayPal, and Target — and sending messages designed to induce anxiety in recipients and cause them to react irrationally, setting them up to give over precious credentials.
Quick Takes: Attack Flow Overview
- Type: Phishing
- Vector: Email to phone
- Payload: Potential credential extraction over the phone
- Techniques: Brand impersonation
- Platform: Google Workspace and Microsoft 365
- Target: Google Workspace and Microsoft 365 users
The Attack
During the summer of 2021, INKY began to see a new type of threat: emails that impersonate retail brands but contain no malicious links or attachments. This change in threat mix induced INKY engineers to create a new threat model — Phone Scam — which was deployed in the product in July. In the four months since the rollout of the Phone Scam threat model, INKY has detected 24,275 of these attacks among its customers. Their prevalence is increasing going into the holidays.
This holiday season, anyone with an email address, whether they shop online or not, could receive a fake order confirmation that impersonates a retail company (e.g., Amazon, PayPal, Walmart). These emails, which instruct the recipient to call a phone number if they want to dispute a charge or resolve a fake issue, are structured around a phony order, often for an expensive item.
Because the majority of these attacks emanate from free-mail services (e.g., Gmail, Hotmail, iCloud), which have high sender reputations, they are able to pass email authentication (SPF, DKIM, DMARC).
When a reputable company like Amazon supposedly sends a note like the one below saying it’s about to ship a pricey piece of equipment that wasn't ordered, it’s enough to send anybody into a panic.
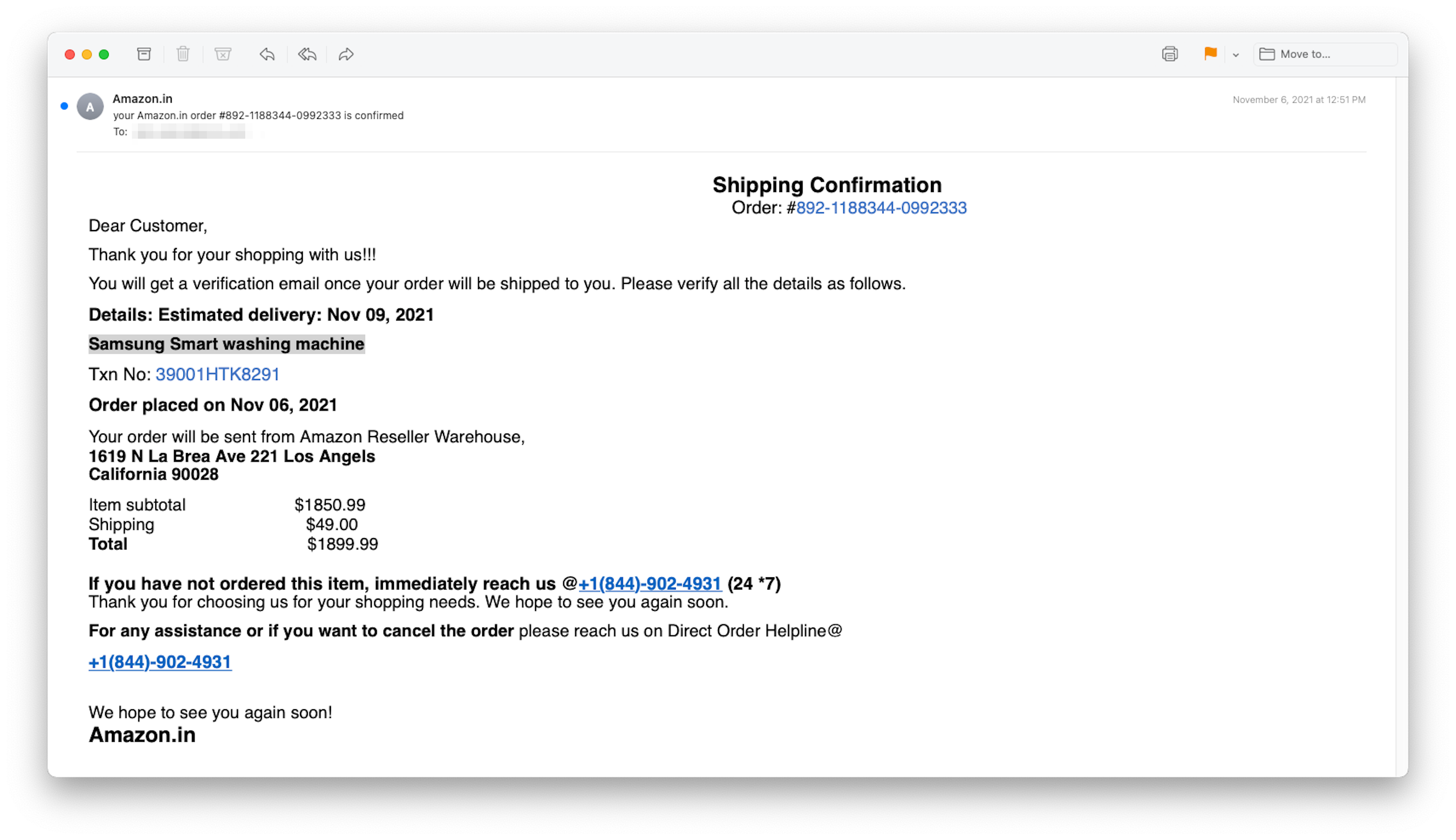
Wait! I never ordered a Samsung washing machine from Amazon! Better call that number!
This one has a bit more formatting, mimicking a cross between a UPS shipment notification and a real Amazon order. Phishers craft their fake orders using high-priced items, in this case an Apple Macintosh computer, hoping to induce in their mark a fear of financial loss and trigger a panic that will affect the target’s judgment.
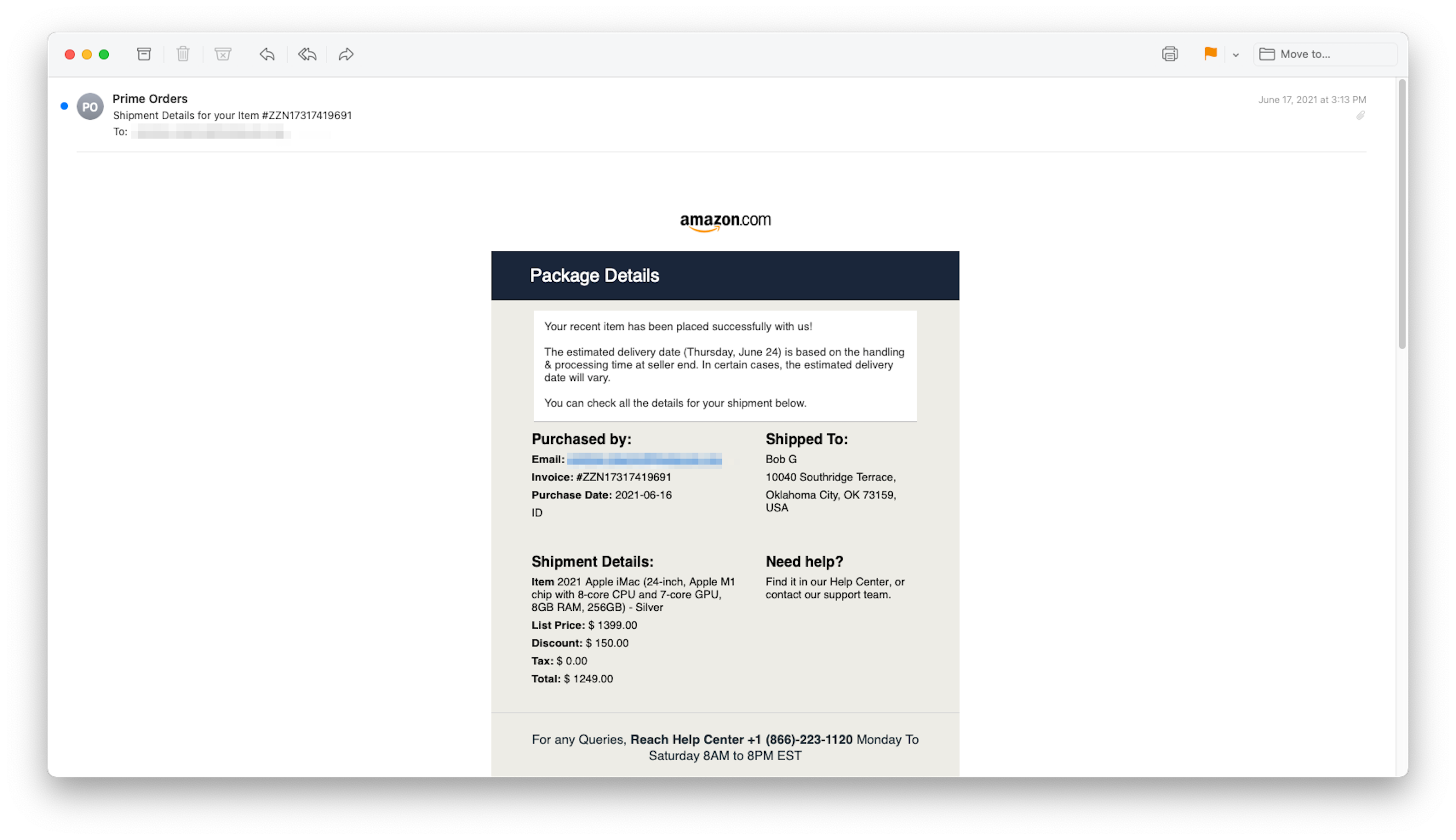
Nice of Amazon to confirm that Apple Mac shipment, but we’re a Microsoft Windows shop!
Then, there are the payment processors, in this case PayPal. A realistic logo indicates the email might have come from PayPal. But the recipient never ordered a purple 64GB Apple iPhone 11. The impersonation of well-known brands is one way phishers hope to gain their target's trust.
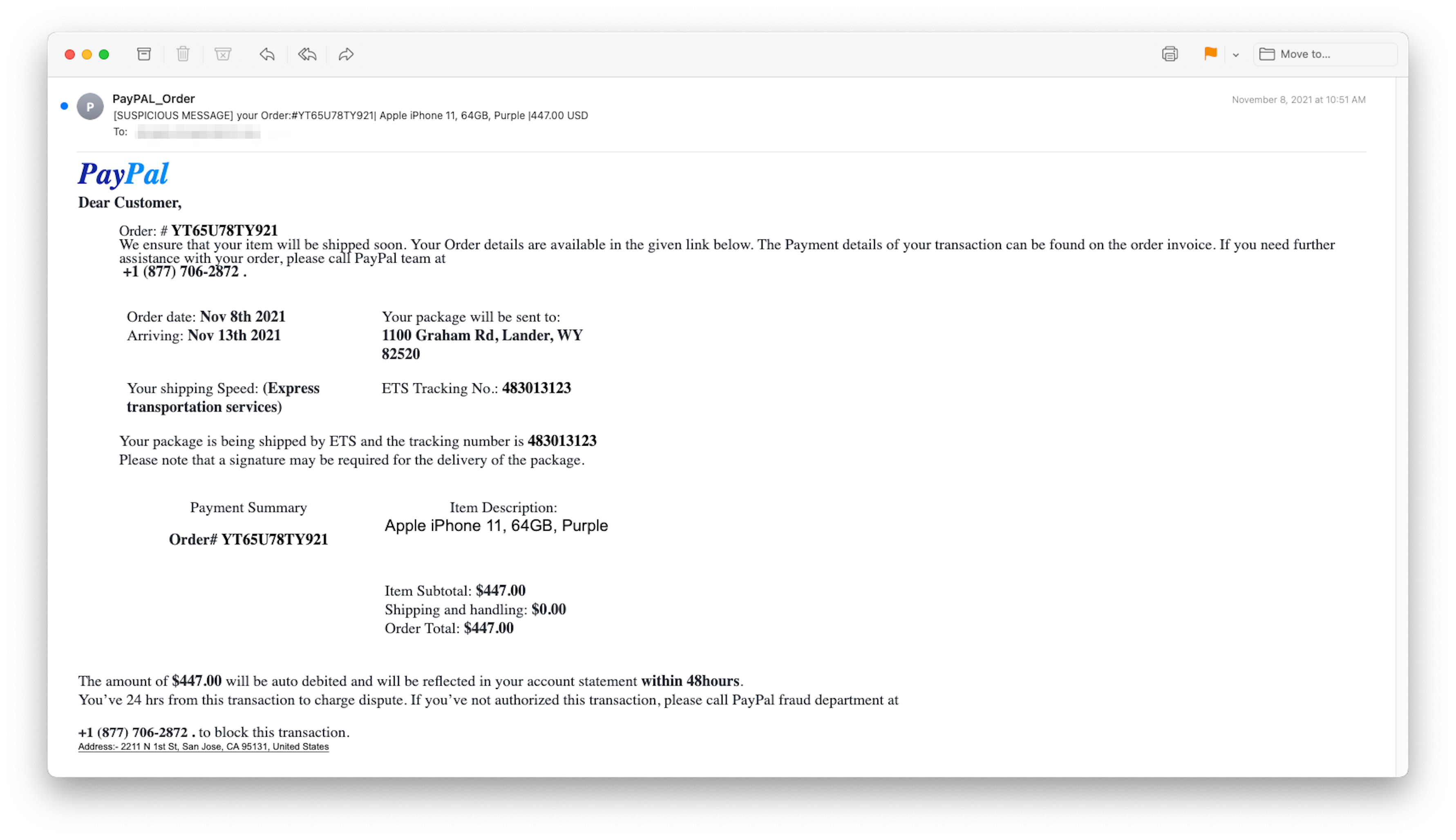
This email did not come from PayPal
Someone may have placed an order with Target for a 40” Vizio HDTV, but not the recipient of this email. The order details are concrete, but bogus. Naturally, the first thing the recipient would think to do is call the number to “block this transaction,” as the helpful instructions indicate.
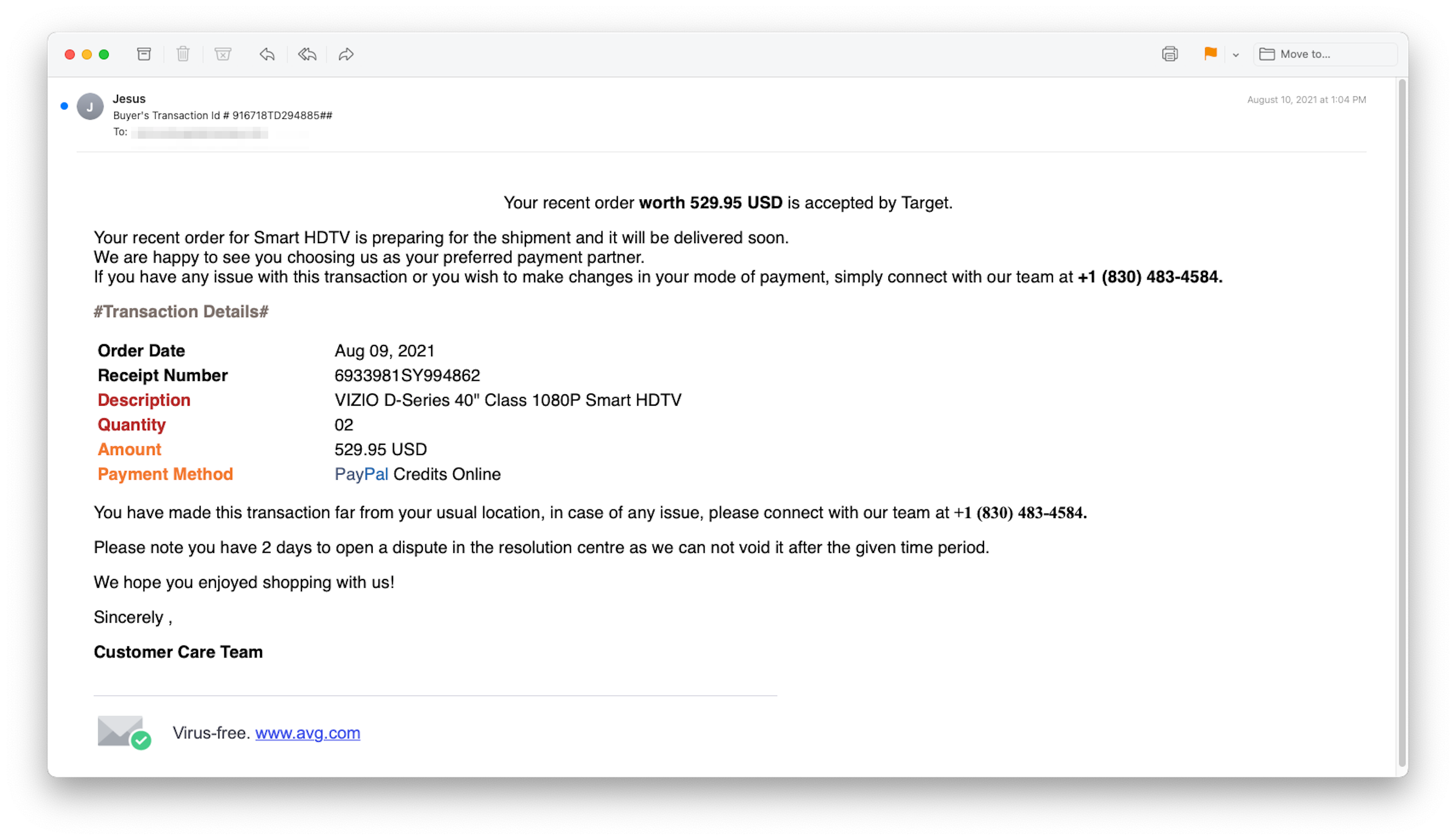
Fake Target payment confirmation for a television
Here’s an interesting one: a fake PayPal confirmation for a firearm order. Apparently, the PayPal-gunsmith connection is not new. This particular configuration of fraud elements has been around for more than a year.
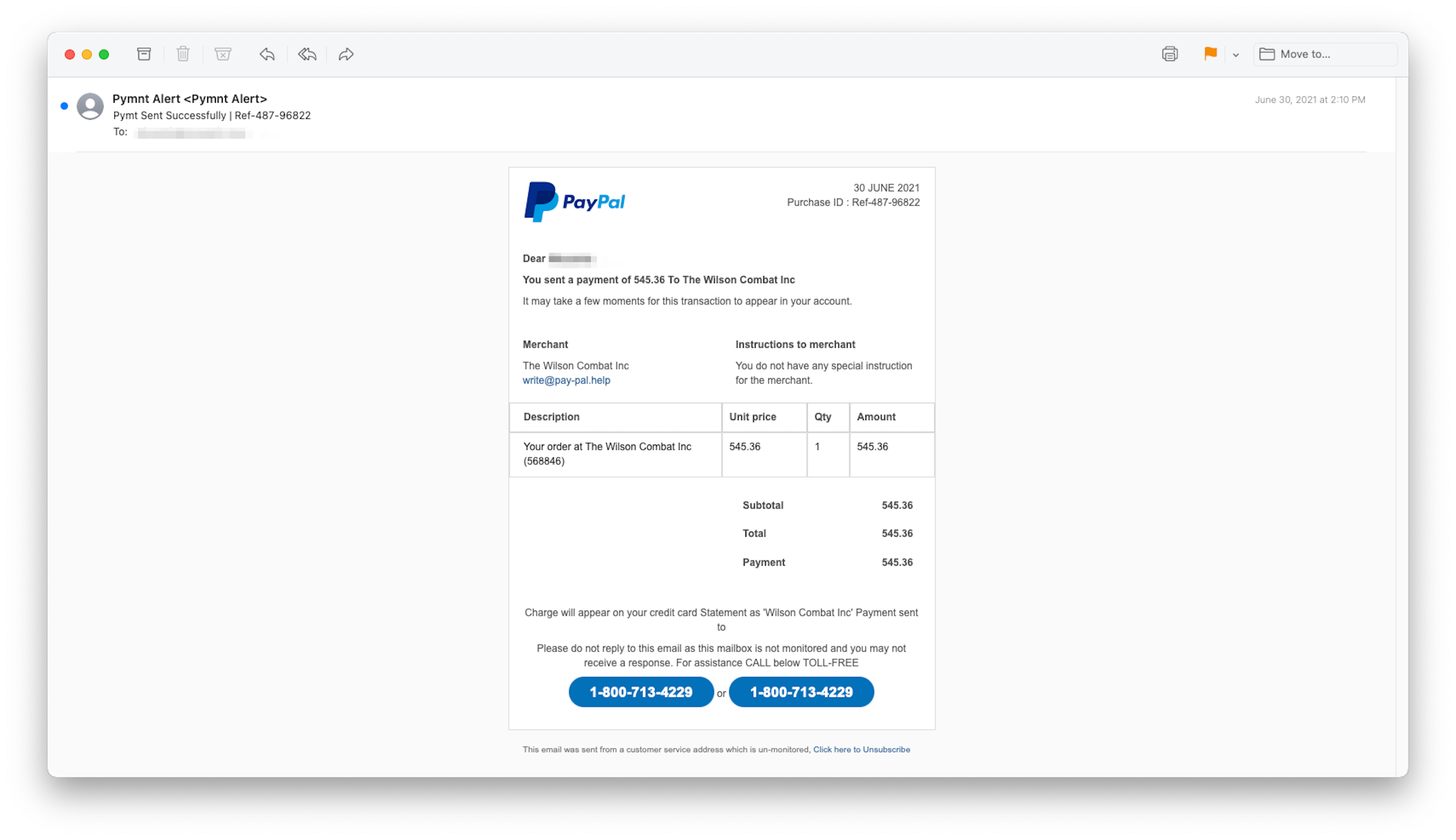 The logo may be PayPal’s, but the email did not originate from one of the payment processors’ servers
The logo may be PayPal’s, but the email did not originate from one of the payment processors’ servers
This one looks like it comes from eBay, but even the friendly name looks funny: e-B.a.y. And is there any such thing as a Dell Latitude Business Gaming Laptop? Dell does sell its Latitude brand to businesses, and it does have a high-end gaming lineup called Alienware and a more modestly priced one called the G Series, but Latitudes and gaming notebooks are sold to two entirely different audiences. However, a panicking recipient of this message might not notice those small discrepancies.
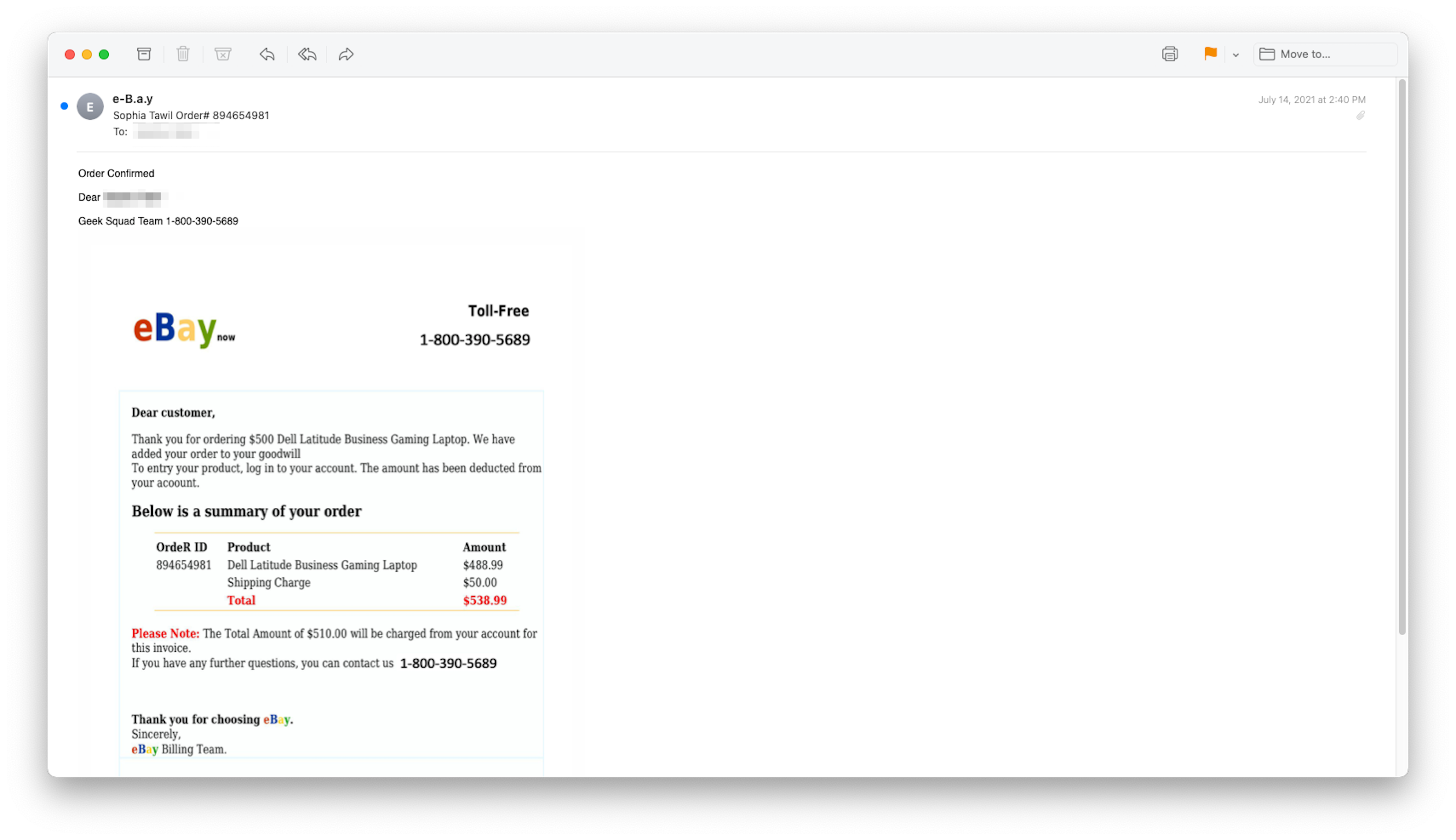
Fake eBay order confirmation for a non-existent Dell notebook
Techniques
These phishing attempts were designed to fly under the radar. They have no links or attachments. So, there’s nothing to detect. Threat intelligence feeds, which are the first line of defense for many anti-phishing packages, will never list these emails as dangerous.
Because the majority of these attacks emanate from free-mail services (e.g., Gmail, Hotmail, iCloud), which have high sender reputations, they are able to pass email authentication (SPF, DKIM, DMARC).
Of the 24,275 Phone Scam emails that INKY detected from June through November, the vast majority — 21,017 — were sent from Gmail accounts.
Logarithmic Scale
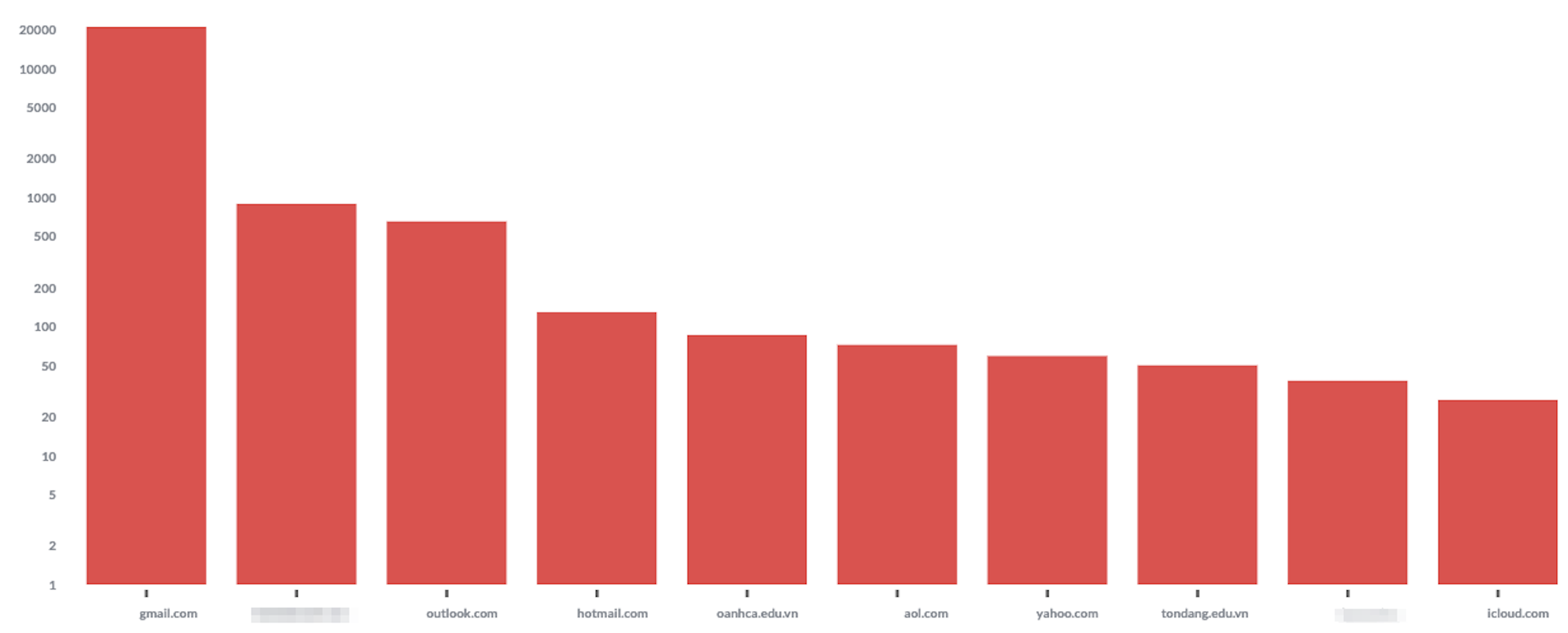
Number of email attacks detected during the sample period, by sender domain (logarithmic scale)
Recap of Techniques
- Brand impersonation — uses brand elements in phishing emails and a malicious site, which also impersonated Microsoft brand elements
- Threat of financial loss — creates a cognitive dissonance in the mind of the recipient, who may be disoriented enough by the message to miss small discrepancies that could tip them off to the fraud
- Time pressure — adds a sense of urgency to the potential loss, again steering the target away from doing a common-sense analysis of the situation
Best Practices: Guidance and Recommendations
Fortunately, there are a number of simple things recipients can do (aside from adopting modern anti-phishing software) to stay safe.
It’s easy enough to take a closer look at a sender’s email address to confirm that the message comes from the branded company that seems to be sending it. Particularly when an email triggers a sense of dread and urgency, looking at the sender’s address can quickly put those fears to rest.
Even if the recipient makes the phone call to the fake sender, it is critical never to give sensitive personal information (e.g., banking information, social security number, date of birth) over the phone.
And just thinking for a minute before responding can reveal that the pitch makes no real sense. For example, one doesn’t resolve an accidental or fraudulent charge by buying a gift card.
And then there’s the simple remedy of just typing the retail web site directly into a browser, going to the real website, and viewing order history, which will likely not include the one referenced in the fraudulent email.
Read more of INKY’s past Fresh Phish, and subscribe to receive our news and articles directly to your inbox.
About INKY
Headquartered in College Park, Maryland, INKY leads the industry in mail protection powered by unique computer vision, artificial intelligence, and machine learning. The company’s flagship product, INKY Phish Fence, uses these novel techniques to “see” each email much like a human does, to block phishing attacks that get through every other system. INKY founder Dave Baggett also co-founded ITA Software, the industry-leading airfare search company purchased by Google in 2011 for $730M, which now powers Google Flights®. For more information, please visit INKY.com/.


