Coronavirus cybercriminals have sunken to an all-time low. Not only are they devising phishing scams during a pandemic that has us all on edge, now they’re using the economic stimulus package as phishing bait.
What’s at Stake?
In case you’re not aware, as part of the CARES Act, Congress passed a $2 trillion bill to help individuals and business affected by the financial implications that have come with the COVID-19 pandemic. The bill includes a provision whereby many Americans will receive a one-time Economic Impact Payment from the federal government. If you filed your 2018 or 2019 taxes, the money will arrive via direct-deposit from the U.S. Treasury Department, using the banking information currently on file from your taxes. Those without direct deposit information on file with the IRS will receive a paper check in the mail.
More than 80 million Americans will begin receiving direct deposits the week of April 13, 2020 and another 101 million are scheduled to receive paper checks…unless the IRS receives their banking information beforehand.1 That adds up to an extraordinary amount of opportunity for hackers, including the well-planned one that INKY caught.
Sophisticated Phish
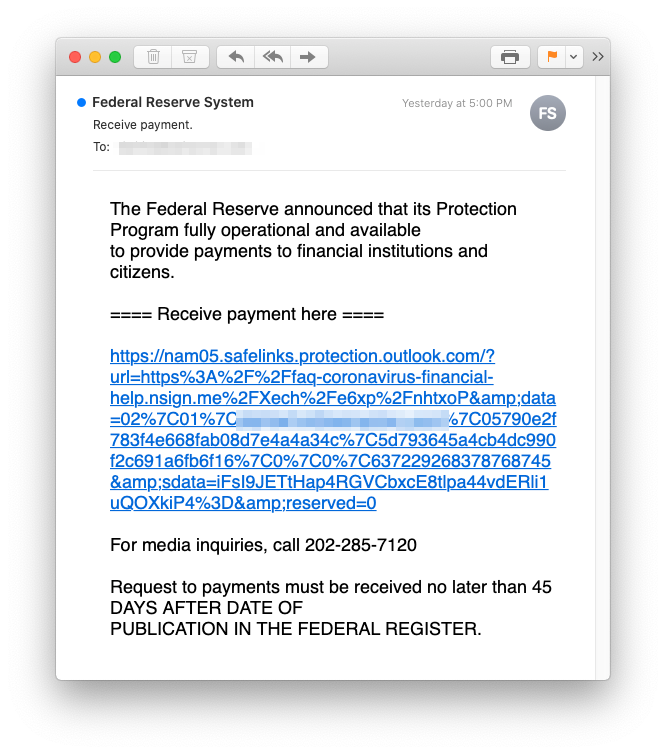
Though INKY caught and exposed this phishing threat, we’re the first to admit that it’s one of the most sophisticated email phishing examples we’ve seen in a while. What makes this catch so impressive? These cybercriminals went to great lengths engineering and then fabricating the many convincing elements required to steal recipients’ banking credentials. The designers behind this cyber-scheme went to the trouble of:
- Purchasing a seemingly-convincing URL for their endeavor: faq-coronavirus-financial-help.nsign.me
- Posing as the U.S. Federal Reserve
- Designing a very convincing website that even speaks to financial assistance
- Listing top “participating” banking institutions complete with real logos
- Impersonating the U.S. Paycheck Protection Program, FEMA, and the CDC
- Pretending to also handle media inquiries (using a phone number that actually goes to a voicemail recording that is in Spanish)
- Incorporating Coronavirus graphics into the website design
- Replicating the FAQ found on the actual IRS Economic Impact Payments website
Would one of your employees have fallen for this elaborate phishing scam?
It began with an email that looks like this:
Download full report
Interestingly enough, the company that received this email also uses Microsoft’s ATP scanning system as a first line of defense against phishing. Unfortunately, this phishing email slipped right though and into the eagerly awaiting INKY Phish Fence.
INKY sees things other email security services do not. In this case, a zero-day phishing attack was foiled, showing once again how INKY protects its customers – and maybe even democracy – from phishing attacks.
Read the full report to learn more about this phishing scam entitled Exploiting a Pandemic: Coronavirus Stimulus Package Economic Impact Payments. Or, contact us directly to see how we can keep your company safe from phishing threats like this and request a free demonstration of our product.
----------------------
INKY® is the emerging hero in the war against phishing. An award-winning cloud-based email security solution, INKY® prevents the most complex phishing threats from disrupting or even immobilizing your company’s day-to-day business operations. Using computer vision, artificial intelligence, and machine learning, INKY® is the smartest investment you can make in the security of your organization. INKY® is a proud winner of the NYCx Cybersecurity Moonshot Challenge and finalist in the 2020 RSAC Innovation Sandbox Competition. Learn more about INKY® or request an online demonstration today.



