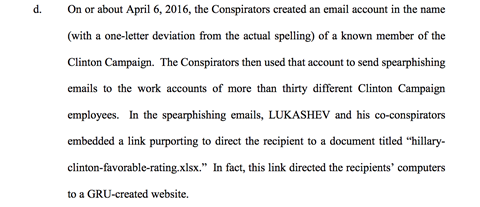
The recent indictment by the U.S. Department of Justice spelled out exactly how targeted phishing attacks, also known as spear phishing, worked to expose confidential information from the Hillary Clinton Campaign in 2016. Here is an excerpt of page 7:
Let’s unpack what happened here:
|
THE PHISHING ATTACK |
INKY RESPONSE |
|
"The Conspirators created an email account in the name (with a one-letter deviation from the actual spelling) of a known member of the Clinton Campaign."
|
We see this all the time. Attackers create a fake email account that looks similar to actual accounts by varying one letter or substituting a unicode character for a letter in the real email address.
|
|
"The Conspirators then used that account to send spear phishing emails to the work accounts of more than thirty different Clinton Campaign employees." |
We see this too, where the attackers send an email from the fraudulent email address to many people. They hope that at least one person opens the attachment, and it doesn't take much effort to send an email to a lot of people. In this case, the fake email was sent to 30 people. |
|
"In the spear phishing emails, LUKASHEV and his co-conspirators embedded a link purporting to direct the recipient to a document titled “hillaryclinton-favorable-rating.xlsx.” In fact, this link directed the recipients’ computers to a GRU-created website." |
To get at least one targeted person to open the email, attackers offer something with a benign title that will likely be clicked. In this case, it was a document titled, “hillaryclinton-favorable-rating.xlsx.”
|
So how can an organization protect itself from attacks like this?
Inky Phish Fence can help. Inky Phish Fence is a secure email gateway that protects users by building sender profiles for each user. These sender profiles "train" Inky Phish Fence to spot anomalies., e.g., email purporting to be from one person but is sent from a different email address than the user usually receives from that person. Inky Phish Fence would display a prominent warning on top of the message that explains why it thinks an email is suspicious.
INKY also warns that this is an email from a "first time sender" if INKY has not seen this email address write to this user before. It is cause for concern if an email that you believed to be from a frequent contact got marked as a "first time sender" by INKY. Often, a scammer will include a familiar display name, but the hidden email address is actually different than the one you expect.
This are just some of the warnings and protections INKY provides.




