A picture is worth a thousand words. But a screengrab could be worth a whole lot more.
That’s the sentiment coming from the latest group of hackers who were caught using a clever image-based phishing scam that has left most email security systems baffled.
Painting the Picture
New phishing tactics develop faster than a Polaroid print. As soon as one phishing scam becomes exposed, another is already on its way to the inboxes of unsuspecting victims. Of course, the first step in the process is often the most difficult. The hacker must get their phishing email delivered. Oftentimes, that is no easy task and requires bypassing spam filters, anti-virus software, Secure Email Gateways (SEGs), and any number of general email security programs. Like any anti-phishing solution, one of the first things they try to do is validate content. But what if the email has no content? Certainly, an email with no content can’t be dangerous, right? Well, when it comes to image-based phishing scams, that’s exactly what scammers want anti-phishing defenses to think.
Enter the Phony Phone Scam
Phone scams have become a new type of phishing threat. In short, they are brand impersonation emails that encourage the reader to contact them by phone rather than click on a link or download a file. Email recipients receive a fake order confirmation from a phisher impersonating a retail company (e.g., Amazon, PayPal, Walmart). These emails, which instruct the recipient to call a phone number if they want to dispute a charge or resolve a fake issue, are structured around a phony order, often for an expensive item. When recipients call the phone number, an operative will try to extract valuable information from them.
These phishing attempts were designed to fly under the radar. They have no links or attachments, so there’s nothing to detect. Threat intelligence feeds, which are the first line of defense for many anti-phishing packages, will never list these emails as dangerous. Additionally, because the majority of these attacks emanate from free-mail services (e.g., Gmail, Hotmail, iCloud), which have high sender reputations, they are able to pass email authentication (SPF, DKIM, DMARC).
Image-Based Phishing Meets Phone Scam
INKY has observed bad actors adopting a technique called Image-based phishing in phone scams. This is a phishing email where the textual message is embedded in an image and attached to the phishing email. Said differently, phishers craft a phishing email, turn it into an image, and send only the image to their victims. Most email clients display the image file directly to the recipient rather than delivering a blank email with an image attached. Recipients won’t know that they are looking at a screenshot instead of HTML code with text (i.e. a phishing email) and since there are no links or attachments to open the email feels safe.
What INKY Caught
The goal of Image-based phishing is to prevent anti-spam and email security scanners from analyzing an email’s text. INKY uses optical character recognition (OCR) that extracts the text from an attached email and uses it in combination with other artificial intelligence algorithms to detect an email as dangerous.
INKY detected bad actors impersonating Geek Squad in Image-based voice phishing (vishing) attacks. INKY users received an email claiming that their subscription with Geek Squad had been renewed for a year and a significant amount of money would be debited from their account within 24 hours.
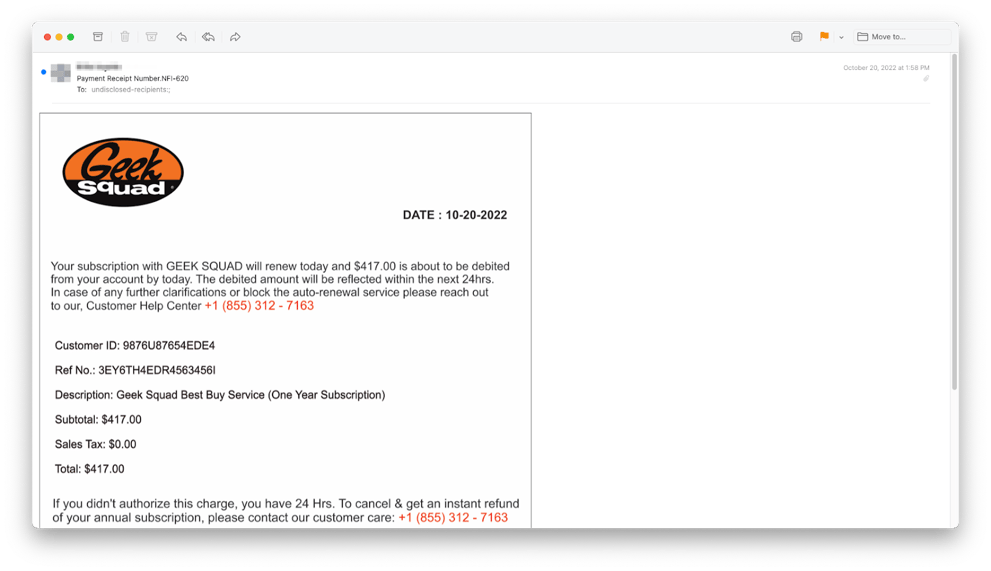
As you can see, the email client automatically displays the attached image file though what was sent was actually an empty email with an image attachment.
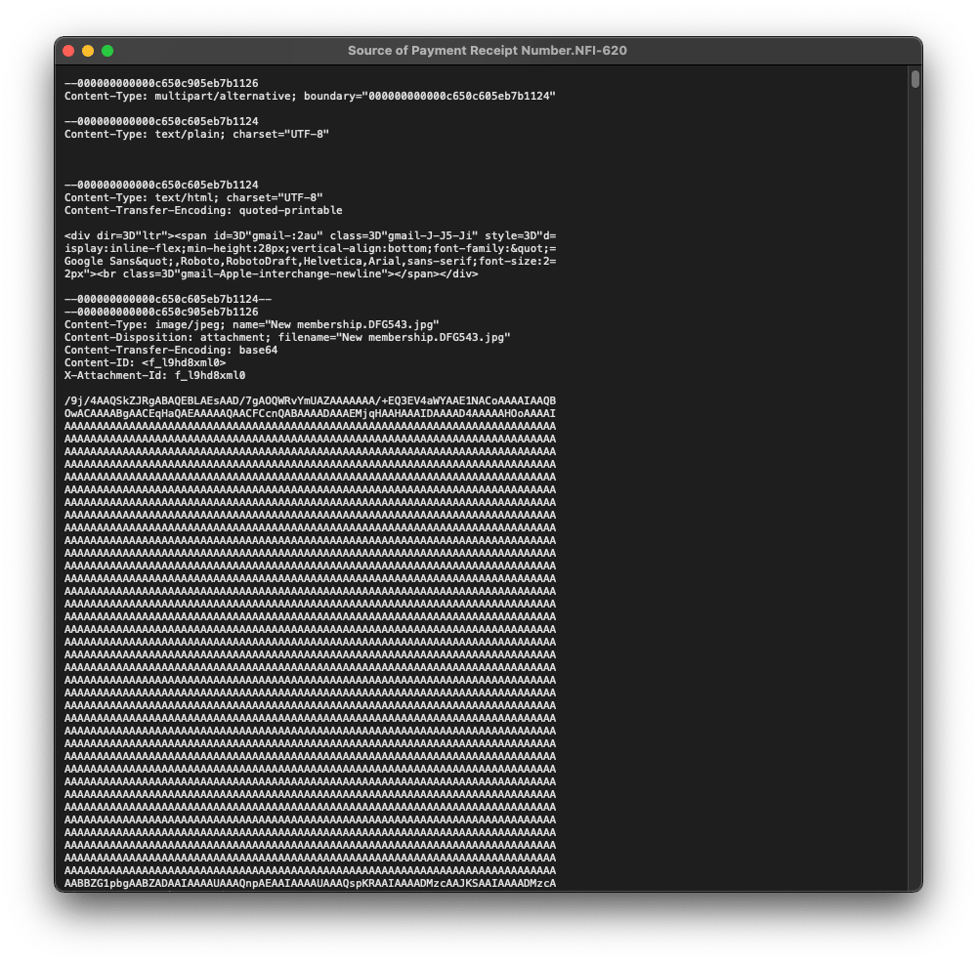
Note that the plain text and HTML versions of the email have no content for email scanners to analyze.
A Note from the Grammar Police
While phishers have a reputation for grammatically sloppy emails, it’s not always easy to notice all the signs. However, recipients with a discerning eye or who thought to visit the Geek Squad’s website for validation may have noticed:
- Geek Squad does not write its company name in all capital letters. Usually, if the logo itself is not in caps, the text in letters certainly wouldn’t be either.
- The word ‘today’ is supposed to prompt urgency and it was used two times in the first sentence. Professional or corporate writers probably would not have used the same word twice in one sentence, and a sense of urgency is always a red flag for phishing.
- “…is about to be debited by today” doesn’t read well. Is it about to be debited or will it be debited sometime today?
- The use of “24hrs” is not very professional. Using “24 hours” with a space and no abbreviation would have been better.
- The third sentence is a mess. For starters, it is missing words and doesn’t really make sense. The beginning, “In case of any further clarification or block” should likely say, “Should you need any further clarification or wish to block…”.
- There should not be a comma between “our” and “Customer Help Center.”
- Toward the end, “24 Hrs.” is used again but this time contains the proper space. There is also a capitalized H and a period in the middle of the sentence.
- Their use of an ampersand (&) is awkward.
- The top of the email says “Customer Help Center” but when reiterated at the bottom of the email they use all lower-case letters and call it by a different name – customer care.
- The phone number in the email is not the same as the one on Geek Squad’s web page.
- Geek Squad doesn’t offer an annual subscription plan for services. Rather, Geek Squad is part of Best Buy which offers an annual subscription plan known as Totaltech™. It’s $199.00 per year.1
Falling for the Phishing Email
Recipients who call the phone number listed in the email will be met with the following outcomes:
- Bad actors claim they need victims to install remote access tools on their computer to resolve the issue.
- Victims are directed to a malicious site where banking information is requested.
- Victims are asked to buy gift cards to get reimbursed for the Geek Squad charges.
The effectiveness of these techniques relies on the panic a victim might feel if they received an invoice for goods or services that they did not purchase. The emotional reaction to a notification of this sort can be strong and may impair judgment. The natural response is to get right on the phone and try to back out of the order, or, barring that, find a way to obtain a refund. The phishers take advantage of this disrupted emotional state to extract personal or financial information before the victim realizes that something is off.
A Final Word
Let’s summarize some of the tactics used in this Image-based phishing and phone scam.
Recap of Techniques
-
Brand impersonation - uses elements of a well-known brand to make an email look as if it came from that company.
-
Image-based phish - textual phish message is embedded in an image.
-
Vishing - impersonates a brand to steal information via a phone call.
-
Threat of financial loss - creates a cognitive dissonance in the mind of the recipient, who may be disoriented enough by the message to miss small discrepancies that could tip them off to the fraud.
-
Time pressure - adds a sense of urgency to the potential loss, again steering the target away from doing a common-sense analysis of the situation.
Best Practices: Guidance and Recommendations
-
Trusted brands will never contact you asking you for personal information or payment related to a support issue unless you have previously engaged them.
-
Recipients of such notifications should always be cautious of requests for payment in the form of gift cards. Real businesses do not use this method of transfer, which is essentially like cash and expensive to trace.
-
It is unwise to call any phone number given in an unsolicited email. Anyone wishing to call a company should use the number on the firm’s official site.
-
No one should give sensitive information over the phone, particularly to an unknown party.
-
In this situation, remote access to the recipient’s device should not be granted, as it is not needed to receive a refund or rectify an issue.
-
If there is any doubt about a charge, it is best to contact the relevant credit card company to see if there really is a charge in that amount. Any real charge would be shown as “pending.”
Given today’s economy it’s especially understandable that someone would quickly react to an unauthorized bank withdrawal. So, imagine if this same type of phishing scam was delivered to your Accounts Payable department. It only takes one frazzled employee to set in motion a chain of events that could effectively drain the company bank account.
INKY is the behavioral email security platform that blocks threats, prevents data leaks, and coaches users to make smart decisions regarding the safety of their email. Like a cybersecurity coach, it signals suspicious behaviors with interactive banners that guide users to take safe action on any device or email client. IT teams don’t face the burden of filtering every email themselves or maintaining multiple systems. Through powerful technology and intuitive user engagement, INKY keeps bad actors out for good. Start a free trial or schedule a demo today.
----------------------
INKY is an award-winning, behavioral email security platform that blocks phishing threats, prevents data leaks, and coaches users to make smart decisions. Like a cybersecurity coach, INKY signals suspicious behaviors with interactive email banners that guide users to take safe action on any device or email client. IT teams don’t face the burden of filtering every email themselves or maintaining multiple systems. Through powerful technology and intuitive user engagement, INKY keeps phishers out for good. Learn why so many companies trust the security of their email to INKY. Request an online demonstration today.
1Source: https://www.bestbuy.com/site/electronics/totaltech/pcmcat1629315977983.c?id=pcmcat1629315977983


