Have you signed up for ChatGPT yet? It’s quite possible, especially considering the new controversial language generator reached 1 billion users in March 2023. With that amount of interest, it’s no wonder cybercriminals have begun impersonating the brand in a sophisticated personalized phishing campaign.
What is ChatGPT and What Can It Do?
In case you’re a newcomer or need a refresher, ChatGPT stands for “Chat Generative Pre-trained Transformer” and is a natural language processing tool that can understand text and language and also generate human-like content and conversation on a wide range of topics. ChatGPT was developed by the tech firm OpenAI, and is capable of composing essays, translating text, having philosophical conversations, writing and fixing code, telling stories, summarizing text, helping someone prepare for an interview, and much more. To do all of this, ChatGPT uses a combination of machine learning techniques and natural language processing (NLP) algorithms, both of which are subsets of artificial intelligence.
This Isn’t Your Everyday Brand Impersonation Phish
The instant popularity of ChatGPT has made OpenAI a natural target for brand impersonation. While that part of the story isn’t too surprising, the detail and sophistication behind this latest phishing threat is so clever that we asked an INKY expert to break it down.
Brand Impersonation, Spoofing, and a Malicious Link
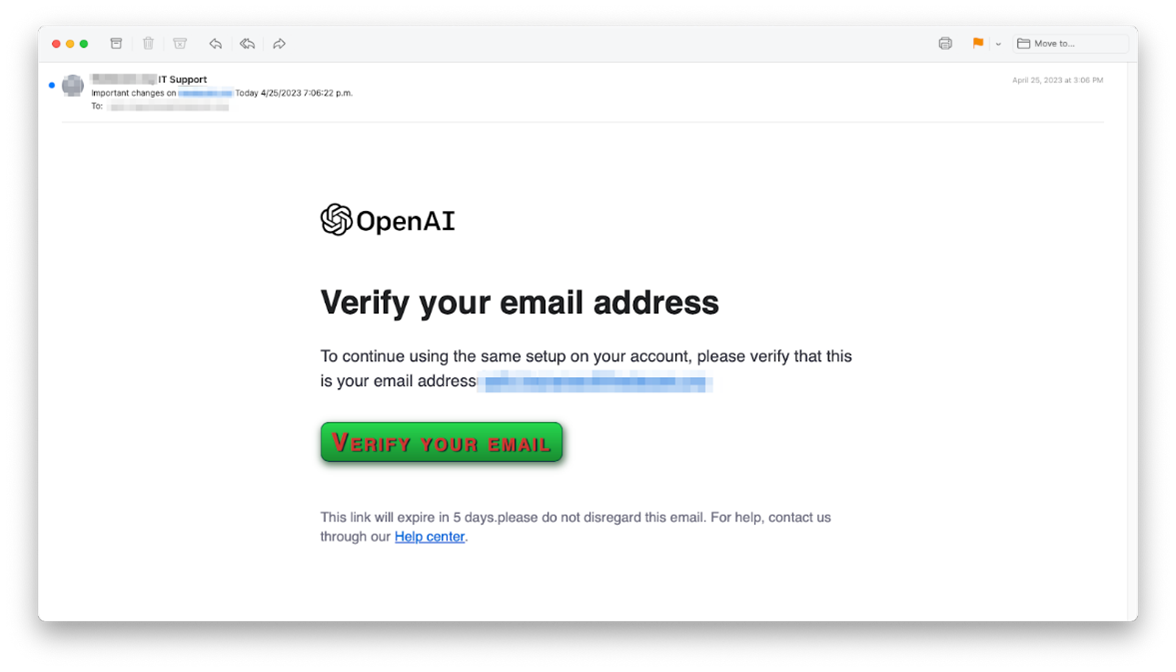
Brand impersonation (a.k.a. brand forgery) emails look legitimate because they are pretending to be from a brand that employees are familiar with or trust. INKY detected a phishing campaign targeting individuals and companies interested in ChatGPT. The initial email is branded with the OpenAI logo and the message is nearly identical to the one users receive when they sign up for a new ChatGPT OpenAI account. To do this, bad actors simply copy and paste HTML/CSS of a real email and swap a safe link for a dangerous one.
Spoofing comes into play with the display address. Phishers spoofed the employee’s domain in the display address as “Recipient Domain IT support” to make it appear as though the email came from the recipient’s IT department.
Malicious links are commonly used in phishing emails. In this case, by hovering over the “Verify Your Email” button in the image below, the following link is displayed:
hxxps://bafybeidqi4sn5nfnfxlgasem4gsdmbq6m55iu6gtouomdgfwu4fx7ps7oq.ipfs[.]dweb[.]link/login.htm#b@inky.com
*HINT – take note of the highlighted text and we’ll explain it below.
The InterPlanetary File System (IPFS) and Why Phishers Love It
In the phishing email’s malicious link, we highlighted “ipfs[.]dweb[.]link”. This indicates that the malicious page you’re about to be taken to is being hosted on InterPlanetary File System (IPFS). The IPFS is a decentralized peer-to-peer file sharing network used to store and share data, in a distributed file sharing system.
What does that mean? Let us explain.
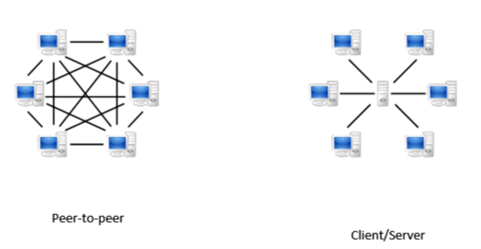
Most phishing sites follow a centralized client-server model where phishing content is hosted on a legitimate server that was hacked and hijacked by the phisher. These client-server models can be taken by the legitimate site owner or the hosting provider in the event the site is compromised or used in a phishing attack.
When IPFS sites are used in a phishing attack, the cybercriminal generally sets up his own fake site. The benefit here is that with IPFS it would be difficult for anyone to take down the site.
IPFS peer-to-peer model is distributed and hosted amongst multiple nodes in the network. These attacks are resilient to takedowns because the phishing content exists on multiple nodes at the same time so phishing content is still active even if one node is targeted.
Personalized Phishing Sites
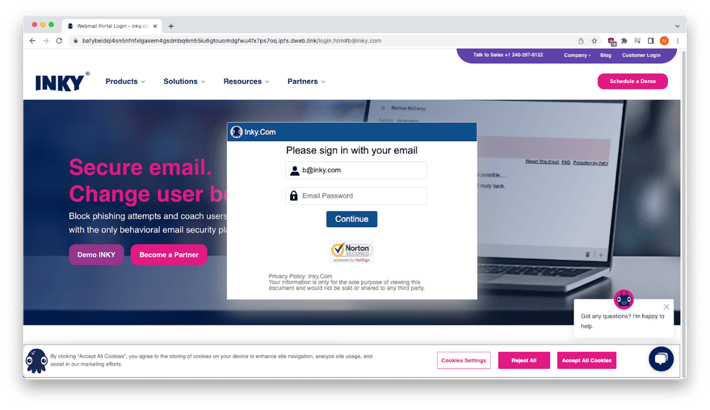
Now, do you remember the characters at the end of the malicious URL? It’s known as the URL parameter and in this case, it was “b@inky.com”. The magic behind this URL parameter is that it allows the cybercriminal to take each of his victims to a very convincing malicious website – one that mimics their own company website! The appearance of the phishing site depends on the URL parameter in the link. In this example, the site impersonates INKY because “b@inky.com” is the current URL parameter.
When the current URL parameter is changed, the malicious site impersonates the corresponding company. In this case, the b@starbucks.com URL parameter impersonates Starbucks! Pretty clever.
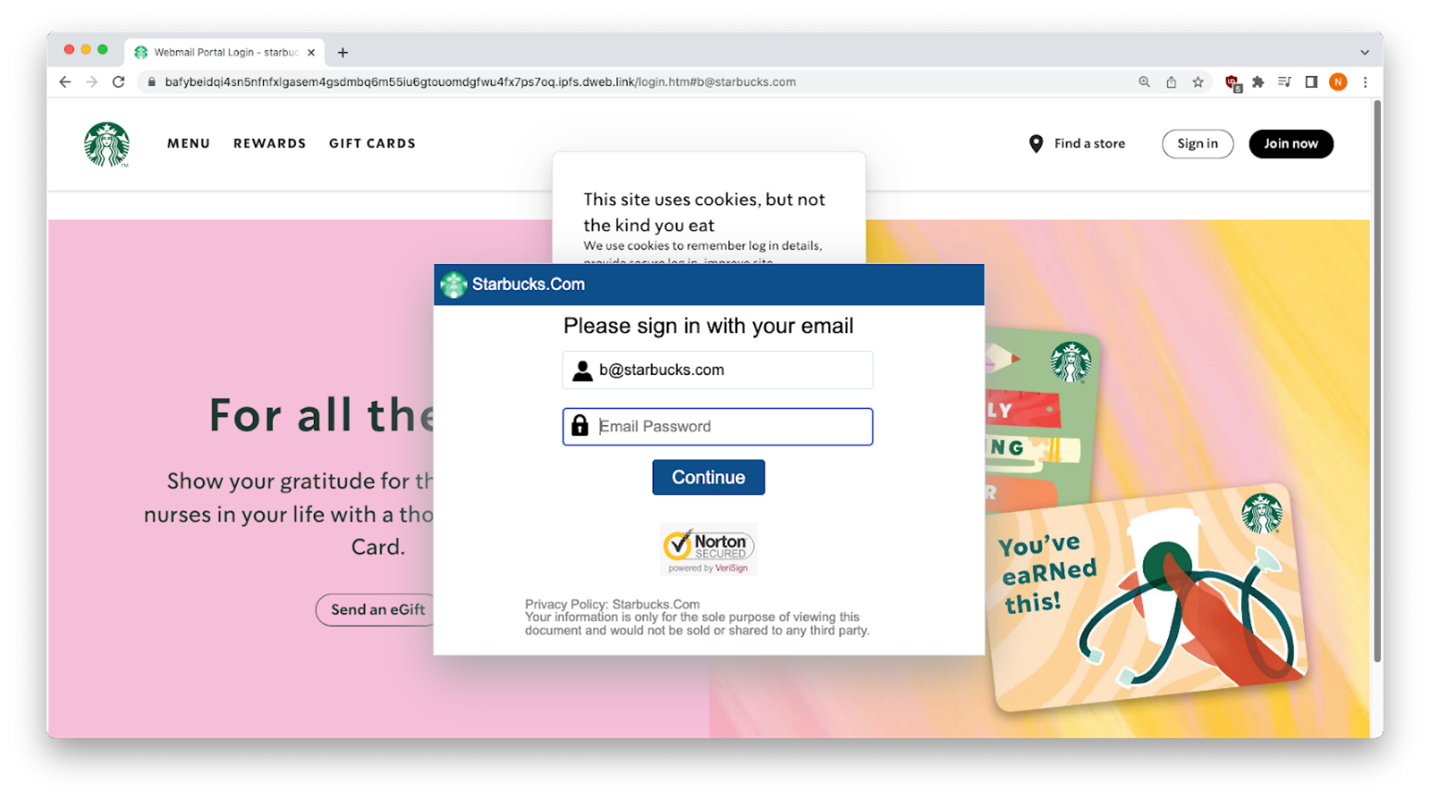
As you can see below, a first attempt at entering credentials returned an error message — but the data had already been harvested.
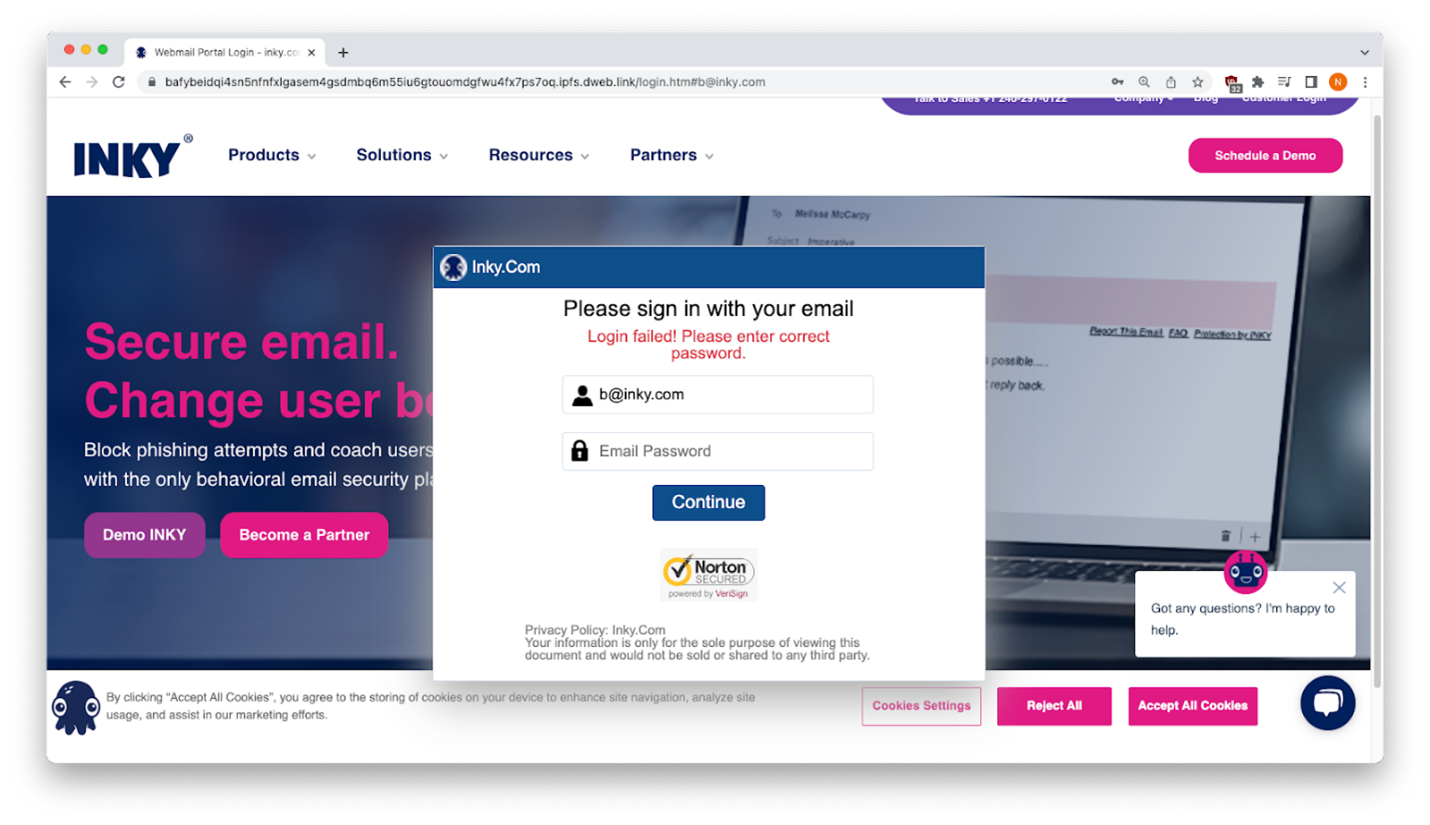
A second attempt harvests the data again and redirects the recipient to their own domain.
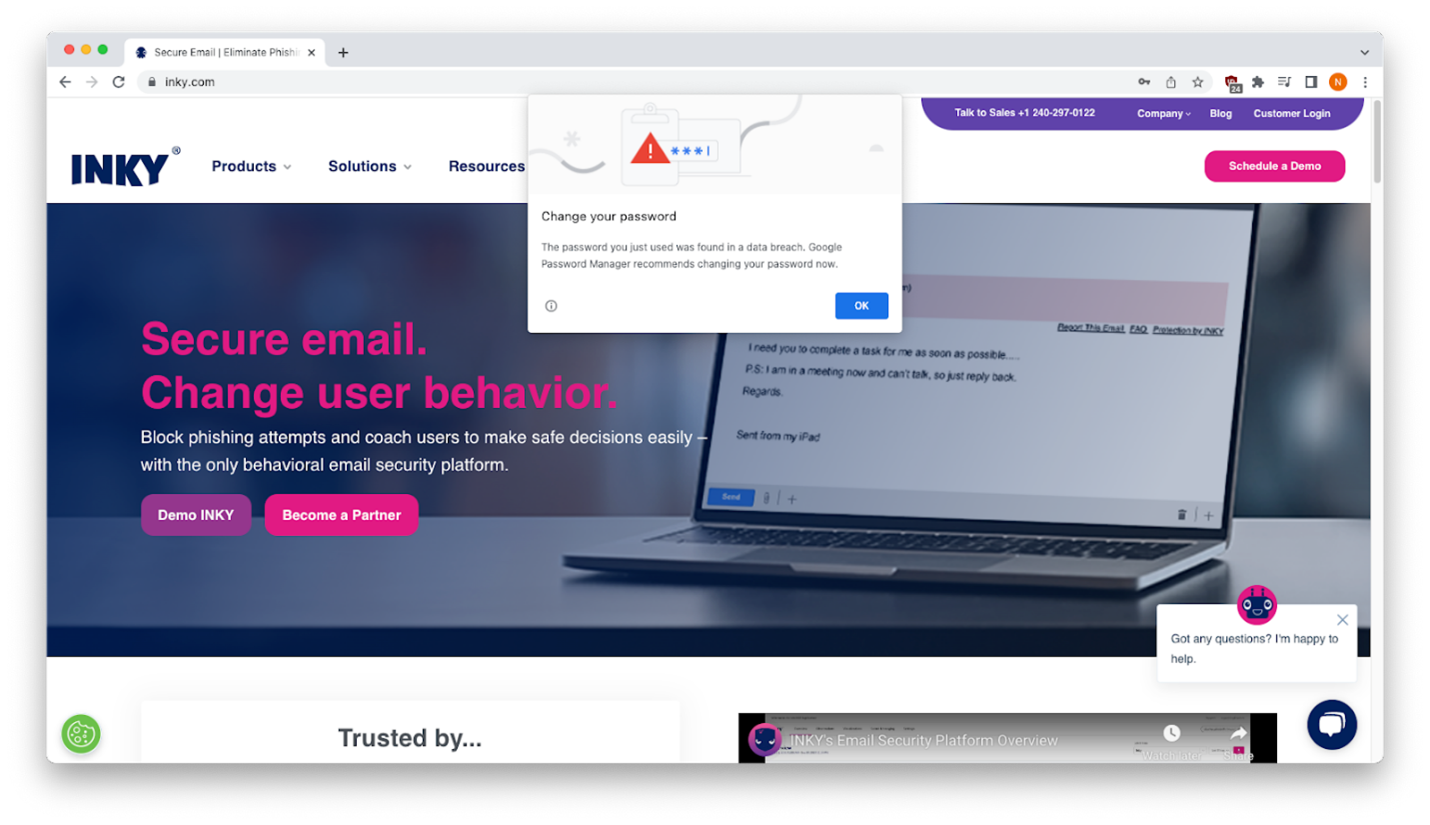
The redirection happens because the personal code uses a my_slice variable “window.location.replace()” to construct a new URL (in this case, inky.com) and replace the existing malicious URL.

As an extra benefit to the phishers, when they used replace(), the phishing site was not saved in the browser’s session history. So, the recipient would not be able to use the back button to navigate back to the phishing site.
A Final Word
Let’s summarize some of the tactics used in this OpenAI credential harvesting phishing attack.
Recap of Techniques
Brand impersonation — using brand logos and trademarks to impersonate well-known brands.
Spoofing – disguising an email address so it appears to be from someone familiar.
Malicious links – a clickable link that directs users to an illegitimate or unsafe website, usually for the purpose of harvesting credentials.
Credential harvesting — occurs when a victim thinks they are logging in to one of their resource sites but are really entering credentials into a dialog box owned by the attackers.
Dynamic redirection — uses elements of the victim’s email address, particularly the domain, to guide the attack flow.
Best Practices: Guidance and Recommendations
- Carefully inspect the display name and sender’s email address. In this case, the email claimed to be from OpenAI and the recipient’s IP department, but the sender’s domain has no relation to these entities.
- Recipients should confirm with their employer if it’s requested to sign into a new system.
- Hover over links to see where it goes.
Without the right email security protection, falling for phishing threats is easy to do. However, as a Managed Service Provider (MSP), you’re looked to for answers. Ensure you have the right email security partner on your side.
INKY is the behavioral email security platform that blocks threats, prevents data leaks, and coaches users to make smart decisions regarding the safety of their email. Like a cybersecurity coach, it signals suspicious behaviors with interactive banners that guide users to take safe action on any device or email client. IT teams don’t face the burden of filtering every email themselves or maintaining multiple systems. Through powerful technology and intuitive user engagement, INKY keeps bad actors out for good. Start a free trial or schedule a demo today.
----------------------
INKY is an award-winning, behavioral email security platform that blocks phishing threats, prevents data leaks, and coaches users to make smart decisions. Like a cybersecurity coach, INKY signals suspicious behaviors with interactive email banners that guide users to take safe action on any device or email client. IT teams don’t face the burden of filtering every email themselves or maintaining multiple systems. Through powerful technology and intuitive user engagement, INKY keeps phishers out for good. Learn why so many companies trust the security of their email to INKY. Request an online demonstration today.



