Looking for the tell-tale signs of a phishing email is something many of us have come to do automatically. However, things get much trickier when the phishing emails come in the form of legitimate Adobe notifications, have been authenticated (SPF & DMARC) by adobe[.]com, and use actual Constant Contact tools as part of their approach. Even with these legitimate elements in place, phishers took this latest phishing scheme to a whole new level, layering on additional (and we mean lots of additional) phishing tactics to achieve maximum results.
Going into 2024, we predicted that the multi-layer phishing campaigns we saw in 2023 would become increasingly more complex. This phishing threat didn’t disappoint, setting the stage for what promises to be the most daunting year of cybercrime to date.
Let’s peel back the layers of this mysterious phish.
This phishing campaign targeted employees at financial institutions, biomedical companies, commercial and industrial HVAC businesses, employment agencies, and professional services firms. The phishers took a Spray & Pray approach, sending hundreds of thousands of identical messages to potential victims, hoping that a percentage of them will fall for the scam.
Cybercriminals started with what appears to be an email originating from a Microsoft server, appearing to be from the recipient’s Human Resources department. It was delivered as a legitimate Adobe notification. The sender’s email address is notifications@adobe.com and all emails were authenticated by Adobe ((SPF & DMARC) by adobe[.]com). Adobe has so many email marketing tools, it’s likely that the bad actors are abusing one of their services for phish to arrive in real Adobe notifications.
Personalization was another tactic employed. Phishers impersonated the recipient’s domain by taking the company name found in the email address to create a display name of “Recipient’s domain name” HR-team.
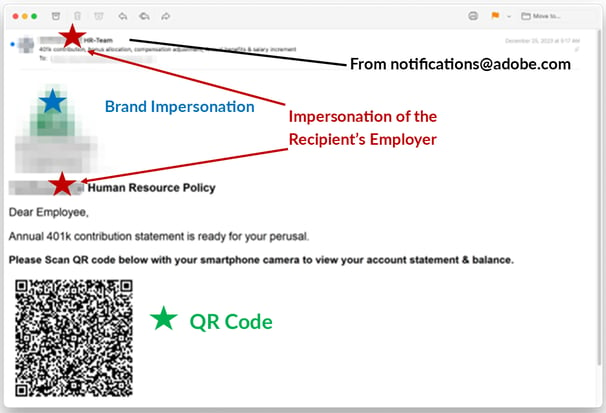
Another tactic used was brand impersonation. Each company’s logo was used in the body of the email. This is achieved by using Google’s API that automatically pulls the favicon image of the recipient’s domain to create a personalized phishing email for each person.
Every email of this phishing campaign also had a malicious QR code the employee is supposed to be used to view their 401K account statement and balance. Interestingly enough, this is where another legitimate tool is used. The INKY banners show that the domain of the QR code link is "r20.rs6.net". This is a well-known authentic Constant Contact domain used in email marketing. Bad actors abused the domain to redirect users to malicious sites. In the end, the payload is an effective advanced fees phishing scam.
But wait, there’s more…
The Ingenuity of an Image Based Phishing Campaign
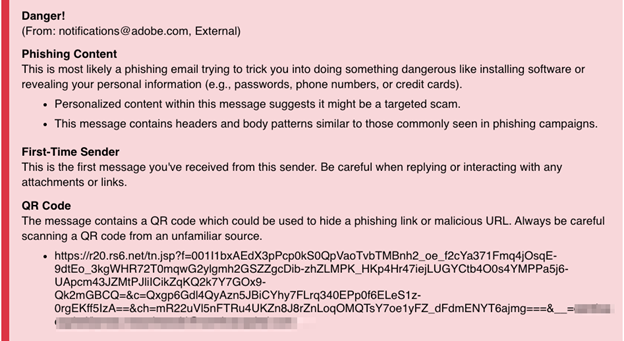
The multi-layered phishing tactics you’ve just read about are all visible approaches that help convince the reader the email is harmless, especially if the notification made its way through the company’s email security systems and arrived at the employee’s inbox. However, what the recipient can’t see is that the email they are reading is actually an imaged-based phish.
Image-based phish are designed to prevent anti-spam and email security scanners from analyzing an email’s text. INKY uses optical character recognition (OCR) that extracts the text from an attached email and uses it in combination with other artificial intelligence algorithms to detect an email as dangerous.
Recap of Techniques
- Personalized phish — algorithms that extract the recipient’s domain and impersonate that domain to create a unique phish for each recipient.
- Image-based phish — textual phish message is embedded in an image.
- Malicious QR code- conceals the malicious URL from recipients and security software.
- Brand impersonation— uses company logos and trademarks to impersonate well-known brands in order to make an email or malicious site look more legitimate.
- Advanced fees scam - occurs when a victim thinks they are logging in to one of their resource sites but are really entering payment information into a dialog box owned by the attackers.
Best Practices: Guidance and Recommendations
- Don’t scan QR codes from unknown sources. Websites reached by QR code might host malicious code that exploits vulnerabilities or steals sensitive data.
- Be cautious when entering financial and personal information on a site reached with a QR code.
- Carefully inspect the sender’s email address. While notifications@adobe.com is a legitimate Adobe email address, it’s suspicious that an employer would send sensitive financial information using that platform.
- If you receive a suspicious email claiming to be from your employer with a new communication method, it’s best to contact them by phone or a similar established method of communication to verify the change first.
Multi-layered phishing attacks, especially those using malicious QR codes, are here to stay. The sophistication and expertise used by today’s cybercriminals make it impossible to catch all of a company’s phishing threats without the help of a proven expert in email security. INKY is the behavioral email security platform that blocks threats, prevents data leaks, and coaches users to make smart decisions regarding the safety of their email. INKY signals suspicious behaviors with interactive banners that guide users to take safe action on any device or email client. Through powerful technology and intuitive user engagement, INKY keeps phishers at bay. Start a free trial or schedule a demo today.
----------------------
INKY is an award-winning, behavioral email security platform that blocks phishing threats, prevents data leaks, and coaches users to make smart decisions. Like a cybersecurity coach, INKY signals suspicious behaviors with interactive email banners that guide users to take safe action on any device or email client. IT teams don’t face the burden of filtering every email themselves or maintaining multiple systems. Through powerful technology and intuitive user engagement, INKY keeps phishers out for good. Learn why so many companies trust the security of their email to INKY. Request an online demonstration today.



