When a company generating more than $86 billion in net revenue reaches out to do business with you, chances are they’ll have your full attention.
What INKY Caught
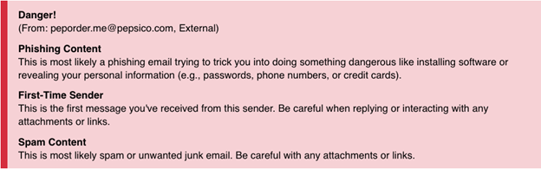
INKY has detected bad actors impersonating PepsiCo in a phishing campaign that infects victims’ computers with malware. As usual, it all starts with a phishing email. In this case, the phishers are impersonating the PepsiCo brand, pretending to be potential clients. They are claiming to need what the recipient sells and they’re asking them to submit a quote for PepsiCo to review.
In this case, the phishers are impersonating the PepsiCo brand, pretending to be potential clients. They are claiming to need what the recipient sells and they’re asking them to submit a quote for PepsiCo to review.
What the would-be victim doesn’t know is that attached to the email is a malicious disk image, disguised as a RFQ (Request for Quote). One click will infect the victim’s computer.
A disk image is a single file that reproduces all the contents and functionality of a hard disk, optical disk, or other storage device. The disk image file is usually quite large and could be anywhere from several megabytes to several gigabytes in size. Malicious disk drives end in one of several extensions including .iso, .cue., .bin, .img, or .dmg.2
A disk image is a great way to backup hard disks because unlike conventional backup programs, a disk image makes a copy of the structure of the drive, including data, programs, and formatting. A disk image so closely mirrors the actual drive that if your main drive ever fails, you can restore everything from the disk image, including personal preferences and plugins.2
That all said, when a malicious disk image is at play, it can give attackers a great deal of access. In fact, Trojan infected machines may give attackers the ability to:
- Surveil user behavior with keystroke monitoring, screenshot captures, webcam recordings, and other spyware
- Delete, download, manipulate, and steal files
- Gain admin privileges and disable user account control (UAC)
- Install malware, ransomware, and other viruses.
Let’s Take a Closer Look at the Phishing Email
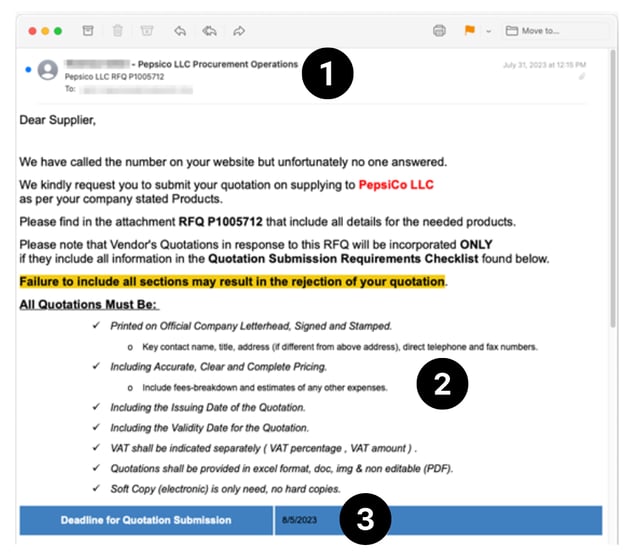
Looking at the top half of the email, we can see how the bad actors are luring in victims.
- As mentioned, the sender’s email address was spoofed. What shows is me@pepsico.com and the sender’s display name uses that of an actual PepsiCo employee who is responsible for procurement management.
- It is becoming common practice for cybercriminals to create phishing emails with a good amount of detail so they seem more convincing. You’ll notice this email comes with a lot of information, as well as a threat their RFQ could be rejected if they don’t follow the specific instructions outlined in the email.
- A common phishing technique is to create urgency. The phisher does that by imposing a deadline for the RFQ.
There are also a few things to point out in the bottom half of the email.
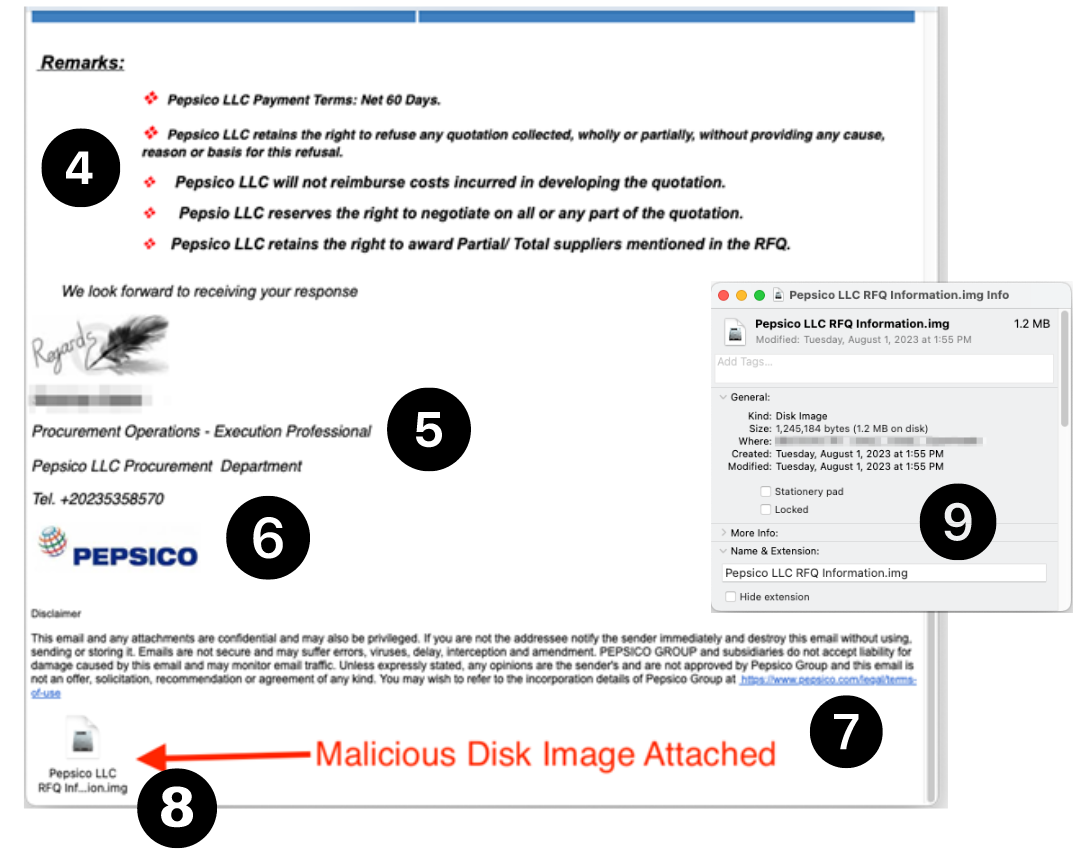
- You’ll notice things start to get a little sloppier. The bullets don’t line up, punctuation is sketchy, and PepsiCo is now spelled with a lower case “c”.
- While it was clever of the phishers to sign the email with the name of an actual PepsiCo employee who works in procurement, they gave him the title of “Execution Professional”, which sounds pretty grim.
- While phishers did use an accurate PepsiCo logo, the phone number has one digit too many for a U.S. number.
- While the disclaimer reads a little funny, it actually does link to PepsiCo’s legal terms of use page, providing some added authenticity.
- The most important (and dangerous) part of this email is the malicious attachment it contains. This is actually the malicious disk image mentioned above. You’ll notice it ends in the telltale img.
- Most people wouldn’t notice the size of the attachment, but at 1.2 MB, this is a suspiciously small file, considering most malicious disk images are much larger.
Why This Phishing Scam Works
With phishing emails, it’s important to choose a brand that prompts readers to act. PepsiCo’s product portfolio boasts more than 500 different brands, including its flagship Pepsi product, Frito-Lays, Gatorade, Quaker, Lipton, Doritos, Rold Gold, Starbucks RTD beverages, and many more. With 291,000 employees located all over the world, PepsiCo is a global powerhouse.1
The way in which this phishing email was deployed also aids in its success. To evade geographical filters, these emails were sent from several U.S.-based virtual private servers controlled by bad actors. Also, the phishers used a “spray and pray” technique - meaning they sent out large quantities of the email in hopes that a percentage of recipients would fall for the scam and click on the malicious link.
A Final Word
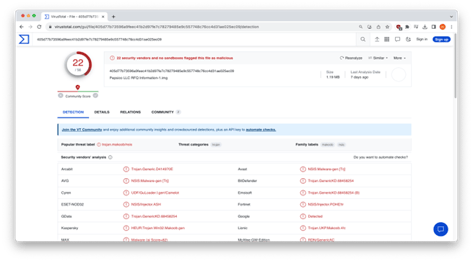
 INKY flagged this email for a number of reasons and we were curious to see whether other security vendors signaled out this phishing threat as a malicious trojan. After uploading it to virustotal, we found that fewer than half – 22 out of 56 – found it to be problematic. The others let it slip by. To us, that speaks volumes about the need for a strong and proven email security partner.
INKY flagged this email for a number of reasons and we were curious to see whether other security vendors signaled out this phishing threat as a malicious trojan. After uploading it to virustotal, we found that fewer than half – 22 out of 56 – found it to be problematic. The others let it slip by. To us, that speaks volumes about the need for a strong and proven email security partner.
Recap of Techniques
- Brand impersonation — uses elements of a well-known brand to make an email look as if it came from that company.
- Trojan horse - malware that misleads email recipients because it is disguised as a legitimate file, though its intention is to execute malicious code.
Best Practices: Guidance and Recommendations
- Don’t open email attachments or links from unknown senders.
- Look for the telltale signs of phishing to include mistakes in grammar and punctuation as well as inconsistencies in wording and treatment of the brand.
- Before replying or opening an attachment, verify the sender’s identity with another means of communication. In this case, an email recipient can contact PepsiCo with a phone number on their official website.
- Do not provide sensitive information over email.
- Always backup your files in case of an attack that damages them.
To truly have a handle on phishing threats, you need a third party’s assistance. INKY offers a relentlessly effective level of security, capable of detecting and stopping phishing threats before anyone becomes a victim. Using computer vision, artificial intelligence, and machine learning, INKY provides a level of ingenuity that is unlike other email security platforms. INKY sees things the way humans do, recognizing logos, brand colors, email signatures, and more — but it also sees the millions of things humans can’t, spotting imposters by as little as a pixel.
See what INKY can do for your business and your customers. Schedule a free demonstration today.
----------------------
INKY is an award-winning, behavioral email security platform that blocks phishing threats, prevents data leaks, and coaches users to make smart decisions. Like a cybersecurity coach, INKY signals suspicious behaviors with interactive email banners that guide users to take safe action on any device or email client. IT teams don’t face the burden of filtering every email themselves or maintaining multiple systems. Through powerful technology and intuitive user engagement, INKY keeps phishers out for good. Learn why so many companies trust the security of their email to INKY. Request an online demonstration today.
1Source: www.pepsico.com
2Source: www.easytechjunkie.com/what-is-a-disk-image.htm#google_vignette



