Over time, phishers deploy variants of phishing techniques that work. They have to keep modifying the specifics because the white hats catch on and mitigate their nefarious tricks. One particularly persistent pattern is the combination of hijacked email accounts and freeware websites. Both can be found in abundance.
The accounts can be hijacked directly or bought cheaply on the dark web. They have the benefit of being able to pass rudimentary email security checks (i.e., DKIM and SPF). Security software sees that they come from legitimate domains and “legal” IP address ranges.
Freeware sites are even easier to obtain. They invite users to sign up, often without verification. One such site is Telegraph, a free minimalist publishing tool that allows users to publish web pages instantly and anonymously without creating an account. These pages can be customized with embedded images and links.
Although many such sites are available, Telegraph is more attractive than most because of its unusually libertarian heritage; its founders openly propound a “live and let die” philosophy, catnip to phishers. Telegraph is a subsidiary of Telegram, a messaging service that, according to extensive documentation, has been used for illegal activities by child pornographers, white supremacists, and terrorists. Telegram was founded by two Russian brothers who are more or less living on the lam at the moment, supposedly in the Caribbean. Pavel Durov, the more public-facing brother, recently acquired French citizenship. The company is registered in the British Virgin Islands and has its operations center in Dubai. For a phisher, what’s not to love?
On Telegram, sent messages can be set to disappear after they’re read. Because of features like this, the service has replaced dark web forums as an encrypted messaging platform for criminals seeking to evade authorities. By setting up end-to-end encrypted private threads, the black hats can pass information without fear of detection.
Telegraph lets anyone set up a webpage. Controls are simple, and options are limited. All the enterprising publisher has to do to create a page is visit https://telegra.ph/, add text, images, and links, and then hit the “publish” button. That’s all phishers need.
Quick Take: Attack Flow Overview
- Type: phishing
- Vector: hijacked email accounts with telegra[.]ph links
- Payload: credential harvesting, cryptocurrency scams
- Techniques: brand impersonation, credential harvesting, hijacked accounts, free website abuse
- Platform: Microsoft 365
- Target: Microsoft 365 users
The Attack
From the end of 2019 through May 2022, INKY detected 1,429 malicious emails via the “Telegraph channel.” However, there has been a huge uptick in the volume of these attacks recently: 1,288 of these emails were sent in 2022 alone. The payloads included credential harvesting and cryptocurrency scams.
Credential Harvesting
Below is an example of one such email sent from a hijacked account.
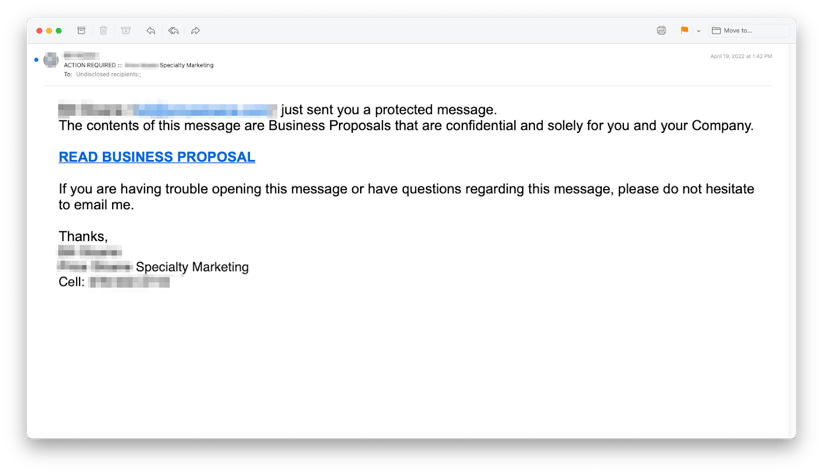
INKY users have been receiving phishing emails with telegraph links
In this case, the linked-to Telegraph page impersonated Microsoft, hosting a malicious link to a Microsoft credential-harvesting site. Clicking on the VIEW PDF DOCUMENT link led to a credential harvesting site, where the victim was greeted with a notice of password protection, setting them up to enter credentials.

A misleading link on the Telegraph site invited the mark to view a PDF.
The victim was presented with a realistic-looking Microsoft login dialog (the page below shows an example of such a dialog; the actual linked page had already been taken down).
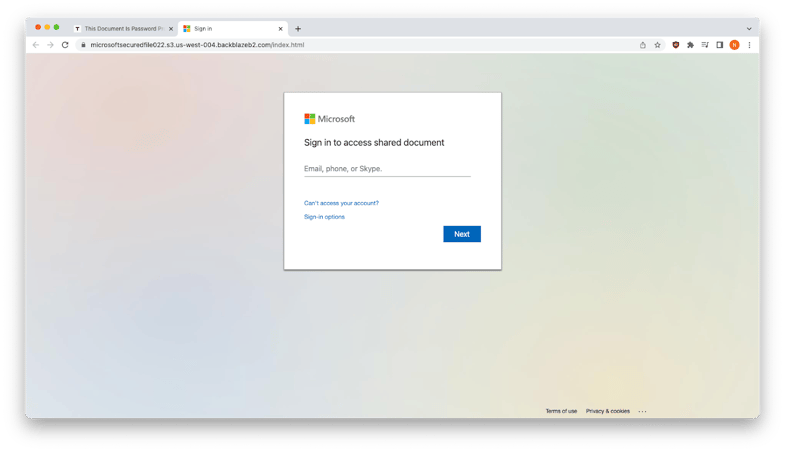
A realistic-looking Microsoft login page
Cryptocurrency Scam
In another case, a fraudulent email used frightening language to try to extort the victim into sending cryptocurrency. The email looked like this:
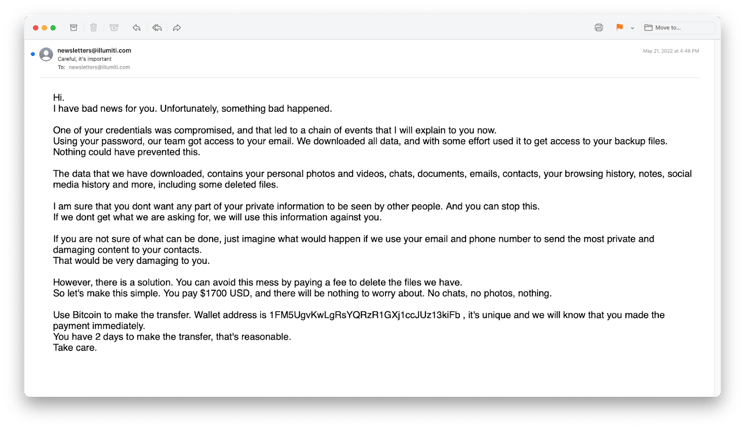
Extortion email sent from a compromised legitimate account
The Telegraph page hosted a crypto gathering site.
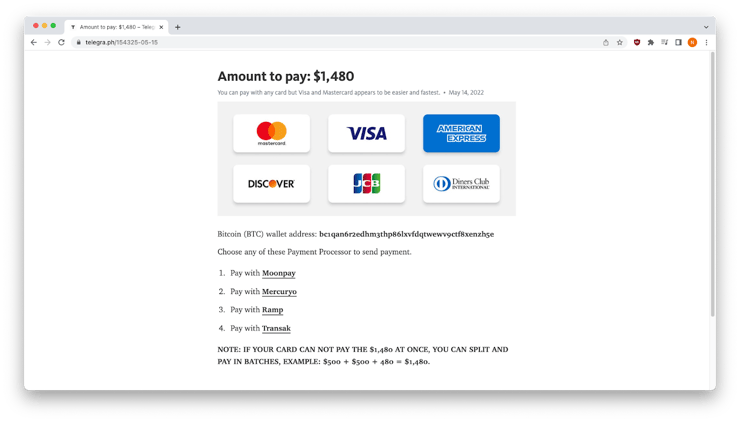
Pay here to avoid the consequences!
As of publication, the bitcoin address associated with this scam had received several transactions totaling $2,578.71.
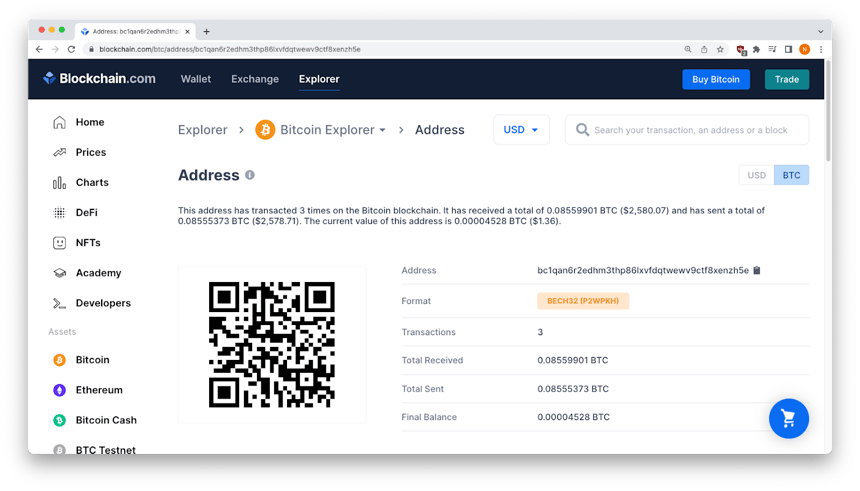
The leger at Blockchain.com showed that the scam worked several times
Recap of Techniques
- Brand impersonation — uses brand logos and trademarks to impersonate well-known brands.
- Credential harvesting — occurs when a victim thinks they are logging in to one of their resource sites but is instead entering credentials into a dialogue box owned by the attackers.
- Hijacked accounts — are used by phishers to make their emails appear to come from legitimate senders
- Free website abuse — allows attackers to set up a malicious site that can pass most security checks
Best Practices:
Guidance and Recommendations
Email recipients should always be suspicious of any message that asks them to log in with credentials to view a document. Legitimate organizations rarely use this type of authentication. Another bright red flag should go up if a sender asks a recipient to use Microsoft credentials to view, say, a DocuSign document.
One way to stay safe when receiving an unexpected email from a known entity (e.g., a bank, a credit union, a government body) is to confirm its legitimacy by contacting them directly via a different communication platform.
A recipient should never reply or act on any email in which the sender threatens to release embarrassing or personal information unless they are paid in cryptocurrency.
Ready to see INKY in action? Start a free trial or schedule a demo today.
----------------------
INKY is an award-winning, behavioral email security platform that blocks threats, prevents data leaks, and coaches users to make smart decisions. Like a security coach, it signals suspicious behaviors with interactive banners that guide users to take safe action on any device or email client. IT teams don’t face the burden of filtering every email themselves or maintaining multiple systems. Through powerful technology and intuitive user engagement, INKY keeps bad actors out for good. Learn more about INKY™ or request an online demonstration today.


