It’s no secret that small businesses have suffered greatly due to the pandemic. In 2021 the U.S. Small Business Administration (SBA) oversaw the distribution of more than $416 billion in emergency relief aid, helping over 6 million small businesses keep their doors open and their workers paid.1 Even with the aid that was given, many small businesses are struggling in the face of inflation, supply chain issues, depleted savings, hiring difficulties, and more. Sadly, as these small business owners push forward, navigating the rough seas ahead, some could soon find themselves ensnared in the traps of a new COVID-19 phishing scheme.
COVID-19 Continues to Be a Lure in Phishing Emails
INKY observed a welcomed but short-lived decline in pandemic-related phishing emails this summer, before spiking to an annual high in September.
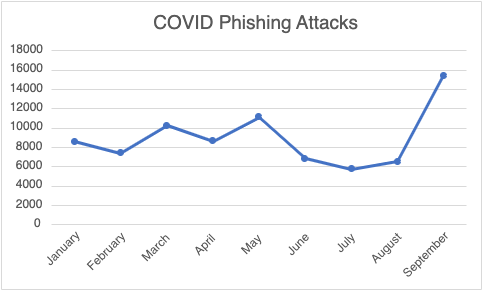
Number of COVID-19 phishing emails in 2022
One particularly slippery phish INKY recently detected combined brand impersonation, credential harvesting, and Google Forms abuse tactics.
First, A Little Added Background.
Google Forms is a free, web-based survey software offered by Google. Abusing Google Forms is a clever phishing tactic for several reasons:
-
It’s trusted by both consumers and businesses.
-
Bad actors can use Google’s infrastructure to host phishing content and harvest data – for free.
-
Evading detection is easier because its high reputation domain won’t appear in threat intelligence feeds.
-
Traffic to and from the service is secured with Transport Layer Security (TLS) encryption so defenders can’t easily inspect it.
Also, as you might imagine, the Small Business Administration (SBA) is a familiar name to many, due to the major role it played in the distribution of COVID-related relief through such plans as the Paycheck Protection Program, Restaurant Revitalization Fund, COVID Economic Injury Disaster Loan program, and others. This familiarity with the SBA adds to the vulnerability of small businesses being phished as part of a brand impersonation scheme.
What INKY Caught
INKY users received a phishing email claiming to be a COVID-19 grant application from the SBA. Unbeknownst to many, the SBA recently stopped accepting applications to their COVID-19 relief loan and grant programs.2 Still, it includes an enticing offer for any unknowing small business owner: Simply fill out the form and find out if you’re qualified to receive the funds. Clicking on “Apply Now” takes recipients to a survey on Google Forms.
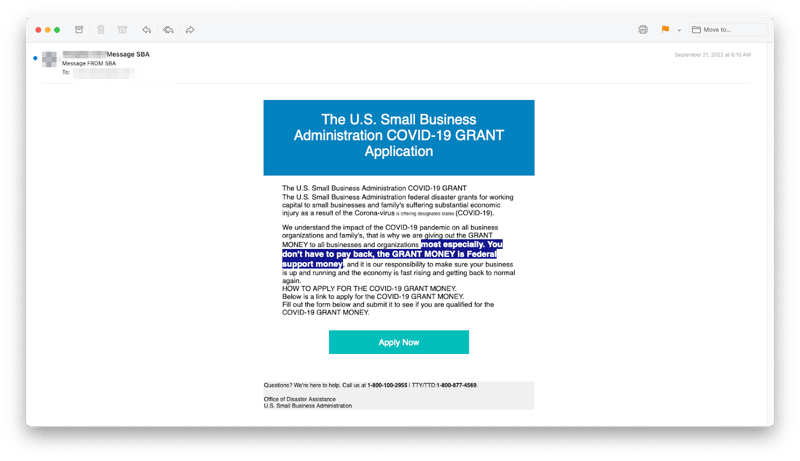
SBA Impersonation Email
An Impressively Designed Credential Harvesting Form
Any small business owner who had previously applied for legitimate loans and grants could be easily fooled by the form itself. The top of the form appears to be a cut-and-paste of a genuine COVID-19 grant message and the questions which follow are very similar to those the SBA asks applicants in legitimate circumstances. 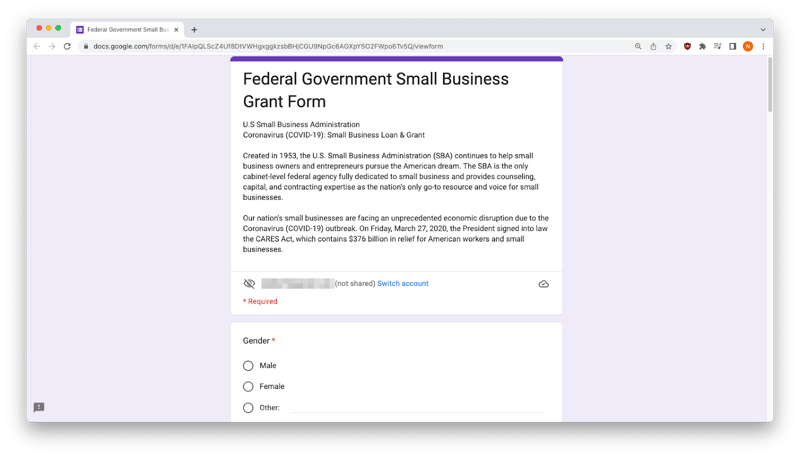
Top of Form
As you can see, the questions are designed to extract users personally identifiable information (PII) and include EIN, SSN, driver's license details, and bank account information. All of this information can easily be sold on the dark web or be used to drain your bank account quickly.
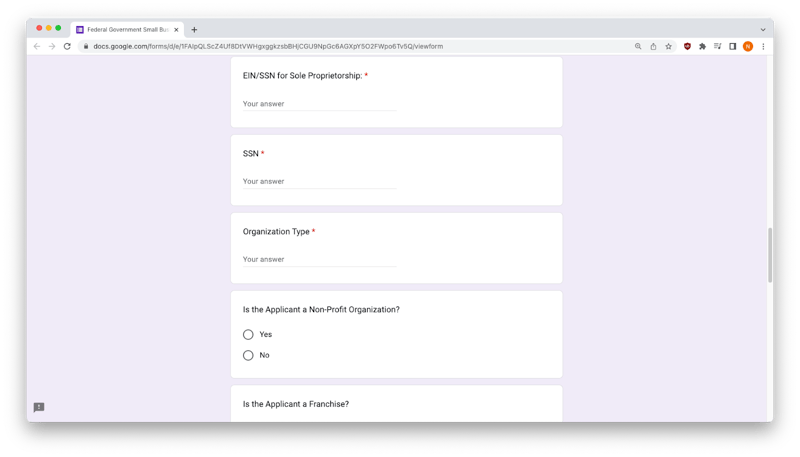
Middle of Form
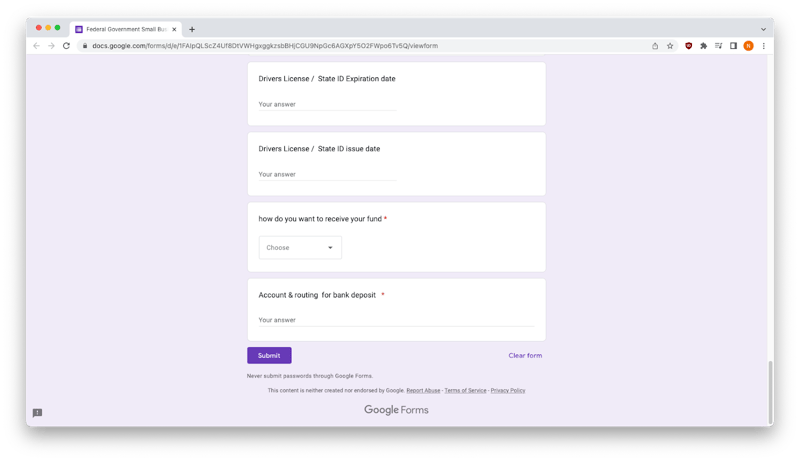
Bottom of Form
Using the purple “Submit” button sends all data to the phishers who created the form. And, as you can see in the screen to the right, Google Forms even helps the cybercriminals generate a final message, confirming their information was received – officially making them a victim of a credential harvesting and brand impersonation scheme. 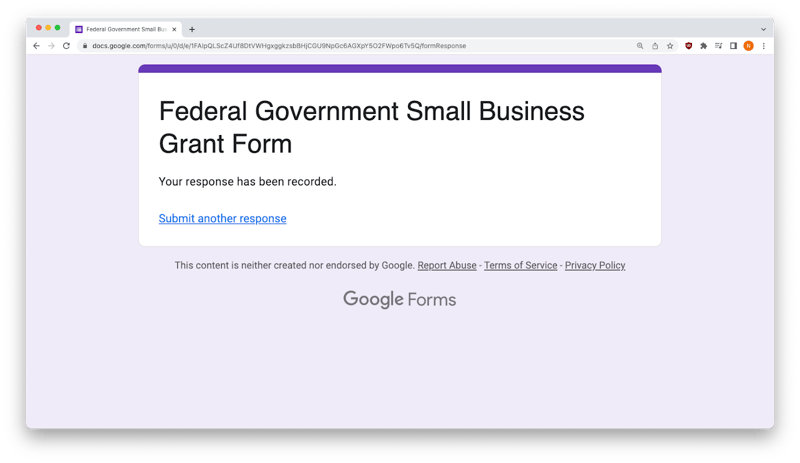
There is something else that a more discerning eye might have noticed. Because this cybercriminal used a legitimate Google Forms survey to harvest credentials there is a line populated just under the ‘Submit” button that says, “Never submit passwords through Google Forms.”
It’s not a good lesson to learn the hard way.
Ironically, if you look a little further, beneath the “Submit” button you’ll also see Google’s “Report Abuse” button. It’s not an option you see too often in phishing scams, and could easily be ignored by anxious small business owners who fall for this threat.
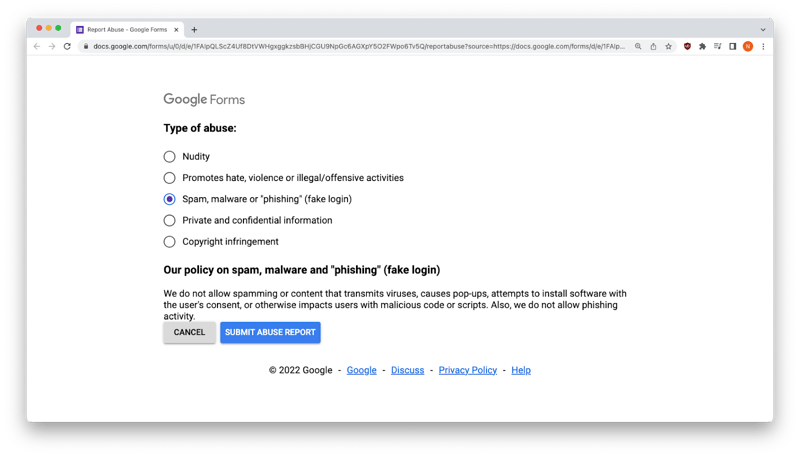
Google Abuse Form
A Word from the Grammar Police
A common rule of thumb in recognizing phishing threats is to look for grammatical, style, and usage errors. While this bad actor did a passable job, there are still inconsistencies that serve as a good reminder to take a closer look at suspicious emails – especially those that seem too good to be true. In this case:
Initial Email
-
Family’s should be plural
-
Corona-virus is not a commonly acceptable usage
-
“is offering designated states” is not grammatically correct
-
Words are omitted in sentences throughout
-
Repetitive, urgent language encouraging you to apply seems rather salesy
-
The use of all caps in GRANT MONEY feels and looks unprofessional
Survey Form
-
Use of inconsistent capitals
-
Questions posed with no question mark
A Final Review
Let’s take a final look at INKY’s discovery of this SBA COVID-19 Grant Application scheme.
Recap of Phishing Techniques
-
Brand impersonation — uses elements of a well-known organization to make an email look as if it came from a legitimate source
-
Data or credential harvesting — collecting personal data under false pretenses
-
The exploitation of current events — capitalizes on the uncertainty, fear, and urgency related to COVID-19
-
Free cloud resource abuse — allows attackers to leverage the reputation of popular web application domains
Best Practices: Guidance and Recommendations
-
Remember what to look for in a phishing email
-
Carefully inspect the sender’s address if you receive an email claiming to be from the U.S. government. Official U.S. government domains usually end in .gov or .mil rather than .com or another suffix
-
Never submit sensitive information (password, SSN, DOB, etc) in online surveys
-
Get INKY
Even in Small Business, Cybercrime is Big Business
In 2021, cybercrime in the form of government impersonation accounted for $142.6 million in financial losses. Any portion of that could put a small business in ruins. Imagine, working hard enough to pull your small business through an unprecedented global pandemic, only to have your company brought down by a phishing email. But it doesn’t have to be that way. Businesses of all sizes need the help of a third-party email security platform to stay safe from phishing threats.
So far in 2022, INKY has detected 14,450 phishing emails with links to abused Google Forms pages. Just think about what we can do for your business.
INKY is the behavioral email security platform that blocks threats, prevents data leaks, and coaches users to make smart decisions regarding the safety of their email. Like a cybersecurity coach, it signals suspicious behaviors with interactive banners that guide users to take safe action on any device or email client. IT teams don’t face the burden of filtering every email themselves or maintaining multiple systems. Through powerful technology and intuitive user engagement, INKY keeps bad actors out for good. Start a free trial or schedule a demo today.


