It will take some time before all of us are able to forget about the Southwest flight debacle of 2022. As one of the world’s leading carriers, they boasted one of the lowest consumer complaint rates in 2021.1 Of course, that ranking may well change after hundreds of thousands of passengers were left stranded over the holidays when more than 16,700 Southwest flights were canceled.
The holiday horror stories were plentiful and included missed vacations, misplaced luggage, five-hour telephone hold times, mile-long rebooking lines, and so much more. While this certainly doesn’t bode well for Southwest, the mood was just right for some savvy cybercriminals to cash-in on a very annoyed public.
Southwest Survey, Anyone?
After a three-day cross-country drive, an extended stay at the kennel for your dog, and vacation days you couldn’t afford to give up, you might be ready to give Southwest a piece of your mind. That was the basis of the Southwest phishing scam INKY recently uncovered.
Mid-way through December, INKY began detecting what has been an ongoing phishing campaign that impersonates Southwest Airlines. Phishing emails are being sent from newly created domains, set up explicitly for these attacks.
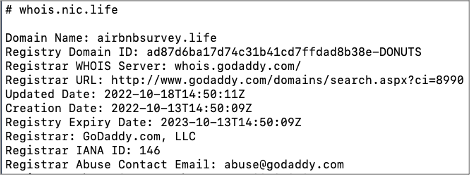
WHOIS results for a sender domain:
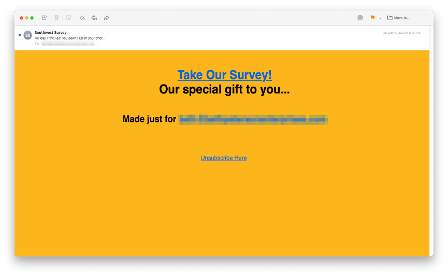
The emails offered a $100 gift card and other special rewards for those willing to take a survey. Some of the emails use the Southwest logo and brand images, while other versions simply impersonate Southwest in the display address. Regardless of the format, if you’re willing to take the survey you will be taken to a malicious website that also impersonates the airline.

The landing page of the website is very clever. It looks rather legitimate and includes some extras, such as:
Deadline – to promote quick reactions, the email includes a time clock and a statement listing a January 5th deadline.
Branding – the background image is clearly that of Southwest.
Reward – a tempting gift with a $100 value.
Exclusive – making the recipient feel special is also a good way to reel them in.
Disclaimers and other links you’d regularly see.
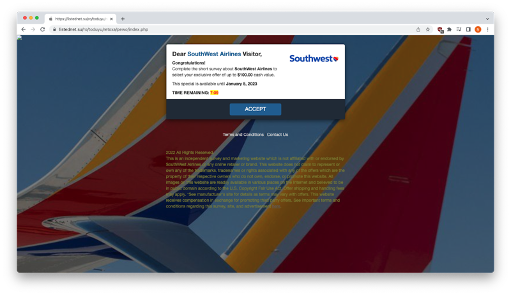
On the other hand, the landing page above does include a few clues that it could be suspicious, even if they can be difficult to find:
Risky Domain – the phishing site’s domain is “listednet[.]su”. The “.su” is the country code for the Soviet Union and it is known to be used by cybercriminals because of its relaxed and outdated terms of service.2
Misuse of Capital Letters - Throughout the phishing site, Southwest is spelled with a capital “W”. Spelling SouthWest with a capital “W” is not in accordance with their brand.
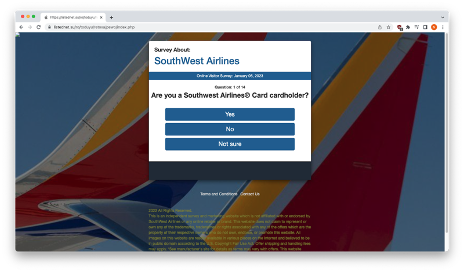
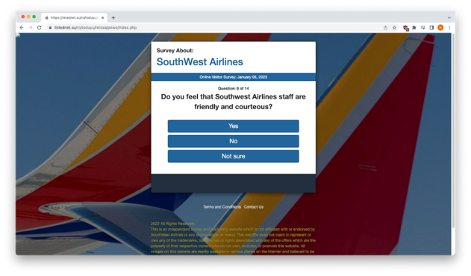
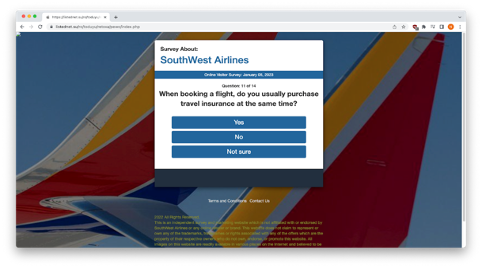
If you choose to take the survey, you will be presented with 14 questions after selecting “ACCEPT”. Here are a few of them:
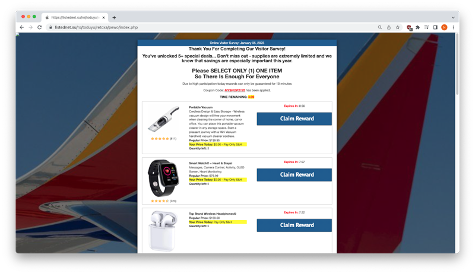
After completing the survey, you will be able to select and claim a reward. Adding the fact that a coupon code has been applied is yet another convincing element that works in the phishers favor. From here, you’ll see that things quickly shift to a credential harvesting mode.
For example, choosing the smartwatch takes you to a domain named bettertechdevices.com, which was newly created on 10/31/22.
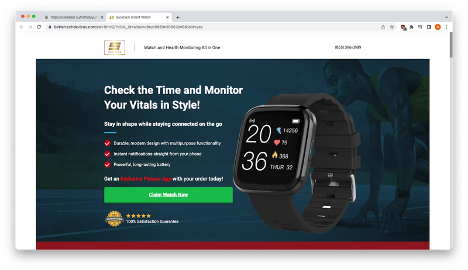
After clicking “Claim Watch Now”, you’ll be taken to a different page that asks for your mailing address and a credit card to pay for the shipping. Though very few people would have read the disclaimer on the initial landing page, the phishers were clever enough to include a sentence stating that shipping and handling fees may apply. Again, it speaks to the fact that cybercriminals are upping their game, being careful to think through multiple aspects of the threat as it is being built. They even went so far as to give you the option of adding EarPods to your order for just $6.77!
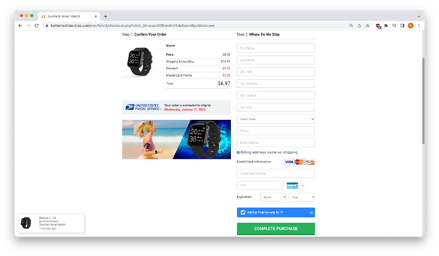
Lastly, at the bottom of the webpage you will find a few other gems, including fake reviews for the watch and a pop-up sales counter that tells you Noah from WY just purchased a SureTech Smart Watch as well.
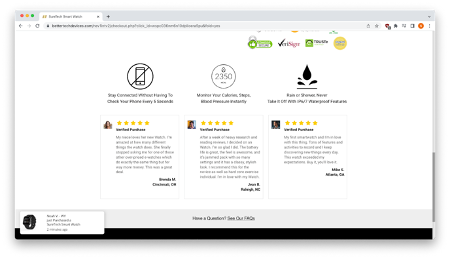
Completing your purchase sends your credit card credentials to the hackers where they can be sold on the dark web, billed monthly with a nominal fee you may not notice for years, or hackers could instantly start charging thousands of dollars’ worth of merchandise to your card.
A Phish of Many Faces
This Southwest credential harvesting scam was widespread, and the cybercriminals used a variety of subject lines, display names, addresses, and domains to fool as many people as possible. Here is a sampling:
Southwest Airlines Prize Scam Indicators:
Subject lines:
Your 100 Dollar Southwest Airlines Offer Is Waiting
Grounded by Southwest? Get your offer...
Bad Travel Experience? Claim your reward!
Notification: Southwest have you grounded? Claim your reward!
Travel plans interrupted? Claim your reward...
Claim Your Fifty Dollar Southwest Airlines Reward
Congratulations! You can get a $50 Southwest gift card!
You're Invited: To Redeem Your $50 Southwest Airlines reward
BONUS: $50 SOUTHWEST Gift Card Opportunity
Holiday Travel got you down? Claim your offer…
Congrats! You've received a Southwest Airlines reward
Display names:
Southwest Shopper Feedback
Southwest-Airlines
Southwest Opinion Requested
Southwest Shopper Gift Opportunity
Southwest Shopper Gift Card Chance
Southwest Survey
Southwest Airlines Feedback
Southwest Reward Special
Southwest Offer
Southwest Customer Offer
Southwest Gift
Sender email addresses:
SouthwestOpinionRequestedAmazingDeals@airbnbsurvey[.]life
SouthwestShopperGiftOpportunity@airbnbsurvey[.]life
SouthwestShopperFeedback@airbnbsurvey[.]life
southwest-survey@statellp-g[.]icu
southwest-survey@gasact5[.]top
southwest-reward-special@umbrella9[.]top
southwest_offer@paraqchk6[.]icu
southwest-reward@paraqchk6[.]icu
southwest.customer.offer@umbrella3[.]top
southwest_customer_offer@statellp-c[.]icu
southwest-gift@safe-driver4[.]icu
Malicious landing page domains:
offerregistry[.]su
listednet[.]su
A Final Word
Let’s summarize some of the tactics used in this Southwest flying phish scheme.
Phishing Techniques Used
Brand impersonation — uses elements of a well-known organization to make an email look as if it came from a legitimate source.
Data or credential harvesting — collecting personal data under false pretenses.
Time pressure — adding a sense of urgency and steering the victim away from doing a commonsense analysis of the situation.
Guidance and Recommendations
- Carefully inspect the sender’s email address, recognizing the difference between the local-part and domain of an email address. The local-part is everything before the @ symbol and the domain is everything after the @ symbol. Recipients should be suspicious that “Southwest” only appears in the local-part and the domain doesn’t belong to the airline.
- Watch out for display name spoofing. The display name is easily configurable and shouldn’t be relied on to tell if an email is authentic.
Southwest’s holiday shutdown is blamed largely on a preventable finding – the airline’s failure to upgrade their antiquated software. Oddly, the same risks exist for any victim of a phishing attack who doesn’t have the proper email protection in place. Avoid chaos, keep customers, and dodge the expensive repercussions that come with being phishing complacent.
INKY is the behavioral email security platform that blocks threats, prevents data leaks, and coaches users to make smart decisions regarding the safety of their email. Like a cybersecurity coach, it signals suspicious behaviors with interactive banners that guide users to take safe action on any device or email client. IT teams don’t face the burden of filtering every email themselves or maintaining multiple systems. Through powerful technology and intuitive user engagement, INKY keeps bad actors out for good. Start a free trial or schedule a demo today.
----------------------
INKY is an award-winning, behavioral email security platform that blocks phishing threats, prevents data leaks, and coaches users to make smart decisions. Like a cybersecurity coach, INKY signals suspicious behaviors with interactive email banners that guide users to take safe action on any device or email client. IT teams don’t face the burden of filtering every email themselves or maintaining multiple systems. Through powerful technology and intuitive user engagement, INKY keeps phishers out for good. Learn why so many companies trust the security of their email to INKY. Request an online demonstration today.
1Source: https://www.statista.com/topics/3041/facts-and-figures-about-southwest-airlines-co/
2Source: https://www.theguardian.com/technology/2013/may/31/ussr-cybercriminals-su-domain-space


