 Hollywood’s writers and actors have been feeling the financial pinch since both groups went on strike back in July. After five long months, Hollywood writers have finally returned to work, but the only actors who have been bringing home a paycheck are the bad actors.
Hollywood’s writers and actors have been feeling the financial pinch since both groups went on strike back in July. After five long months, Hollywood writers have finally returned to work, but the only actors who have been bringing home a paycheck are the bad actors.
That’s right. Bad actors – also known as cybercriminals and phishers – are impersonating some of the more popular streaming services in an attempt to tap into what is poised to be a $330 billion industry.1
Let’s break down three streaming service phishing threats INKY recently caught.
The Audience: It’s Like Shooting Phish in a Barrel
Every phishing scam needs a target audience and bad actors would be hard-pressed to find one as monumental as this one. Consider this:1,2
- 85% of U.S. households have at least one video streaming subscription.
- In 2022, U.S. consumers spent $34 billion on digital home entertainment.
- The amount of time Americans streamed video in 2021 is equal to 15 million years!
Think about it. The majority of households have streaming services, and they depend on them so much that they are poised to act quickly should issues with their service arise. It’s a best case scenario for cybercrime.
The Anatomy of a Phishing Phone Scam
The first two examples you see are phishing phone scams. Generally, phone scam phishing emails consist of a plain message (from what appears to be a legitimate source) with no suspicious links or malware attachments, featuring a simple pitch and a phone number.
The target is supposed to be persuaded by the message to call the number. At the other end of the line is someone working for the phishers who tries to extract information from the caller. Victims are usually met with one of the following outcomes:
- Bad actors claim they need victims to install remote access tools on their computer to resolve the issue.
- Victims are directed to a malicious site where banking information is requested.
- Victims are asked to buy gift cards to be reimbursed for the phony invoice charges.
The effectiveness of these techniques relies on the panic a victim might feel if they received an invoice for goods or services that they did not purchase or a threat of service cancellation. The emotional reaction to a notification of this sort can be strong and may impair one’s judgment. The natural response to reading an alarming message is to get right on the phone and try to back out of the order, or, barring that, find a way to obtain a refund. The phishers take advantage of this disrupted emotional state to extract personal or financial information before the victim realizes that something is off.
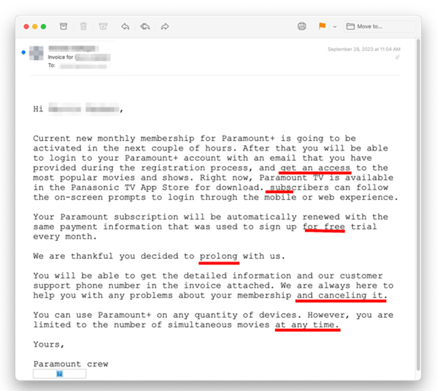
A Phishing Phone Scam of Paramount Proportions
The number of Paramount+ subscribers reached 77 million in 2022.3
Recipients received a phone scam phishing email impersonating Paramount+ that claims an automatic renewal of a subscription will be processed. All the emails originated from AOL free-mail accounts which have a high sender reputation, so they are able to pass email authentication (SPF, DKIM, DMARC).
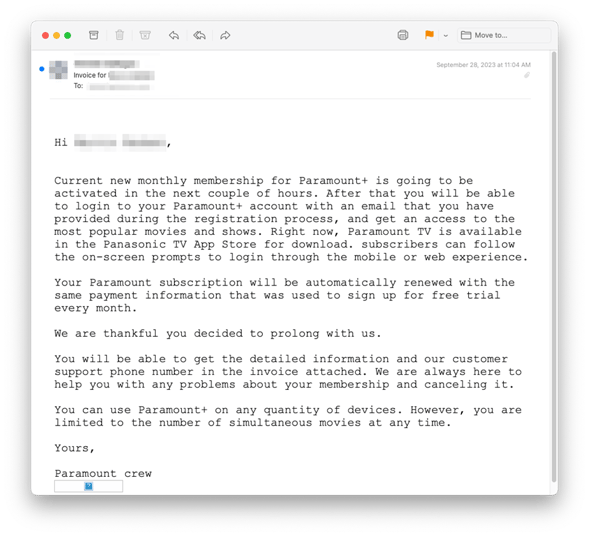
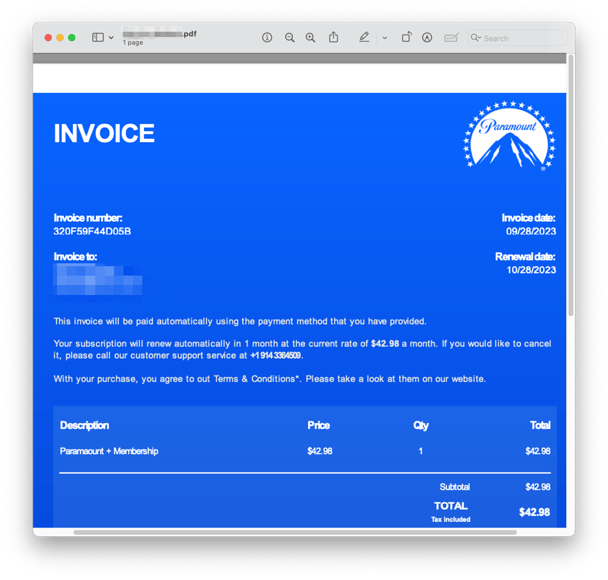
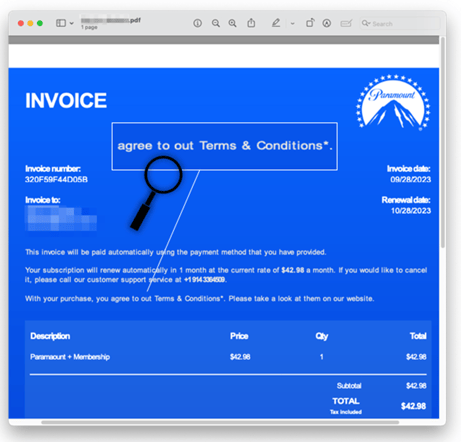
Each email has a fake invoice attached as a PDF. You’ll see the bad actors included a monthly fee that would get most readers concerned. The running rate of Paramount+ Essential is just $5.99 a month, not $42.98.
Disney+ Phishers Create a Convincing Look-Alike Domain
By the end of 2022, Disney+ had 44 million subscribers.4
In a similar phishing phone scam, bad actors sent a phone scam phishing email impersonating Disney+ and claiming that the recipient’s subscription would automatically renew. The inflated price of $49.99 would also be alarming to anyone familiar with the service whose basic rate is just $7.99. A phone number was provided for “cancellation”.
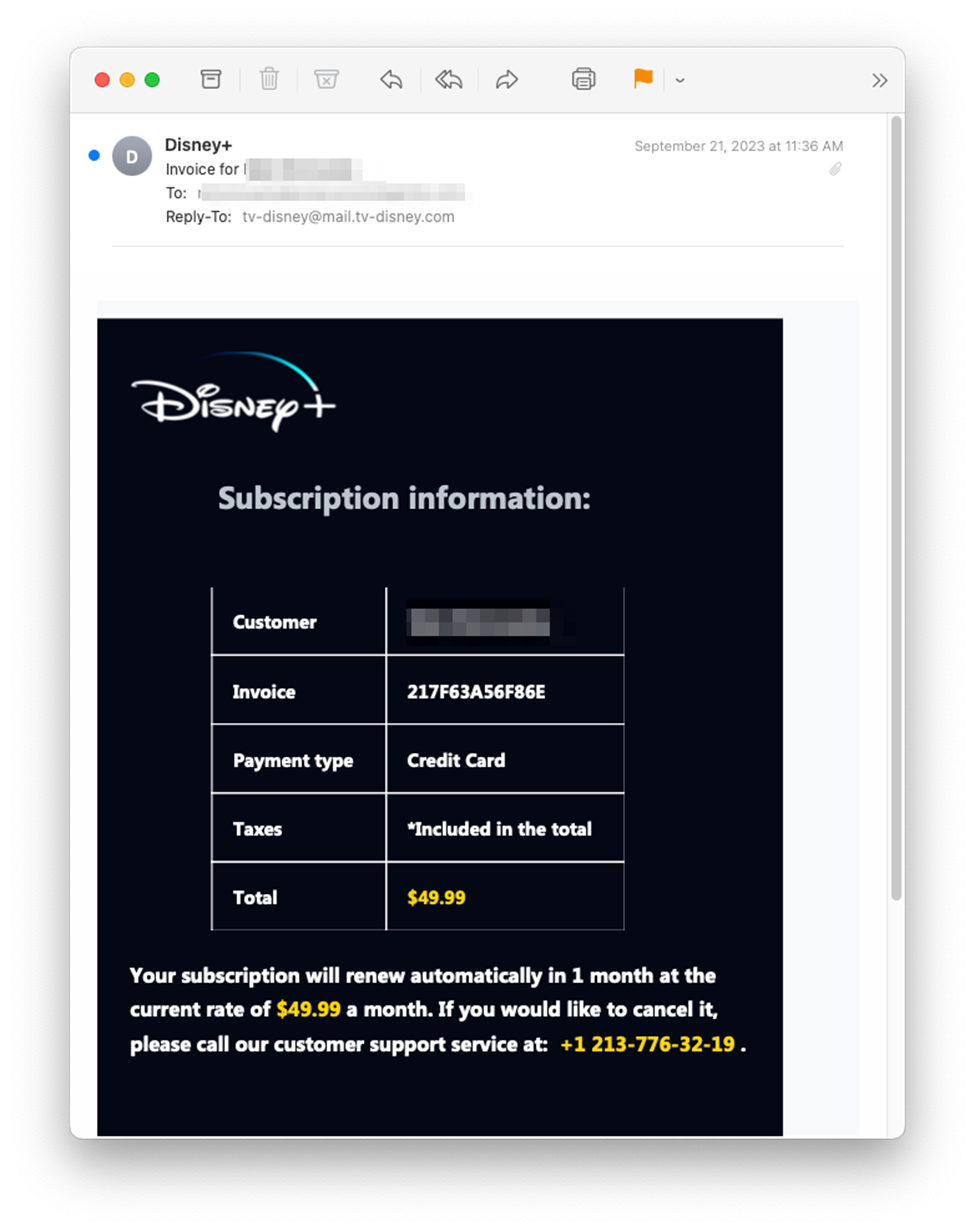
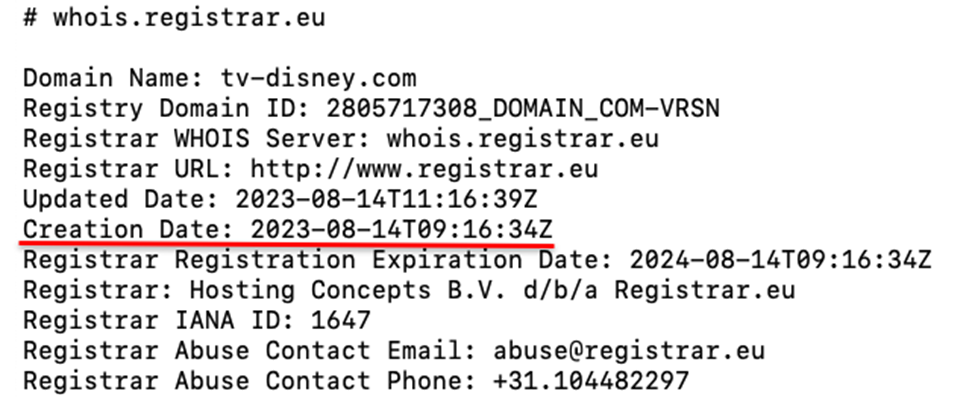
It’s interesting to note that all these emails originated from tv-disney[.]com, a clever and convincing look-alike domain. These newly created domains are able to pass standard email authentication (SPF, DKIM, and DMARC). Also, because they were brand new, the domains represented zero-day vulnerabilities – meaning they had never been seen before and did not appear in threat intelligence feeds commonly referenced by legacy anti-phishing tools.
INKY quickly discovered this look-alike domain had been created one month prior to the receipt of the phishing email.
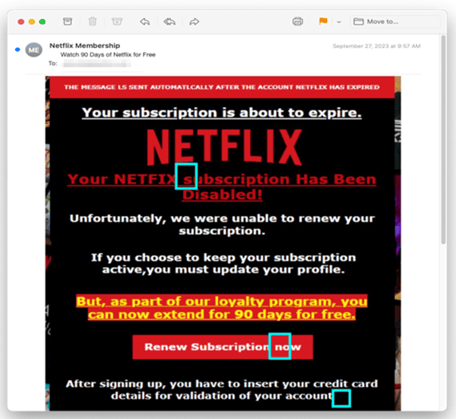
Phishers Impersonating Netflix Deliver a Malicious Link
There were about 75 million Netflix subscribers in 2022.4
The last of the three streaming phish examples is a bit more traditional. Cybercriminals behind this scam delivered a malicious link to their would-be victims. As with the others, it all started with a phishing email. Disguised as Netflix, the email claimed recipients needed to update their profile to keep their subscription active.
The email itself email originated from Walrusglycogenesis[.]com, which is a phisher-controlled domain created in 2022. A closer look reveals inconsistencies in the message – is my account about to expire or has it been cancelled? You’ll also notice that the design of this phishing threat looks more like an ad for a horror film than it does a professional communication. Still, it will press the panic button of plenty of readers.
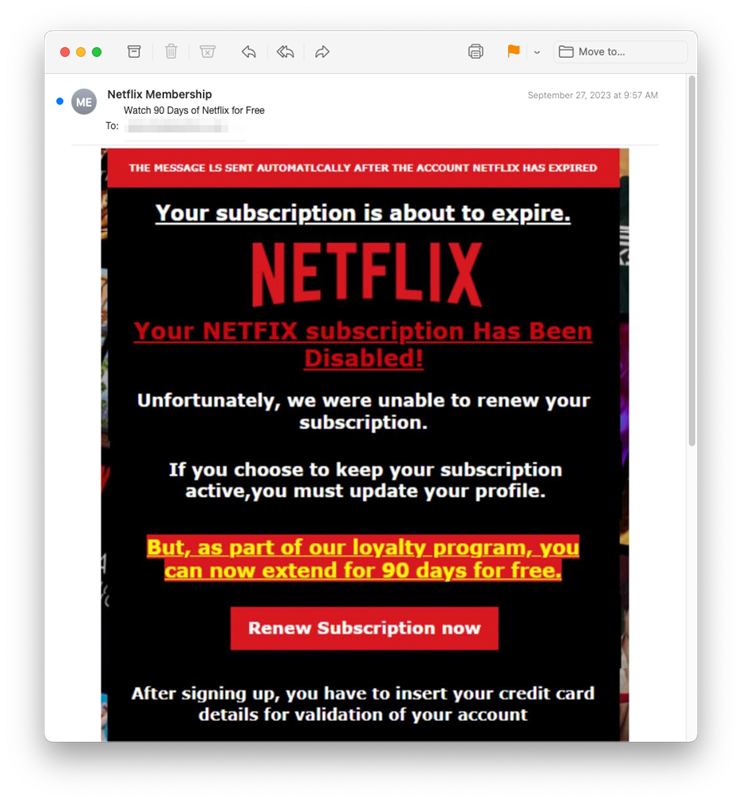
Those who click the link are taken to a malicious site that impersonates Netflix and is set up for credential harvesting.
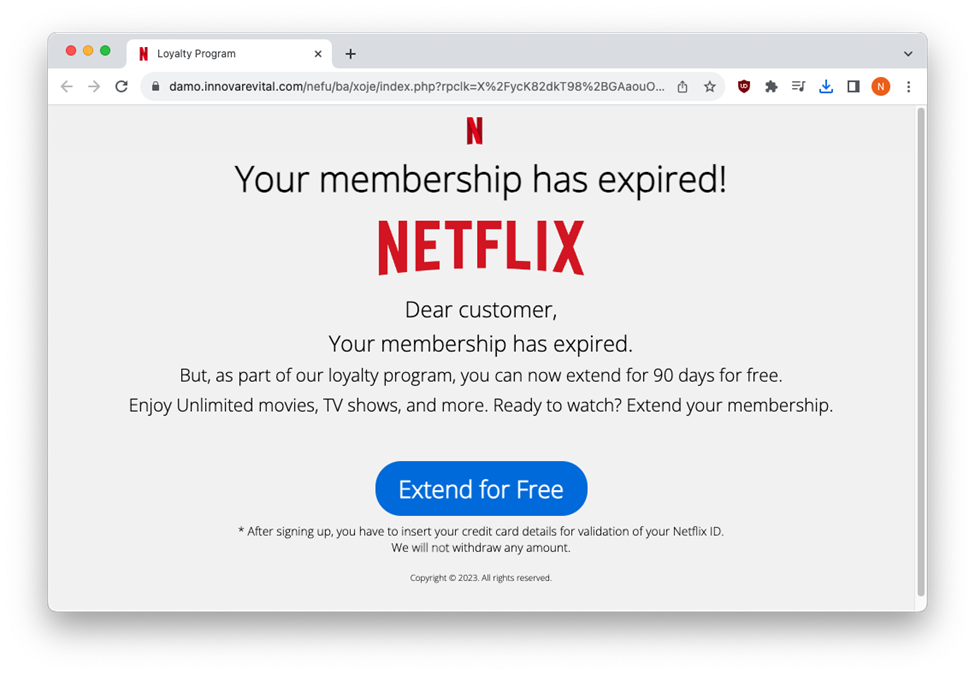
Clicking on the blue “Extend for Free” button opens a form that asks for personal information.
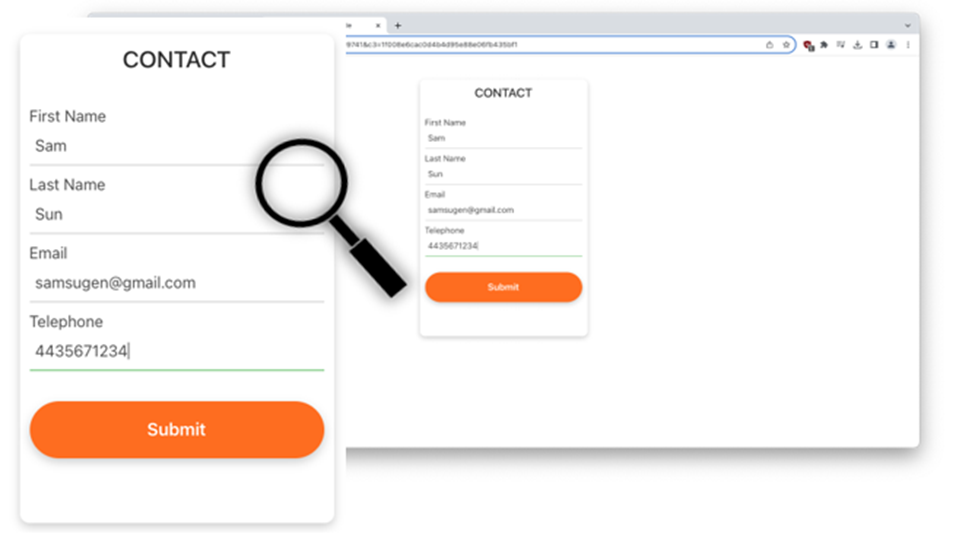
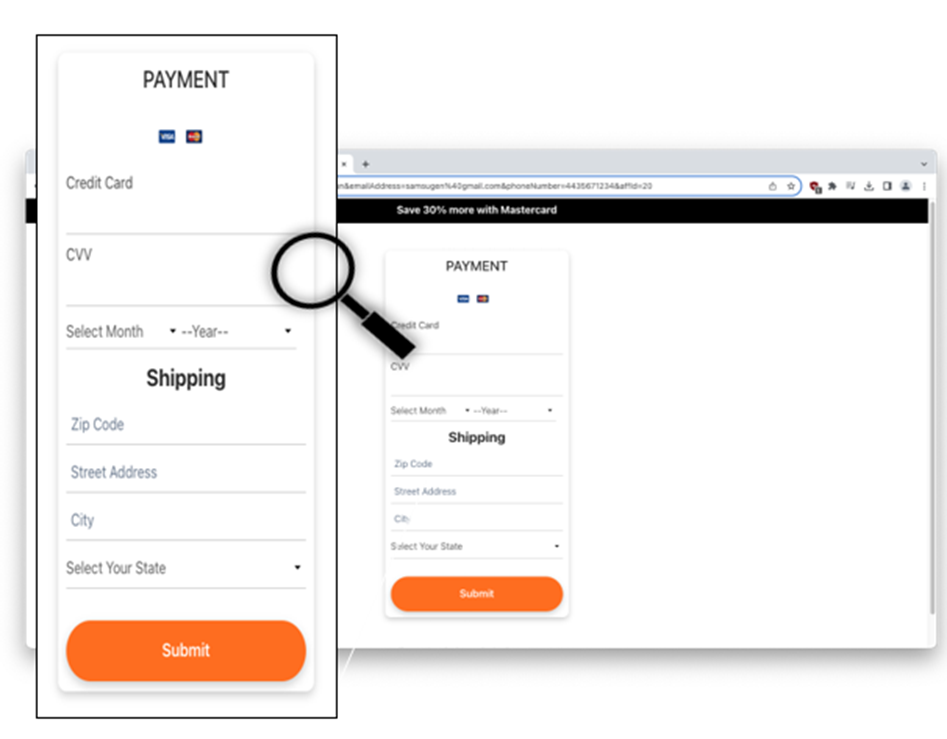
Then, clicking the orange “Submit” button takes you to a form that harvests credit card details.
A Word from the Grammar Police
Hollywood writers would never make the same mistakes as those found in your average phishing email. A common mistake cybercriminals make is not recognizing their own poor grammar, spelling and capitalization inaccuracies, missed punctuation, and basic errors in usage. While many of these are overlooked by distracted or panicked victims, we like to point them out in an effort to make everyone a little more phishing-conscious. Grammatical errors should be especially rare in instances of brand impersonation since sizable companies like Netflix, Disney, and Paramount have their own writing and editorial teams helping to ensure each customer communication is clear and professional. Below are a few examples.
Recap of Techniques
There were a number of common phishing techniques used in the Ring phishing scam.
- Brand impersonation — uses company logos and trademarks to impersonate well-known brands in order to make an email or malicious site look more legitimate.
- Threat of financial loss — creates a cognitive dissonance in the mind of the recipient, who may be disoriented enough by the message to miss small discrepancies that could tip them off to the fraud.
- Time pressure — adds a sense of urgency to the potential loss, again steering the target away from doing a common-sense analysis of the situation.
- Vishing — impersonating a brand to steal information via a phone call.
Best Practices: Guidance and Recommendations
Fortunately, there are a number of simple things recipients can do (aside from adopting modern anti-phishing software) to stay safe.
- Take a closer look at a sender’s email address to confirm that the message comes from the branded company that seems to be sending it. Particularly when an email triggers a sense of dread and urgency, looking at the sender’s address can quickly put those fears to rest.
- Guard your sensitive information. Even if the recipient makes the phone call to the fake sender, it is critical never to give sensitive personal information (e.g., banking information, social security number, date of birth) over the phone.
- Type don’t click. Don’t follow links, instead just typing the retail web site address directly into a browser, going to the real website, and viewing order history, which will likely not include the one referenced in the fraudulent email.
- Look up company numbers. It is unwise to call any phone number given in an unsolicited email. Anyone wishing to call a company should use the number on the firm’s official site.
- Guard your device. In this situation, remote access to the recipient’s device should not be granted, as it is not needed to receive a refund or rectify an issue.
- Remember, urgency is a phishers best friend. When you feel rushed over an email you recently received, it could be a signal to slow down and pay attention.
Of course, the best way to prevent phishing attacks is with the help of a third party. INKY provides the most comprehensive malware and email phishing protection available. INKY is also the only behavioral email security platform which means not only do we block phishing attempts, we also coach users to make safe decisions – everywhere, all the time.
Find out what INKY can do for you. Request a free demonstration.
----------------------
INKY is an award-winning, behavioral email security platform that blocks phishing threats, prevents data leaks, and coaches users to make smart decisions. Like a cybersecurity coach, INKY signals suspicious behaviors with interactive email banners that guide users to take safe action on any device or email client. IT teams don’t face the burden of filtering every email themselves or maintaining multiple systems. Through powerful technology and intuitive user engagement, INKY keeps phishers out for good. Learn why so many companies trust the security of their email to INKY. Request an online demonstration today.
1Source: www.cloudwards.net/streaming-services-statistics/
2Source: www.statista.com/statistics/296345/us-consumer-spendings-on-digital-entertainment-by-type/
3Source: https://variety.com/2023/tv/news/paramount-plus-subscriptions-77-million-2022-1235524323/
4Source: www.comparitech.com/blog/vpn-privacy/netflix-statistics-facts-figures/



