Have you ever lost your wallet? Even if you just think you have, your heart immediately begins to race, and you’re driven to act as quickly as possible to recover what is yours…before it’s too late. In this latest phishing scheme, hackers are capitalizing on the universal panic they know sets in, whether your wallet is Vuitton or virtual.
A Few Terms
If you’re new to cryptocurrency, there are a few things you should know.
COINBASE: Coinbase is a <relatively> secure online platform for buying, selling, transferring, and storing cryptocurrency.
PRIVATE KEYS: Account holders have their own personal Coinbase Wallet where passwords, known as private keys, are stored. These private keys prove your ownership of your digital money and allow you to make transactions. Without your private keys, you lose access to your cryptocurrency.
RECOVERY OR SEED PHRASE: When your Coinbase Wallet is first set up a recovery phrase is automatically generated. The recovery phrase (also called seed phrase) is a string of 12 to 24 simple words that will unlock your wallet, along with the private keys associated with the cryptocurrency in your wallet.
The Phishing Lure
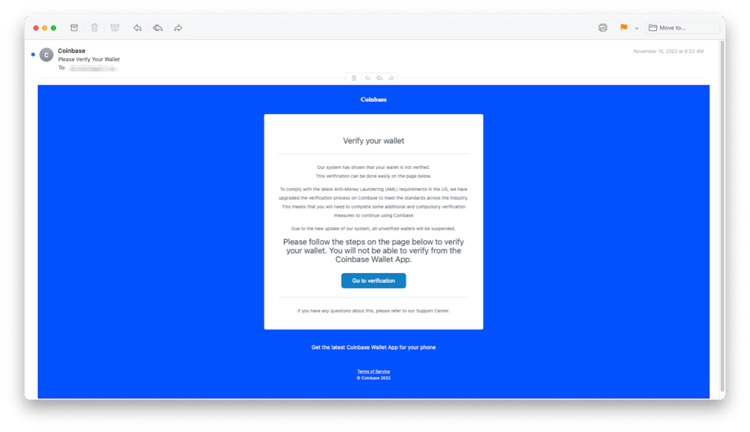
With more than 108 million customers, Coinbase was a great option for an elaborate multi-step phishing attack that leveraged a reputable web development platform to harvest credentials in order to gain control of the victims’ cryptocurrency. To lure victims in, bad actors sent a Coinbase branded phishing email that informed readers of the company’s newly upgraded account verification process. To continue using Coinbase and keep their wallet from being suspended, users needed to verify their account information.
After clicking on the “Go to verification” button within the email, victims were taken to phishing site hosted on fleek[.]co, which is a highly reputable web development platform that offers free personal accounts with no credit card required (characteristics that phishers appreciate).
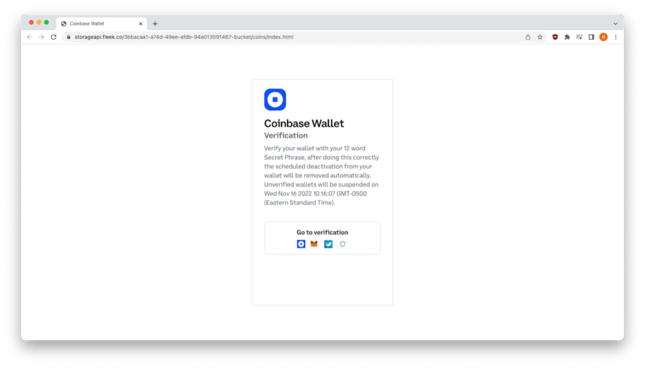
The fake Coinbase page informs customers that they will need to enter their 12-word “Secret Phrase” (wrong term, which we’ll cover later) to verify their account and stop the scheduled deactivation. This is the main goal – capturing the very credential that controls access to all of the victim’s cryptocurrency. The cybercriminals even go so far as to share the exact date and time of the impending account deactivation.
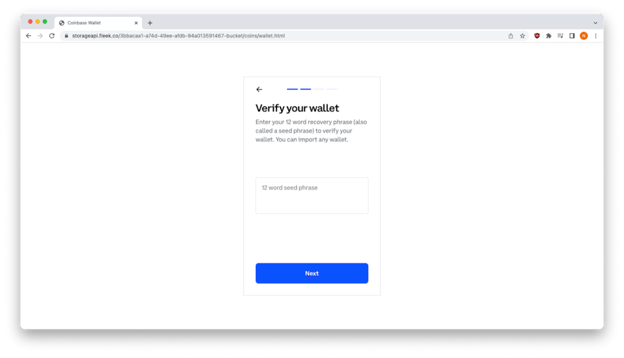
Finally, victims are guided to the page where they would enter their recovery phrase. For anyone who did give up their recovery phrase, it was “game over”. Even the Coinbase website provides a warning that references someone who lost hundreds of millions of dollars in bitcoin as a result of losing their recovery phrase.
Sharpening Your Phish Sighting Skills
Professional corporations are known to employ teams of talented writers and editors. They have style guides to help ensure communications are always on brand, and their processes make certain that before an email gets to a customer, numerous people have proofed and approved it. Especially in cases like account suspension, the communication must be precise and clear.
We have to hand it to this group of phishers, they did a nice job with the language in this threat. And because it lacked the types of obvious grammatical errors we have come to expect from phishing emails, other clues could more easily be overlooked. Still, if you zero in or do a little investigating on the Coinbase website, you might uncover some red flags. Our hope is that sharing these details will help you gain a better eye for catching them.
Initial Email
- The spacing and mixed font sizes used in the message do look rather sloppy, though probably not enough to be an obvious alert. However, there is no company logo on the page – just the word “Coinbase” at the top of the message. When Coinbase uses their logo as a header it is in their brand blue and in all lowercase letters. A quick search for “Coinbase logo” is one way to check.

- There are two instances where the users are instructed to references “the page below.” However, there really is no “page below”. Readers should be instructed to use the link below.
- At least one sentence is missing a period.
- While we don’t encourage people to click on random links, sometimes just hovering will show you where they lead. The initial email’s primary purpose is to get victims to click on the “Go to verification” button. However, to look authentic, they also added a “Terms of Service” link at the bottom. The problem is it also takes you to the verification page they want you to visit.
- At the bottom you’ll see “Get the latest Coinbase Wallet App for your phone”. That is a simple sales opportunity any company might include and yet it doesn’t have a link, which is a wasted opportunity.
- Also, toward the bottom is the statement, “If you have any questions about this, please refer to our Support Center.” You will rarely see “about this” in a professional communication. It’s too vague and reads poorly. Instead, it might say, “If you have any questions about your Coinbase account or the required verification process…” It’s also poor business etiquette to suggest they refer to your Support Center without providing a way for them to do so. Adding a link or a phone number would have been more appropriate.
- When it comes to clickable buttons, the text is usually in title case to give it symmetry. The exception would be if there is punctuation in the wording. So, in this case editors would have corrected “Go to verification” to “Go to Verification”.
Secret Phrase Instructions
- The biggest mistake on this page is calling referring to users’ recovery or seed phrase as a “Secret Phrase”.
- Another big mistake is assuming all users have 12 words in their Secret Phrase. The Coinbase website clearly states recovery phrases contain between 12 and 24 words.
- Other parts of the message on this page were also sloppy.
- The first sentence doesn’t entirely make sense and should be two separate sentences.
- “12 word” should be hyphenated.
- “after doing this correctly” is awkward. It should say, “After successfully verifying your Coinbase Wallet, the scheduled deactivation will automatically be removed.”
- There are only two sentences in the copy and yet one says an account will be suspended and the other warns of a deactivation. Which is it? A good editor would have spotted this inconsistency.
- Promoting a sense of urgency is a tell-tale sign of a phishing email. In this case, the phishers give a very precise (to the second) time for this account to be suspended. It happens to be less than 24 hours after the email was sent. Can you imagine the legal problems a company could face if they suspended someone’s account funds with less than a day’s notice, using just a single email notification? Had it gone to their junk folder, the email would never have been seen.
- Coinbase does have a separate logo for their Coinbase Wallet, which the phishers were smart to include on this page.
Final Verification Page
- While this page correctly references a recover and seed phrase, it’s still inconsistent with the prior messaging.
- The major flaw on this page can be found in the last sentence. It says, “You can import any wallet”. While the wallets from other vendors can be imported into your Coinbase Wallet, if the company is about to deactivate your account they certainly wouldn’t be concerned with wallets from other vendors or recovery phrases outside of the one they are threatening to deactivate.
A Final Word
Let’s summarize some of the tactics used in this Coinbase cryptocurrency credential harvesting phishing attack.
Recap of Techniques
- Brand impersonation — uses elements of a well-known organization to make an email look as if it came from a legitimate source.
- Data or credential harvesting — collecting personal data under false pretenses.
- Threat of financial loss - creates a cognitive dissonance in the mind of the recipient, who may be disoriented enough by the message to miss small discrepancies that could tip them off to the fraud.
- Time pressure - adds a sense of urgency to the potential loss, again steering the target away from doing a common-sense analysis of the situation.
- Multi-Step process – having the victim go through multiple steps makes the email feel more legitimate as compared to a typical phishing email.
Best Practices: Guidance and Recommendations
- Carefully inspect the sender’s email address. This email claims to be from Coinbase but was sent from a non-Coinbase domain.
- Hover over links to see where the link goes. In this case, the link goes to fleek[.]co instead of a Coinbase site.
- Coinbase (and other cryptocurrency wallets) will never ask for your recovery phrase. It should only be used to restore wallet access and can’t be used for verification.
Money is powerful. Getting money obviously pushes people into a life of crime. Losing money – or at least the threat of it - can quickly lead us into making snap decisions. Hopefully this INKY Fresh Phish will instill a new rule of thumb; If an email combines urgency and money, it’s worth your while to take a deep breath and pause.
To really catch phish two things are required. First, you must do your own part to recognize the signs of a phishing email and make intelligent choices for your own safety and for the safety of your organization. Secondly, realize that you can’t do it all on your own and ensure you have an expert at your side.
INKY is the behavioral email security platform that blocks threats, prevents data leaks, and coaches users to make smart decisions regarding the safety of their email. Like a cybersecurity coach, it signals suspicious behaviors with interactive banners that guide users to take safe action on any device or email client. IT teams don’t face the burden of filtering every email themselves or maintaining multiple systems. Through powerful technology and intuitive user engagement, INKY keeps bad actors out for good. Start a free trial or schedule a demo.
INKY is an award-winning, behavioral email security platform that blocks phishing threats, prevents data leaks, and coaches users to make smart decisions. Like a cybersecurity coach, INKY signals suspicious behaviors with interactive email banners that guide users to take safe action on any device or email client. IT teams don’t face the burden of filtering every email themselves or maintaining multiple systems. Through powerful technology and intuitive user engagement, INKY keeps phishers out for good. Learn why so many companies trust the security of their email to INKY. Request an online demonstration today.


