As people begin to contemplate returning to work in a physical office, phishers are thinking about new ways to exploit, through phishing emails, workers’ desire for accurate information about COVID-19, vaccines, and related work policy changes. In late winter, a wide swath of INKY users received phishing emails that impersonated their employers and used various COVID “lures” to install malware or harvest credentials. Most of these exploits used stolen platforms or open redirects to deliver phishing content. Most of these exploits used stolen platforms or open redirects to deliver phishing content.
The following examples give instances of such emails, all of which were caught by INKY’s anti-phishing technology.
Bogus Survey
One common tactic used by phishers is to run an algorithm that extracts the recipient’s domain name and puts it next to the term “HR."
Here is a message that appeared to come from the HR department, supposedly asking employees to take a survey about a topic of great interest: their willingness to get a COVID-19 vaccine. The email was replete with company-specific information.
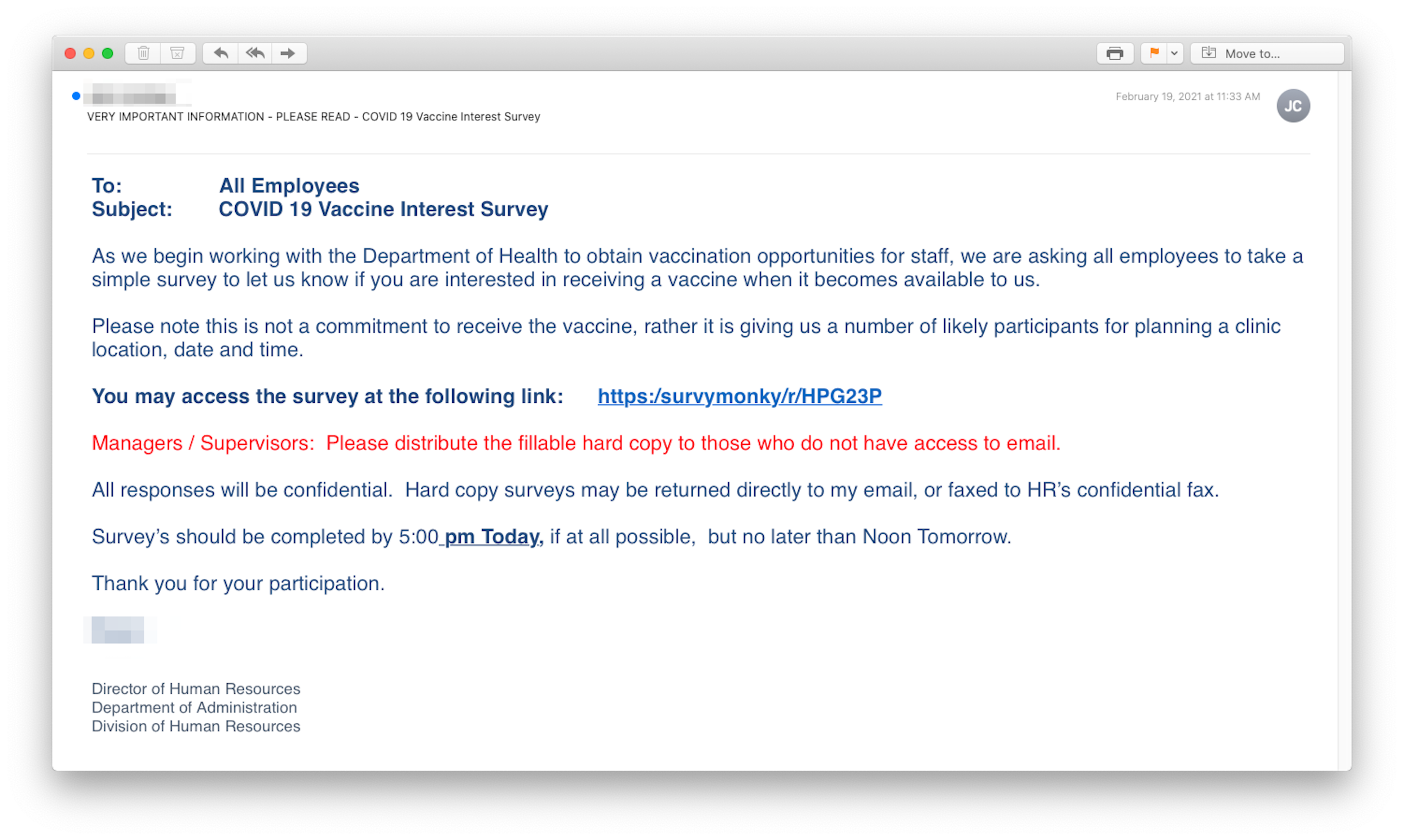
But a very close reading (which most recipients would be unlikely to do) would have revealed that the URL of the supposed survey did not actually go to “surveymonkey.com” but rather to “survymonky/r/HPG23P,” a misleading URL that led to a credential harvesting site on a hijacked domain.
Although many phishing attacks originate in foreign countries, this one came from the United States. Needless to say, the real senders didn’t actually care about employees’ opinions.
Not Your Boss's Boss
When the CEO speaks, most people listen. And the phishers know an employee’s general respect for authority will help them deliver a toxic payload. In this example, the phisher used the employer’s name and logo to give the message some credence.
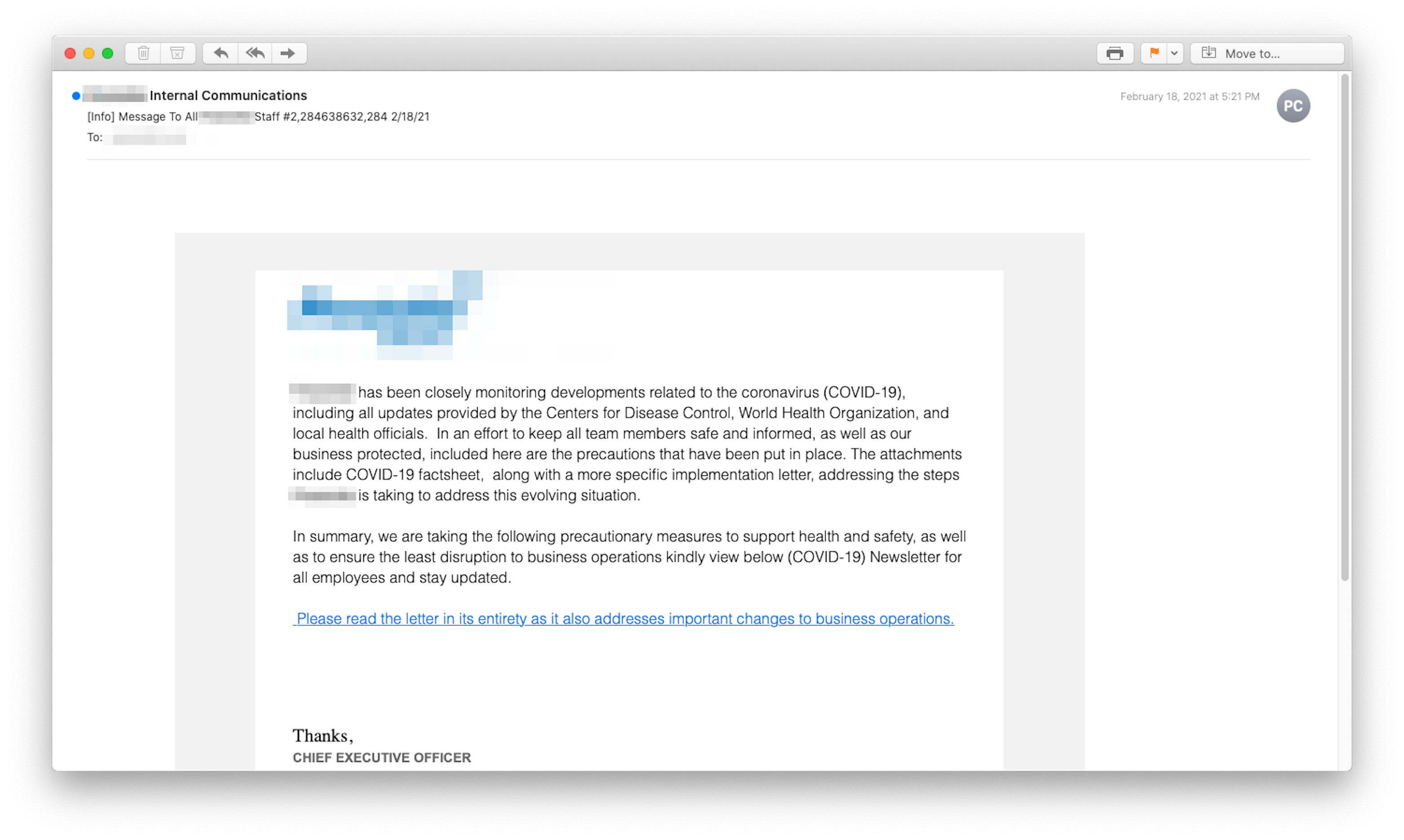
However, rather than coming from the CEO, this deceptive phishing email came from Spain. And, embedded within it was a link that used Google's open redirect capability to send those who clicked through to a malware injection site or a credential harvesting operation. The cybercriminal was able to exploit a weakness that some legitimate websites like Google use that allows users to input parameters in a link that redirects to other sites. What the user sees is “google.com” followed by a long URL path. Even if the recipient were to scrutinize the URL, all they'd see was a good-looking Google redirect. What could possibly go wrong?
Rule Change for the Worse
This next one, apparently an internally sent missive, purported to come from someone in "our department," a vague moniker that could refer to HR or to any operating department. That vagueness helps cybercriminals cast a wider net. The email seemed to lay out new COVID-19 rules to be followed by department members.
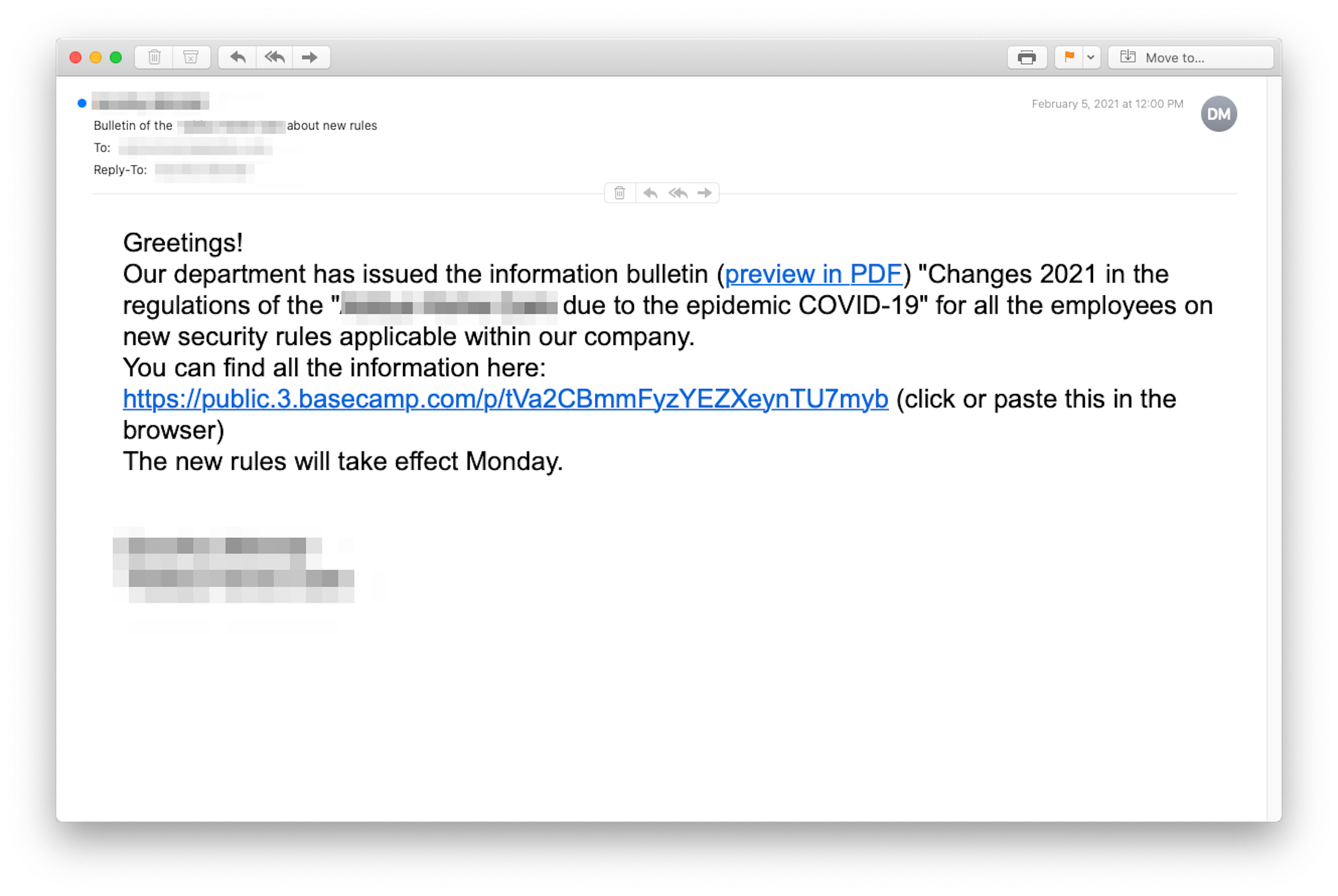
However, this phishing email didn’t originate in "our department" but in the Netherlands. The link did lead to a project-management tool (basecamp.com), but the specific site on basecamp had been hijacked by the hackers and served as host to a malware injector or credential harvesting page.
Respondents Threatened for Noncompliance
Reasonably well written, this email, apparently from the human resources department at the target company, actually came from phishers located in the United Kingdom. There are elements that might strike the recipient as strange. For example, the phrase "recuperating favorably” is a bit off. Noncompliance is spelled "non-compliance.” And "these guide and policies” has an agreement-of-number problem.
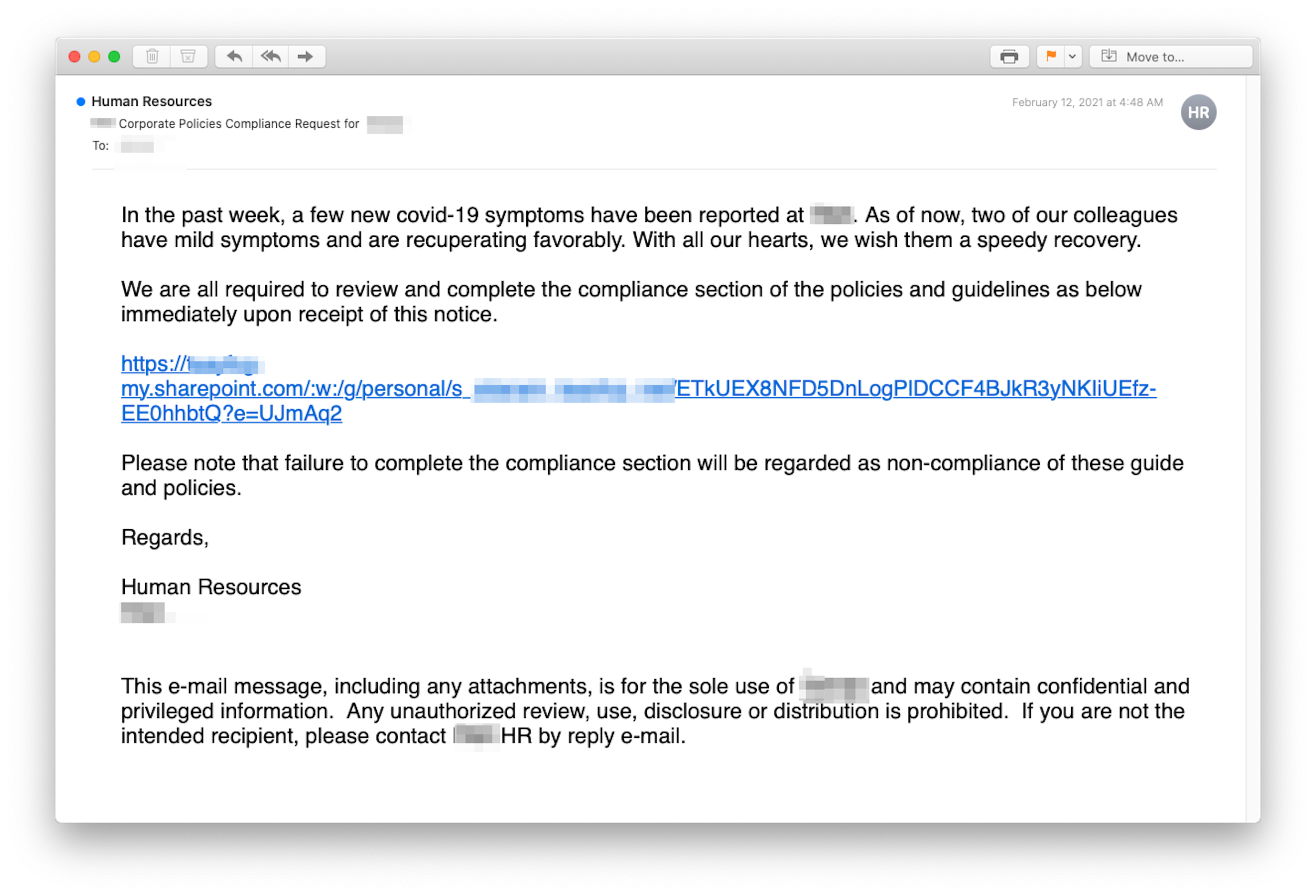
But otherwise, it’s a pretty good fake, including the legitimate SharePoint link embedded in the email. The problem with the link was that it led to a real but hijacked SharePoint site that was turned into a credential harvesting operation.
As with Pandemic, You Can’t Be Too Cautious
Nearly 60% of businesses that closed during the pandemic will never reopen, making returning to the office an achievement in and of itself. 1 And yet, even with vaccine availability and scaled-back restrictions, reopening your business alongside a pandemic is no easy task. And while maintaining social distancing and disinfecting protocols may be at the top of the checklist, but you can’t overlook what lurks just behind the computer display.
According to the FBI’s 2020 Internet Crime Report2, the number of complaints rose 69% during the year of the pandemic, with the largest reported losses in history — a whopping $4.1 billion. Business email compromise phishing schemes continue to be the costliest with adjusted losses of about $1,8 billion. And sadly, in terms of types of cybercrime, phishing incidents more than doubled in the past year. 2
Of course, we would be remiss if we didn’t mention that even if you’re one of the many companies remaining remote after the pandemic, you’re still at great risk of an email phishing attack. As the examples above hopefully prove, cybercriminals are willing to go to extremes in order to trick employees into making the types of simple human errors that cost companies millions every year. All it takes is one click.
In 2020, the FBI’s Internet Crime Complaint Center received 28,500 complaints related to COVID-19 and many of the same opportunities are still very much in play. 2 So, as part of your “back to the office” protocol, remember that when it COVID-19 phishing threats, INKY acts like a vaccine — keeping your business safe in the office, remotely, and when using mobile devices.
----------------------
INKY® is the emerging hero in the war against phishing. An award-winning cloud-based email security solution, INKY® prevents the most complex phishing threats from disrupting or even immobilizing your company’s day-to-day business operations. Using computer vision, artificial intelligence, and machine learning, INKY® is the smartest investment you can make in the security of your organization. INKY® is a proud winner of the NYCx Cybersecurity Moonshot Challenge and finalist in the 2020 RSAC Innovation Sandbox Competition. Learn more about INKY® or request an online demonstration today.
1Source: https://nypost.com/2020/09/17/majority-of-covid-19-business-closures-are-permanent-report/
2Source: https://www.ic3.gov/Media/PDF/AnnualReport/2020_IC3Report.pdf


