The Russian attack on Ukraine has the news cycle in its grip. And since, even on a slow day, phishers weave the news into their lures, it’s no surprise that they have jumped on this story. It has all the right characteristics for baiting a snare: a high level of drama, strong emotions, and a natural attack flow that takes advantage of Westerners' desire to make donations to the people of Ukraine.
Thus, within a week of the initial invasion, INKY began to detect Ukraine-themed phishing attacks. The slickness of the attacks suggests that this is not this group’s first rodeo.
Because this particular scam involved cryptocurrencies, INKY engineers were able to track transactions executed to date and determined that none of our customers were tricked into making donations, and, further, that no donations from anywhere have been made on the fake site.
Quick Take: Attack Flow Overview
- Type: phishing
- Vector: email sent from U.S.-based virtual private servers, link to slick donation website
- Payload: cryptocurrency theft
- Techniques: VIP impersonation
- Platform: Microsoft 365
- Target: Microsoft 365 users
The Attack
INKY customers based in the United States received phishing emails that impersonated Ukrainian President Volodymyr Zelenskyy.
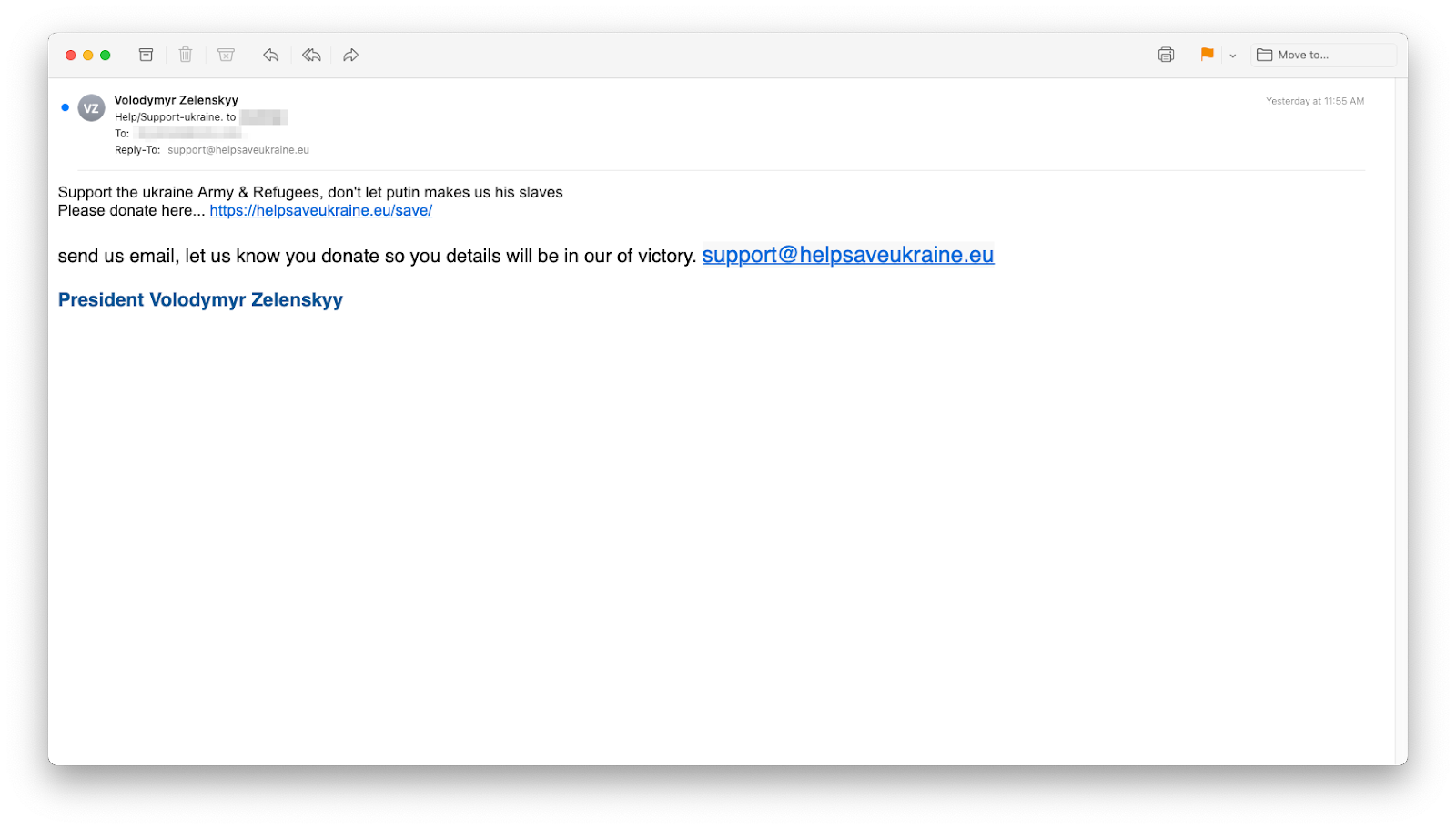
Not the real Zelenskyy
To evade geographical filters, these emails were sent from U.S.-based virtual private servers. With slightly off capitalization and punctuation, the simple text could easily have been created by a non-native-English speaker. The apparent Zelenskyy (spelled the correct Ukrainian, as opposed to Russian, way) asked recipients to support “the ukrainian Army and Refugees” by visiting helpsaveukraine[.]eu/save/
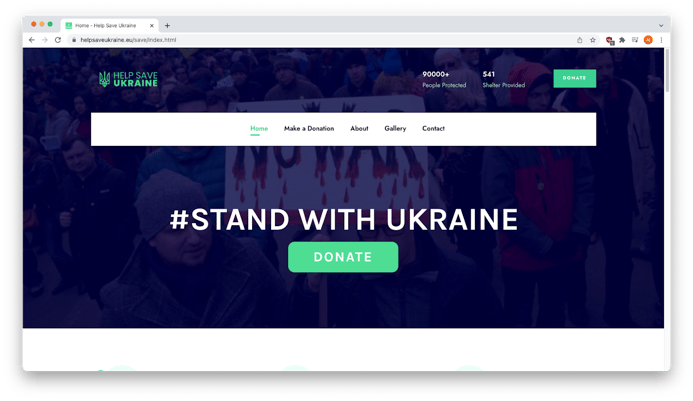
A strong landing page
The landing page of the linked website was impressively professional, well designed, and functional with a clear call to action, a green “Donate” button.
However, clicking on the “About” tab turned up a number of indications that the site was hastily erected, a fraudulent page designed for a phishing exploit.
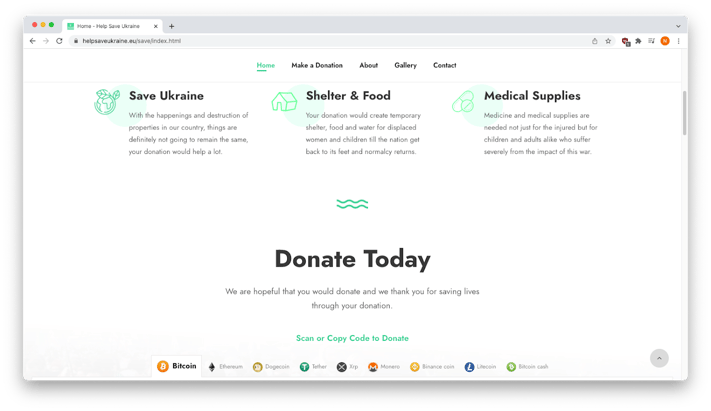
Potemkin inside pages
For example, the “How are We?” section (which was probably meant to be “Who We Are”) began with “Text box item sample content,” and all sections (“How are We?”, “Tackling Poverty”, “Make Big Impact”, “Unite The Society”) had the exact same text (“Charity law within the UK varies among England….).
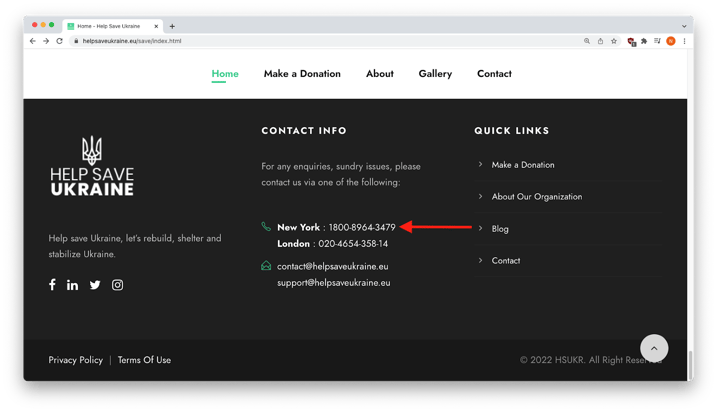
Bogus contact information
Scrolling to the bottom of the home page revealed a contact phone number said to be in New York, but with the wrong number of digits, indicating that it was likely created by non-US phishers.
On the bottom right of the home page, was a copyright of “HSURK,” but there appears not to be any such company.
Clicking on the “Make a Donation” tab showed that the site was soliciting donations in cryptocurrency.

Make a donation in crypto
An analysis of blockchain transactions validated all cryptocurrency addresses as real.
The Bitcoin address had 0 transactions (indicating that no one was duped).
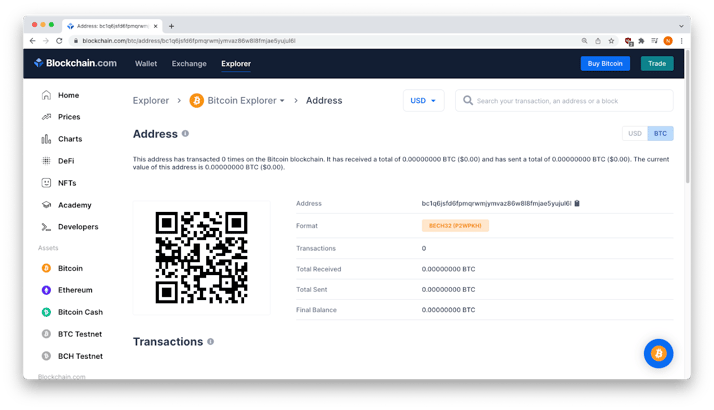
Real Bitcoin address
The Ethereum address had transactions from 2018, but none from 2022 (again, no one was duped).
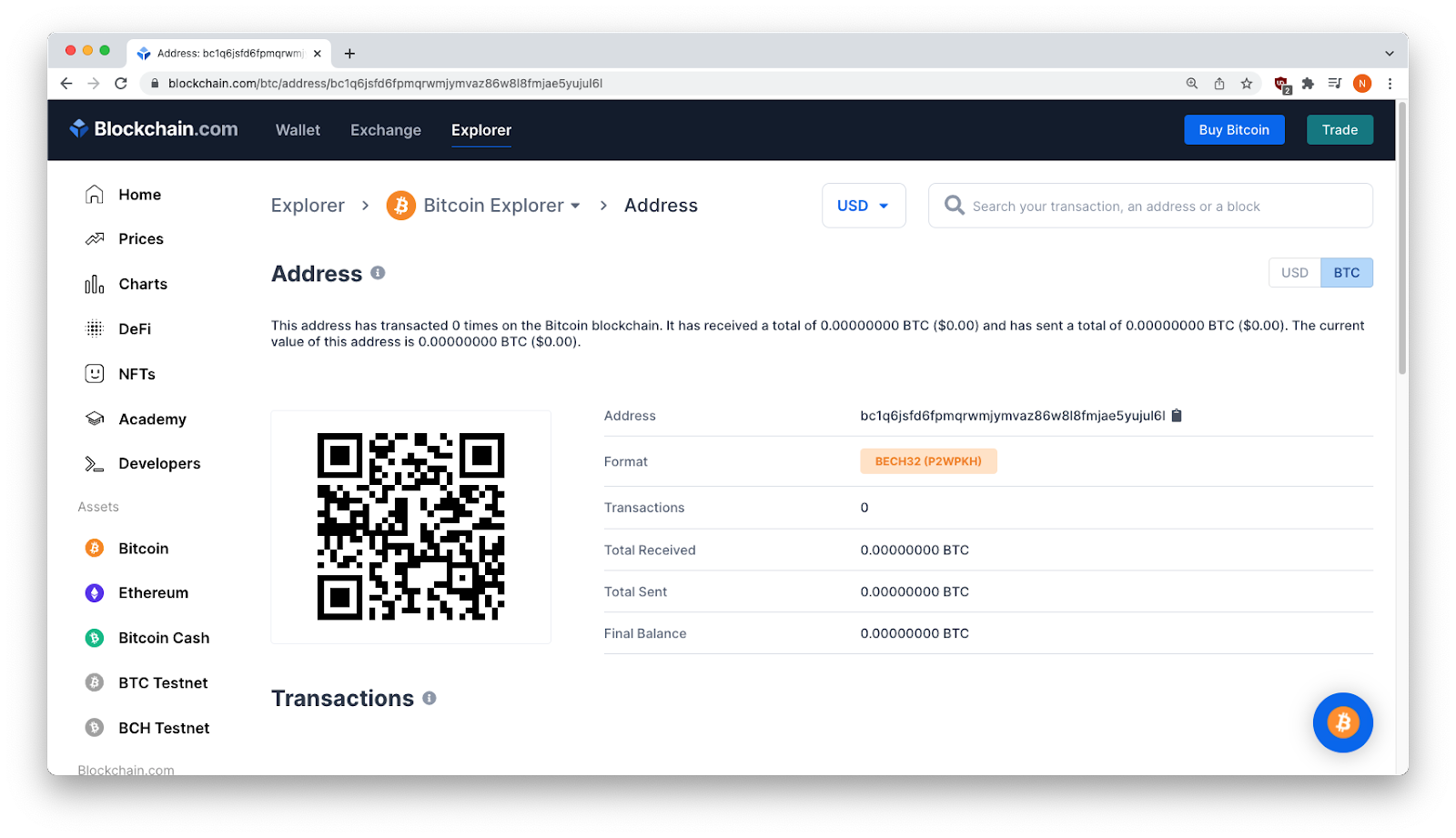 Real Ethereum address
Real Ethereum address
INKY received the first reports of this campaign March 7, and by the next day, the site had been taken down. But before it was removed, an INKY data analyst managed to grab a bunch of screenshots, presented here.
The site had a gallery:
Imagery with strong emotional appeal
Citizen soldiers
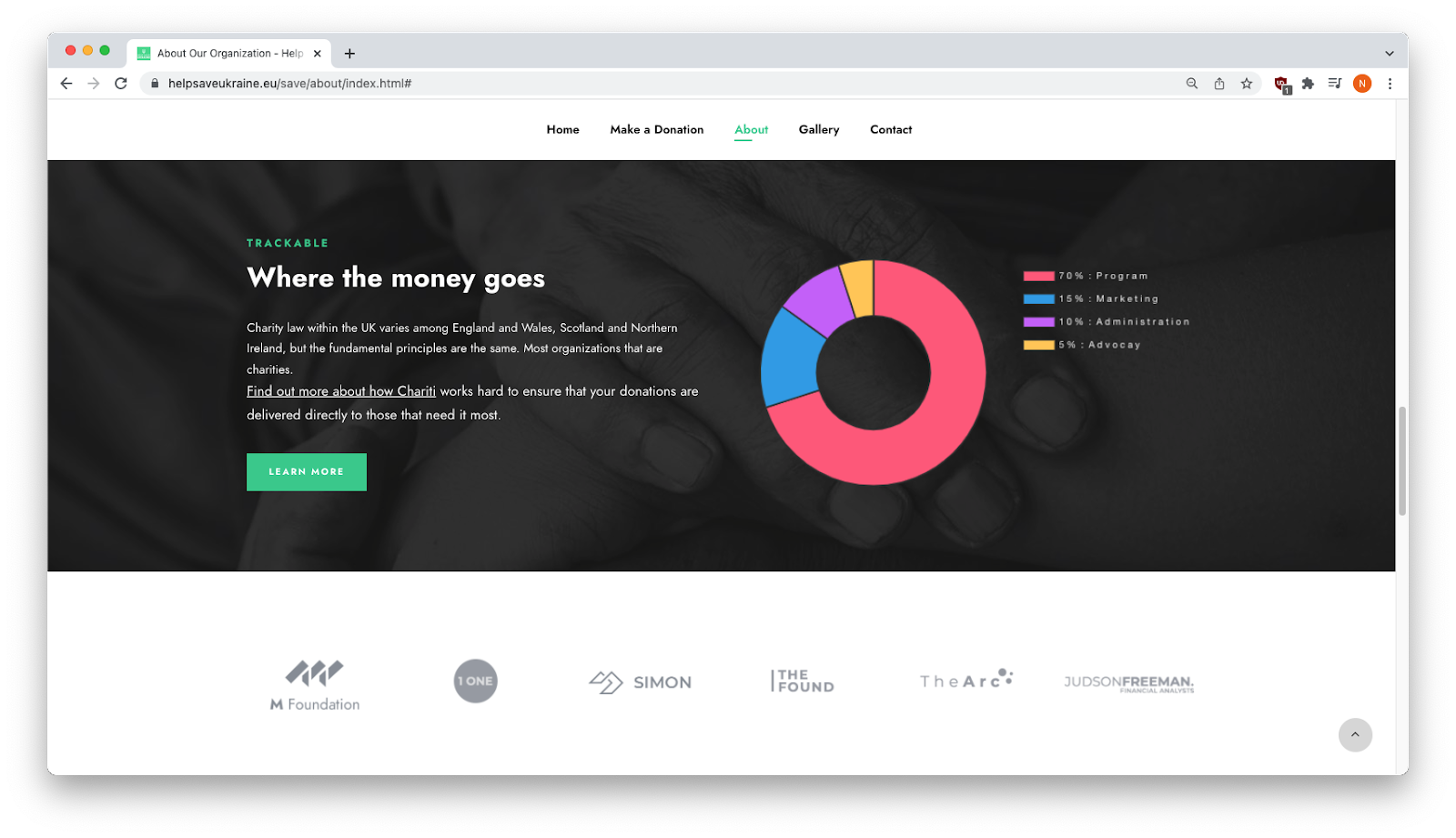
Where the money goes: a nice-looking but fake distribution graphic
More appeals
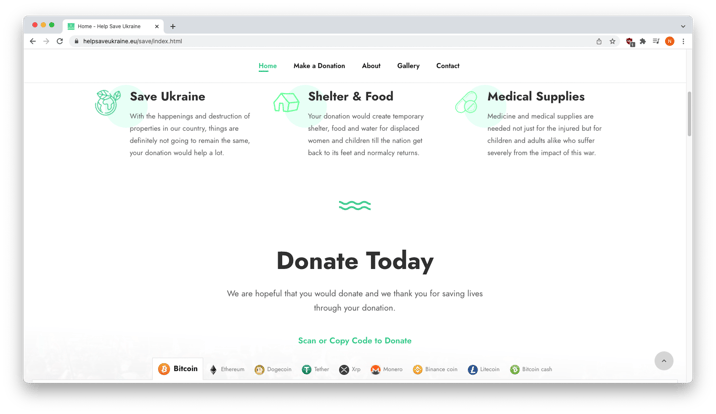
A call to action
Recap of Techniques
- VIP impersonation — uses elements of a well-known person to make an email look as if it came from them
- Phisher-controlled website — used to create a plausible landing for any victim who clicks through from the phishing email
- Cryptocurrency scam — involves tricking the target into legally transferring unrecoverable funds to accounts controlled by the phishers
Best Practices: Guidance and Recommendations
Double-check the sender’s email address. In this case, the sender’s email was spoofed to look like it came from the recipient’s domain: President-helpteam@[your domain].com.
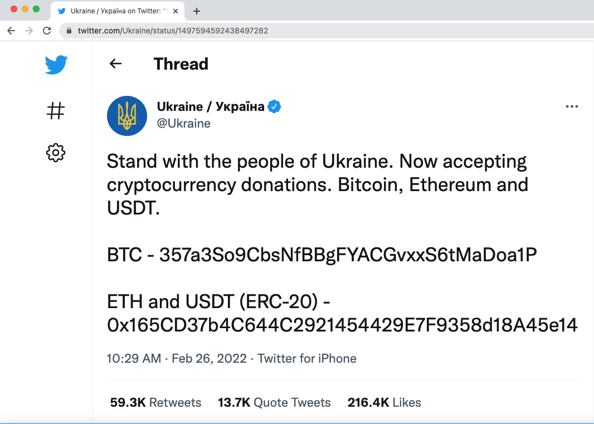
If someone would like to send help to Ukraine, the real Ukrainian government is actually accepting cryptocurrency donations, but make sure to transmit funds only to addresses found on Ukraine’s official Twitter handle:
Also, the website ukrainewar.carrd.co contains links to vetted, more-legitimate ways to help.
Learn more about INKY's response to the crisis in Ukraine.
----------------------
INKY is an award-winning, cloud-based email security solution developed to proactively eliminate phishing emails and malware while simultaneously providing real-time assistance to employees handling suspicious emails so they can make safer decisions. INKY’s patented technology incorporates sophisticated computer vision, machine learning models, social profiling, and stylometry algorithms to effectively sanitize emails, rewrite malicious links, detect and block security threats, mitigate sender impersonation, and more. Cost-effective and powerful, the INKY platform was developed for mobile-first IT organizations and works seamlessly on any device, operating system, and mail client. Learn more about INKY™ or request an online demonstration today.


