If a thief breaks a window in your house and steals things, you will notice the broken glass and what is missing quickly. If one of your team members clicks on a phishing attack email and give thieves access to your data, you may not find out for months.
The average breach goes undetected for 206 days. In some cases, it can take years to figure out. That’s a long time for crooks to have access to your data and plenty of time to do serious damage.
It Starts with A Phishing Email
Phishing attacks are the most common cause of system breaches. There’s no shortage of tricks the bad guys will roll out:
- Brand Forgery
- Domain Spoofing
- Malware and Ransomware
- Spear Phishing Attacks
- CEO Fraud
- Zero-Day Attacks
The best email security is one that prevents these nasty phishing emails from getting through to one of your employees in the first place.
Phishing Attacks Are Becoming More Sophisticated
We’ve come a long way from the Nigerian Prince that has millions of dollars to give away. Today’s scammers are running highly targeted and sophisticated phishing attacks.
Phishing kits are available on the dark web. These kits clone well-known websites and set up shop on temporary servers. They will look just like the real thing when someone clicks on the phishing email but grab the victim’s login credentials. Other attacks will be embedded in documents that are hosted on popular file-sharing sites with recognizable names.
Even well-trained employees have fallen victim to social engineering tricks. There is so much personal information available online for free that cybercriminals can find out a lot about someone without a lot of work. They can personalize these phishing attacks and make them look legitimate by using this personal information.
You Can’t Rely on Blacklists And Keyword Detection
The problem is that most built-in email security solutions, such as those used by Office 365, Exchange, and G Suite, rely on blacklists that do not provide enough protection. When an email arrives, it’s analyzed before it hits your inbox. It is compared to existing lists of previously detected threats. If it’s not on the list, however, it will make its way through.
Depending on blacklists alone is dangerous. Cybercriminals can easily change tactics or web addresses. By the time a threat shows up on the list, the damage may have already been done.
Another way to detect phishing attacks is by using content filtering. Keywords and common phrases that scammers use can trigger warnings and quarantines but simply won’t catch everything. Links can appear legitimate. Even anti-phishing software that traces links may not detect a malicious document or a cloned site waiting to steal credentials.
You Can’t Rely On Policies And Training
Western Carolina University has robust policies and guidelines on passwords, email, and internet security. So, when they did an email phishing test by sending out a simulated attack, they did not expect that 50 percent of the faculty and staff would violate the policies, or that 20 percent would click on the email link.
Despite training, people still click on links. In a similar test, 20 percent of the recipients clicked on links from an unknown sender even when they were aware of the potential problems. They admitted they were curious about what would happen. Emails that addressed the recipient by their first name had a 56% click rate!
Presenting genuine and malicious emails to groups consistently shows that people make poor decisions. People think they’re smarter than the scammers. This leads to overconfidence in detecting phishing emails.
Even when people know what to do, they still fail to employ proper security protocols to protect themselves. It’s become so common that they have a name for it: Security Fatigue.
Stop Email Phishing: What Works
You need blacklists, keyword detection, content filtering, email security policies, and training. However, these strategies alone will not stop your employees from clicking on phishing emails.
Your email security needs to start with a robust anti-phishing software solution that goes beyond these basic tactics.
A Better Solution
INKY integrates with your existing email and security platform to catch even the most sophisticated phishing attacks. INKY can see things other software misses. It catches the phishing attacks even before they get put on blacklists.
INKY educates users while protecting them. It scans links for potential threats and displays bold color-coded warning messages inside the body of the email that users will not miss.
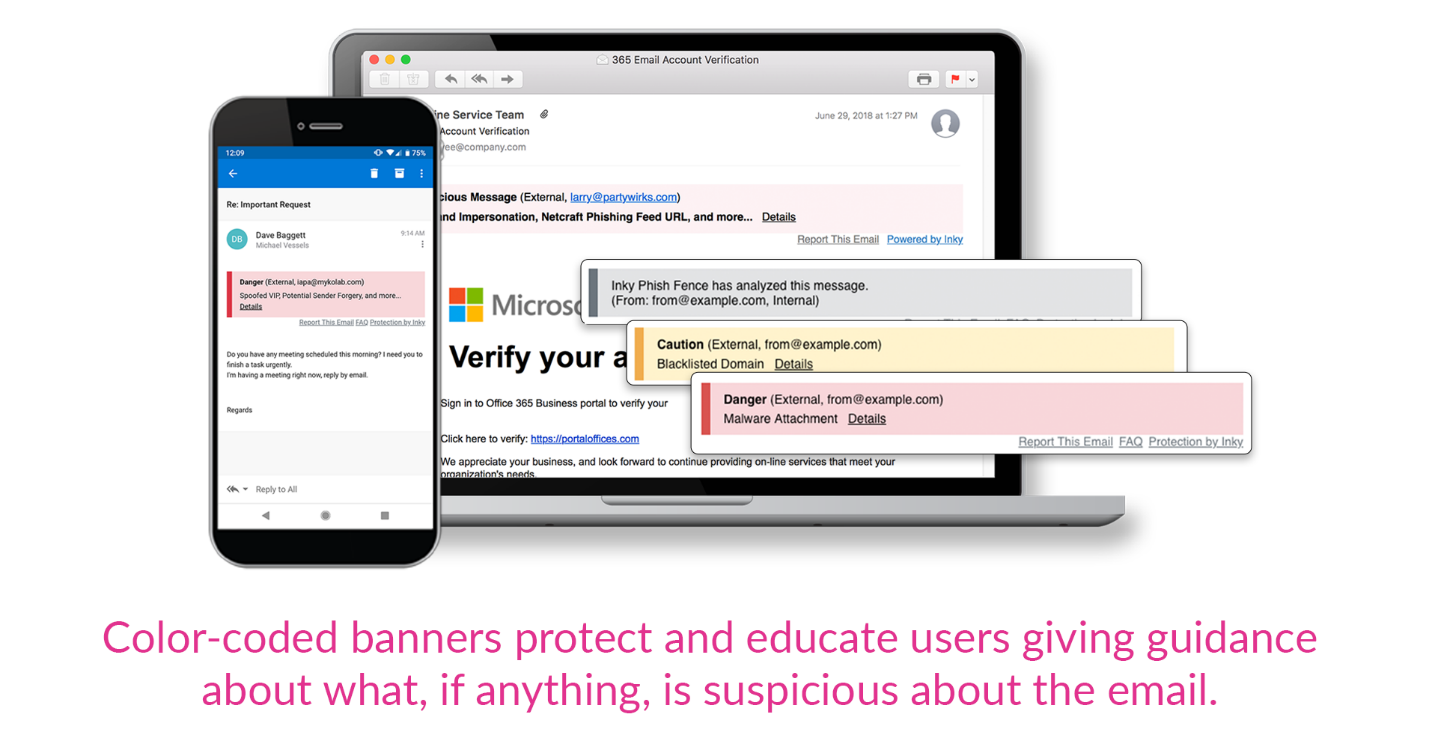
Using more than two dozen computer vision and machine learning algorithms, INKY can “see” email in a similar manner as a human email security expert would. This catches realistic-looking forgeries even when they come from high-reputation senders.
Get a demo of the INKY email security platform today.



