Would you have fallen for this Phishing Scam?
By Inky July 11, 2018 Catch Of The Day
Every day at Inky we see incredible examples of phishing scams. It never ceases to amaze us the lengths cyber criminals will go to steal. The FBI regularly reports that email phishing scams are a monumental (about 5 billion dollars!!) problem facing all business – across any industry. Here I have described for you one of the latest scams that Inky prevented from ever making it to one of our software user’s inbox.
The email message looked like this:
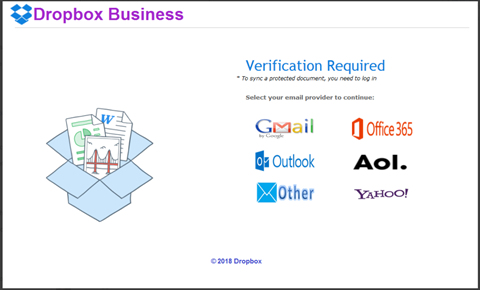
It really does look like it’s from Dropbox doesn’t it! And it made it through other email protection measures that our client also had in place. (SPAM and Malware filter)
The email said, “Verification Required … You need to log in” and provided several login options. The Dropbox logo looks spot on, and all the logos for the email login options – Gmail, Office 365, etc. – look real as well.
So how did Inky know this was Phishy?
Because Inky can “see” the email like a human would.
Using Computer Vision technology, Inky “saw” the Dropbox logo, and noted that this email claimed to be from the brand Dropbox. Inky knew that if the email was really from Dropbox, then it should come from an approved Dropbox domain. Inky instantly determined that this was not a Dropbox domain and gave this detailed warning in the Inky Phish Fence user friendly banner:

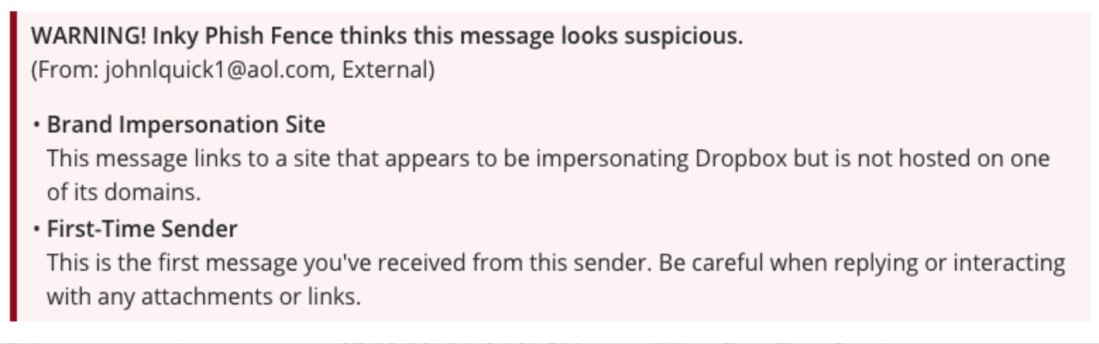
First Time Sender Warning
Besides warning of the mismatch of the Dropbox logo and non-Dropbox domain, Inky knew, thorough the social graph it has built for this user that this is the first time the user had received an email from this sender. (See the “First-Time Sender” note above.) This is an immediate red flag and way to catch impersonation attempts. If someone uses Dropbox often, how could this email possibly be from a first-time sender?
What Did the Attacker Want?
The attacker here was most likely after the login credentials of the recipient. The attacker wanted the recipient to sign in using their Gmail, Office 365, Exchange, Aol or Yahoo details. If the recipient had in fact logged into this false site, the attacker would then have their login and password, and therefore access to their personal or work email. It could have been days or weeks before the recipient even knew they had been compromised.
Not today though– Inky quickly caught this and kept the recipient safe. Phishing attack averted!
Want to learn more about how Inky’s Phish Fence can protect your business? Click here to sign up for a demo today.



