Although Bitcoin is entirely fabricated out of whole cloth, has no intrinsic value, and was created primarily to pay for the heavy-duty computing resources needed to process blockchains, it has become a store of value and medium of exchange because people agree on its status and function. All that’s required for the value to exist is that two or more people agree that it does.
Part of Bitcoin’s rise to prominence in the United States has been due to the Coinbase exchange, which has created the infrastructure to provide liquidity in Bitcoin markets, including trading activity and exchange into various currencies. Coinbase is the largest cryptocurrency exchange platform in the United States. As marks of mainstream acceptance, Coinbase went public with a direct Nasdaq listing in April this year, has established an annual revenue run-rate of nearly $2 billion, and is generating envy-inducing profit growth. At the end of 1Q21, Coinbase reported $335 billion in trading volume and boasted 56 million verified users. It also operates Bitcoin transaction capabilities with Stripe, Braintree, and PayPal and, through several large investment banks (JP Morgan Chase, Goldman Sachs, and Morgan Stanley), lets banking clients access Bitcoin funds.
That’s Where the Money is
Based on the Willie Sutton Rule (“I rob banks because that’s where the money is."), Coinbase has attracted a lot of criminal attention. The company fended off an extremely well-tailored phishing attack in 2019.
Recently, the prominence of Coinbase has attracted a new wave of phishing attacks aimed at Coinbase users. The attackers impersonated Coinbase and tried to get users to give up their Coinbase login credentials. This credential harvesting operation was conducted through phishing emails and sites that impersonated Coinbase.
In normal usage, Coinbase verifies customers when they upload identity documents (e.g., driver’s license, passport). They can then buy cryptocurrency by linking a bank account, debit or credit card, or a payment processor account. Coinbase also issues customers a digital cryptocurrency wallet, where they can store and send cryptocurrency to different external wallets.
Quick Takes: Attack Flow Overview
- Type: phishing
- Vector: hijacked legitimate email accounts, hijacked website
- Payload: credential harvesting
- Techniques: phishing email herds victim to a fake login page, where login data is captured
- Platform: Office365
- Target: Login credentials used to steal Bitcoin, financial information, and personal data.
The Attack
Coinbase is one of the hundreds of brands that INKY monitors for impersonation. This month, dozens of credential harvesting campaigns that target Coinbase users were discovered.
Here is an example, a relatively well-written pitch sporting the Coinbase logo:
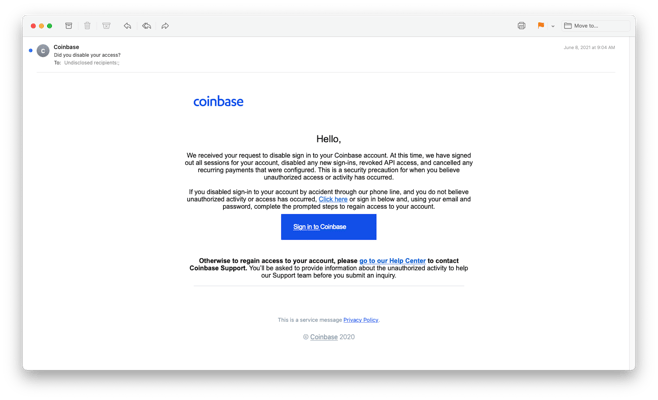
This phishing email originated from a hijacked email account and claimed to be from Coinbase. Victims were told that they needed to resolve an account issue by clicking on the blue “Sign in to Coinbase” button.
Anyone who clicked on the link was taken to a hijacked (from a German roof renovation company) website that hosted a perfect copy of a Coinbase login page:
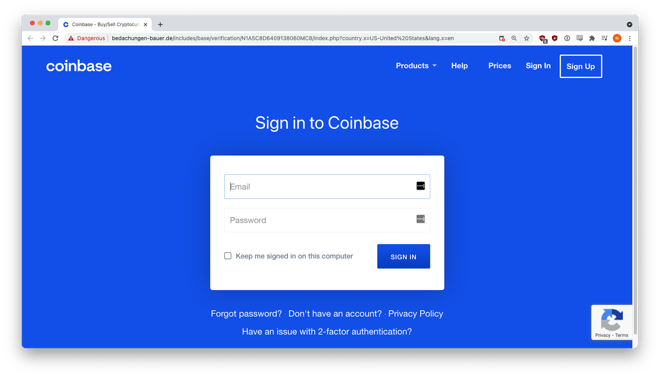
We tested the phishing site by entering fake credentials, which was promptly harvested and sent to the attackers.
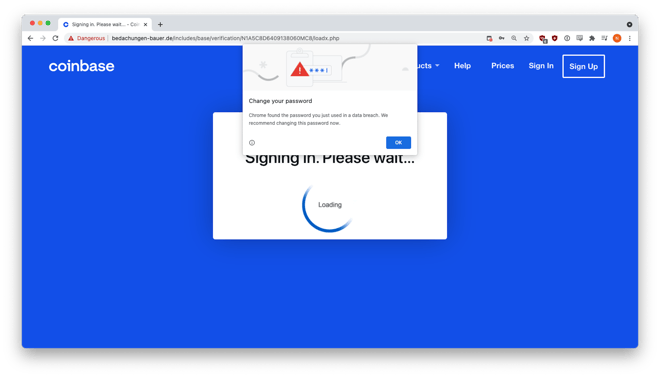
Two-Factor Authentication Isn’t Enough
Coinbase advises its users to set up two-factor authentication (2FA), but the black hats can beat 2FA with phishing kits that act as a relay between real websites and phishing victims.
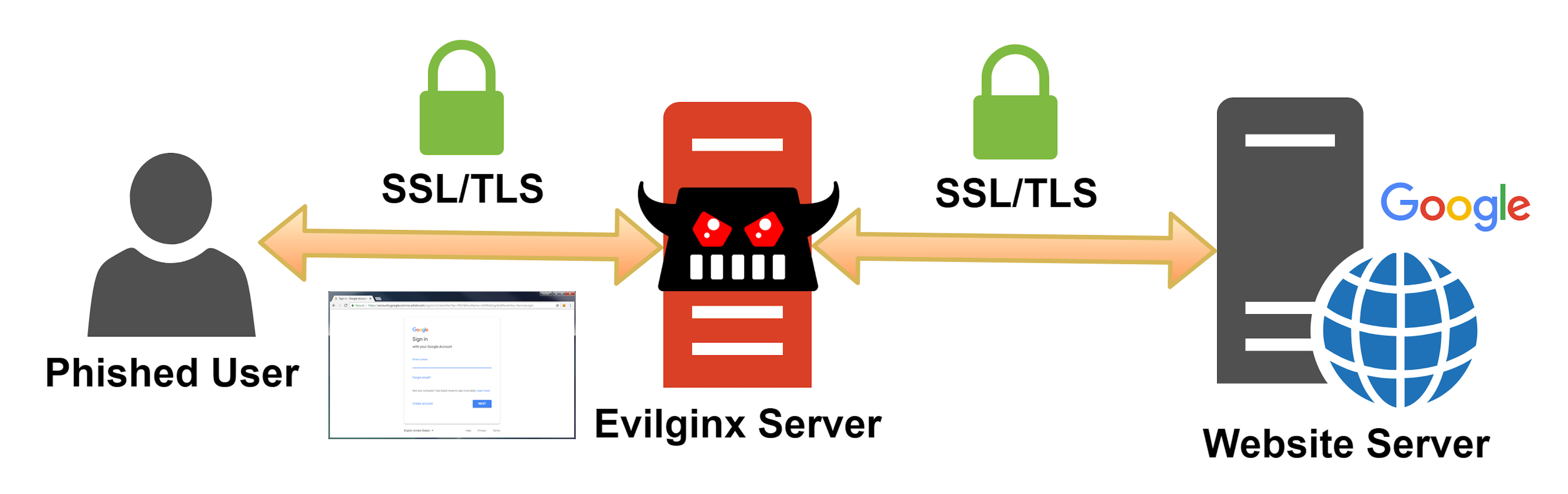
Evilginx is a man-in-the-middle attack framework that uses an Nginx HTTP server to proxy real websites to phishing victims. The phished user communicates directly with a website server and Evilginx intercepts all transmitted data between the two parties including the 2FA token that the website sends as a browser cookie to the client.
Although this technique was not used for this particular phishing attempt, Coinbase customers need to realize that 2FA will not protect them from phishing attacks.
Recap of Techniques:
- Hijacked Sending Address — sends out an email that looks as if it’s from Coinbase.
- Trusted Logo Imagery — gains the confidence of target recipient, furthering the likelihood of a successful exploit.
- Hijacked Website — passes checks for legitimacy by traditional email security products.
- Credential Harvesting — credentials obtained when the victim tries to log in to the fake page.
Best Practices: Guidance and Recommendations
A password manager is one way to stay protected against credential harvesting attacks, and supplements 2FA. It’s an encrypted database that stores, generates, and manages passwords for websites. They are available as browser extensions and have an automated script that compares the current site’s URL to the URL stored in the database. If the two URLs don’t match, then the manager will not automatically enter credentials. Password managers also have a confirmation icon flag that is visible on the browser toolbar when visiting known sites. This is an effective deterrent against look-alike domains and visual imitations. If your password manager doesn’t offer to automatically enter credentials, then you’re on a different website.
A proven way to fend off phishing attacks like this is to install robust anti-phishing technology. Solutions such as a simple cloud appliance that sits in line between the SEG and recipients’ inboxes can help with this problem. These solutions can catch the phish not by trying to determine whether the sender is legitimate but by comparing what the sender is purporting to be with what it really is. That two-pronged analysis is done by rendering the email in a headless browser for visual analysis and tracing the path back to its origin. If the mail "looks” like it comes from Coinbase, but actually comes from a domain not under Coinbase's control, these solutions alert the user and the administrative console.
Fresh Phish examples discovered and analyzed initially by Bukar Alibe, Data Analyst, INKY
About INKY
Headquartered in College Park, Maryland, INKY leads the industry in mail protection powered by unique computer vision, artificial intelligence, and machine learning. The company’s flagship product, INKY Phish Fence, uses these novel techniques to “see” each email much like a human does, to block phishing attacks that get through every other system. INKY founder Dave Baggett also co-founded ITA Software, the industry-leading airfare search company purchased by Google in 2011 for $730M, which now powers Google Flights®. For more information, please visit https://INKY.com/.


