If you've been following the Silicon Valley Bank (SVB) fiasco, you know the institution's demise was caused by a run on the bank. Can you visualize that? Hundreds of customers allowing sheer panic to set in, quickly prompting them to make swift and drastic decisions they might not have made under normal circumstances. It's the same type of emotional state that cybercriminals hope to provoke when unleashing a phishing attack. So, it's not surprising that bad actors quickly took advantage of the collapse of Silicon Valley Bank (SVB) and used it as a lure to steal credentials.
On March 16th, INKY noticed the first phishing scheme devised to steal Microsoft account credentials.
The Phishing Attack Specifics
THE RUSE: Fake DocuSign notifications that appeared to come from Silicon Valley Bank were sent to an unknown number of potential victims. Each of these phishing emails were spoofed to look like they came from the real and legitimate sending email address for DocuSign notifications (dse_na2@docusign[.]net).
THE REALITY: An examination of email headers revealed that these attacks actually came from several virtual private servers associated with newly created domains. As you might imagine, newly (and quickly) created domains are the norm in phishing attacks as phishers rush to devise a believable path for victims to follow.
The following is a list of domains and IP addresses initiating these attacks, attempting to pass as a DocuSign from Silicon Valley Bank:
valucards[.]com (created 2/27/23)
87.120.37.209
93.123.12.139
87.121.52.227
212.73.134.251
87.120.8.233
grouporionllc[.]com (created 3/12/23)
51.81.119.210
51.81.119.209
51.81.119.211
taylorlandcompany[.]com (created 3/12/23)
15.204.9.145
Customized DocuSign Notification Branded as Silicon Valley Bank
As you can see below, the phishing email that was sent is an identical copy of a real DocuSign email notification and has been customized with SVB’s logo.

Reeling In Victims to Harvest Credentials
Email recipients are told that the “KYC Refresh Team” sent two documents (KYC Form.docx & Change of Contact.docx) that require a signature. “KYC” is a banking term that stands for “Know Your Customer” or “Know Your Client”. It’s a mandatory process banks use to verify an account holder’s identity. Of course, in this case, the phisher is using it to convey a sense of legitimacy to its intended victims.
Recipients are told to click on the “'Review Documents” button. Hovering over the button reveals the link:

While most people probably don't slow down long enough to examine the links under buttons, this one - serving-sys[.]com - is a tracking link domain associated with Amazon Advertising. As you'll see below, recipients who click the link are first redirected to na2signing.web[.]app and immediately redirected to docuonline[.]eu.
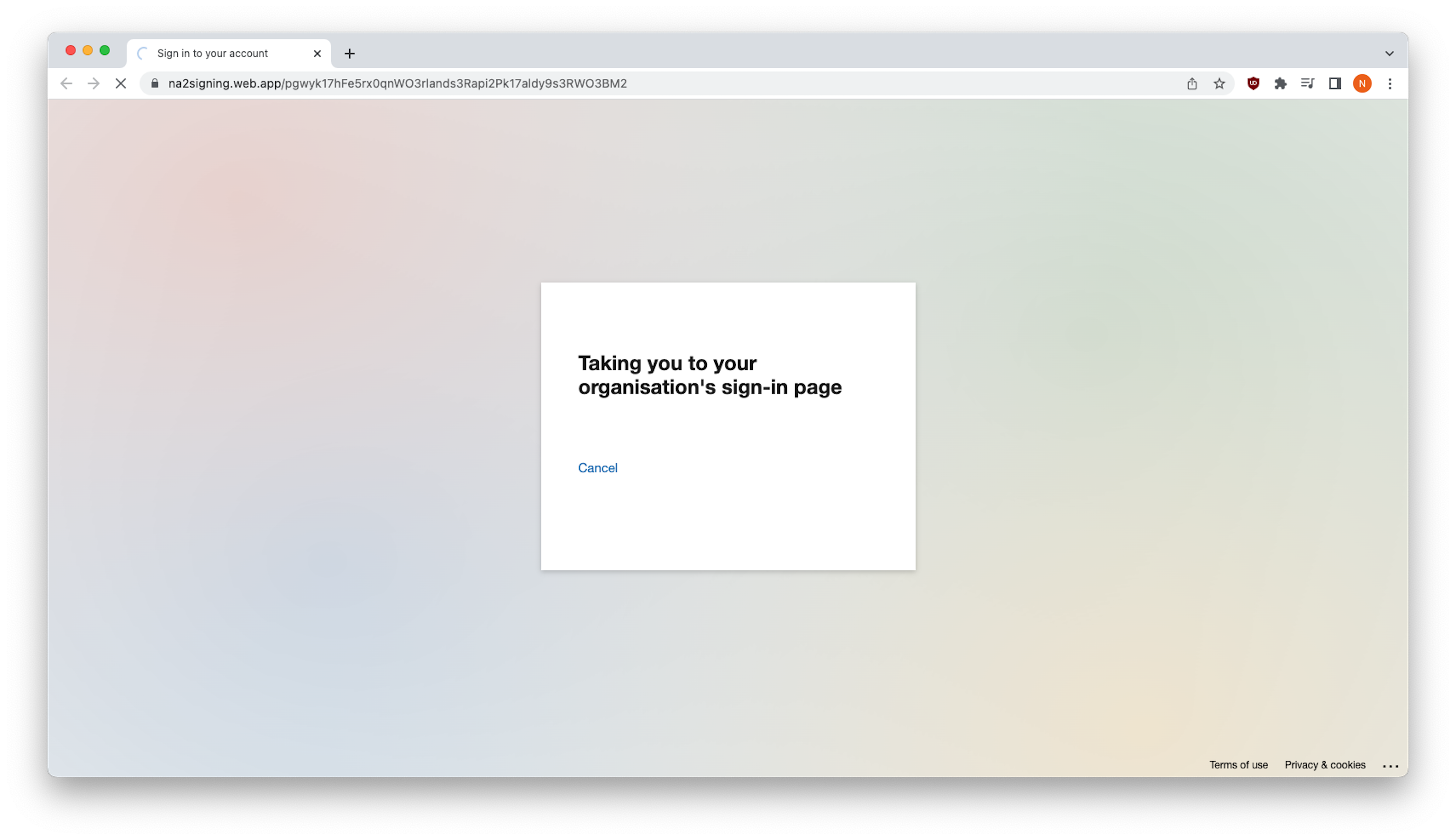
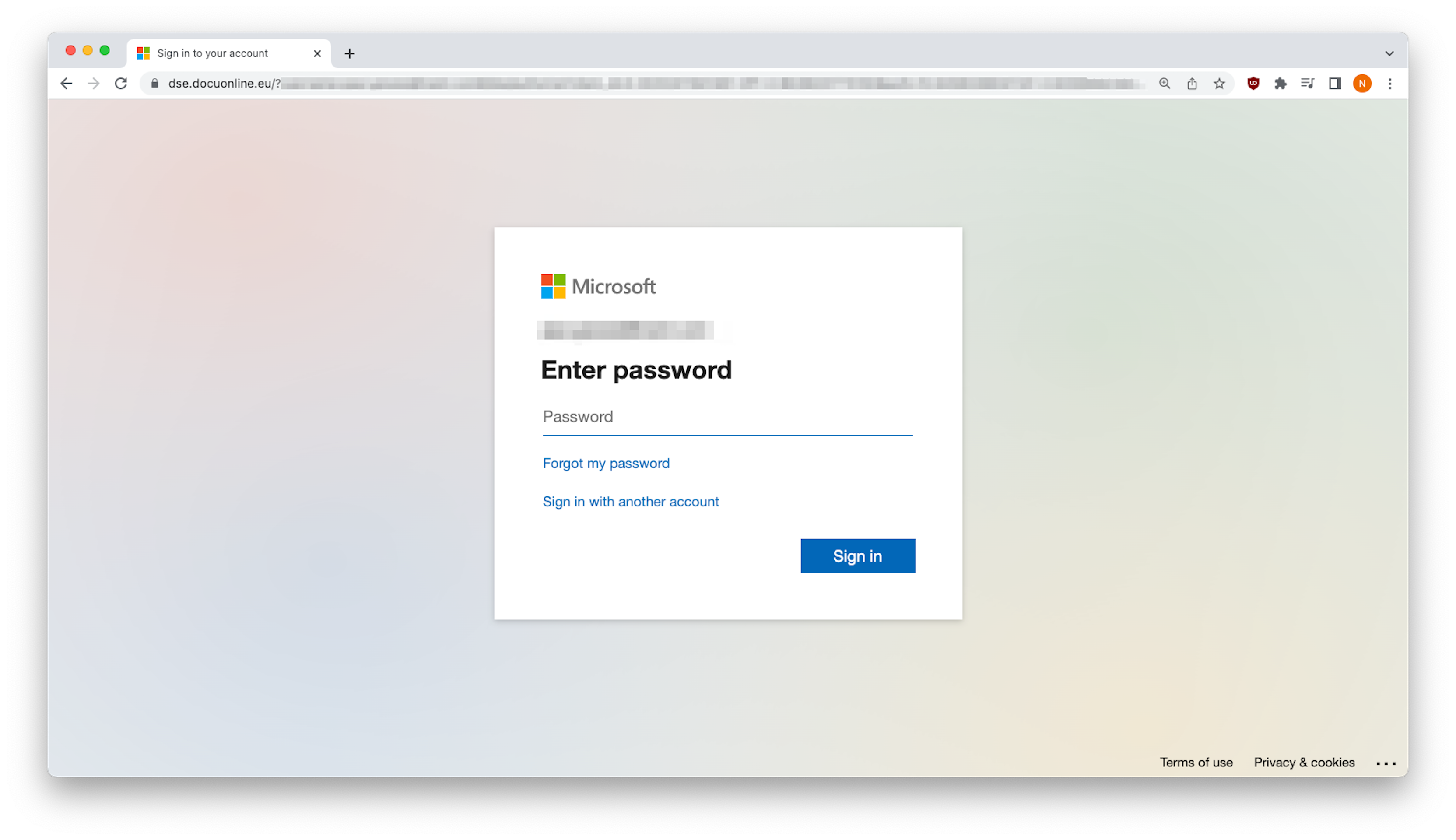
Exploiting Harvested Credentials
These phishing sites look identical to the real Microsoft login page. However, any data submitted will be sent to the bad actors behind this scheme. Once they have them, cybercriminals can use your harvested credentials in a number of ways including gaining access to anything from bank records to employer files, using your email to trick those close to you into surrendering important company data or banking access. Or, your credentials can be sold on the dark web.
Could it Happen To You?
Silicon Valley Bank was the 16th largest bank in the country and its customers withdrew $42 billion of deposits in less than 48 hours - ultimately leading to the company's collapse.1 That may sound like a record-breaking downfall, but companies that have been the victim of phishing attacks can fall just as quickly.
Adding fuel to the fire, the #1 cause for email phishing disasters is human error.2 If you're a business owner or a Managed Service Provider (MSP), that's reason to worry. Any employee, regardless of sonority or position, could make a costly mistake with just one click of a mouse or one login attempt. It's human nature. It's also why you need to partner with an expert in email security.
Recap of Phishing Techniques
-
Brand impersonation — uses brand logos and trademarks to impersonate well-known brands.
-
Credential harvesting — occurs when a victim enters credentials into a form controlled by phishers.
-
Exploitation of current events — capitalizes on the uncertainty, fear, and urgency related to SVB collapse.
Best Practices: Guidance and Recommendations
-
Hover over links to see where the link goes. In this case serving-sys[.]com is not a DocuSign or SVB domain.
-
Carefully inspect the link domain in the browser bar. In this case, a Microsoft login page is hosted on non-Microsoft domains (web[.]app & docuonline[.]eu).
-
Recipients should be suspicious that their Microsoft account credentials are demanded to sign a document on Docusign.
-
If an email seems suspicious, contact the sender through another method of communication to verify the legitimacy of the sender.
If you'd like to read more about credential harvesting, you might be interested in INKY's report entitled: Understanding Phishing: Credential Harvesting - Department of Justice Scam.
If you're concerned about how a phishing attack could affect your clients or your business, its time to take the next step in phishing prevention by calling INKY. Find out what INKY can do for you. Request a free demonstration.
_________________
INKY is an award-winning, behavioral email security platform that blocks phishing threats, prevents data leaks, and coaches users to make smart decisions. Like a cybersecurity coach, INKY signals suspicious behaviors with interactive email banners that guide users to take safe action on any device or email client. IT teams don’t face the burden of filtering every email themselves or maintaining multiple systems. Through powerful technology and intuitive user engagement, INKY keeps phishers out for good. Learn why so many companies trust the security of their email to INKY. Request an online demonstration today.
2Source: https://www.ic3.gov/Media/PDF/AnnualReport/2020_IC3Report.pdf


