One of the best things about working at INKY is observing all the shapes and sizes that phishing attack emails come in. It’s particularly rewarding knowing that even the most convincing Phishing email examples are caught by our Phish Fence.
Below you will find six of the most convincing phishing email examples we’ve seen recently. Would you fall for these phishing emails? Judge for yourself.
Phishing Email Example #1
Who is it supposed to be from?
Discover Card
What’s the Premise?
In this phishing example, the premise is that your account has been compromised. Lucky for you, Discover Card has caught it and is supplying you with a temporary ID and link so that you can update your username and password. The email uses Discover branding and iconography, and links to their actual app and all of their social media.
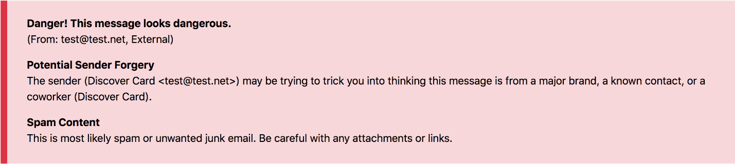
What did the INKY Banner say?
Phishing attack: Red Banner: Flagged for Sender Forgery and Spam content
What gave it away?
In this case, the email domain that the phishing attempt was generated from was not associated with Discover Card. Further, the content met Phish Fences spam criteria and was flagged as such.
What did it look like?

Phishing Email Example #2
Who is it supposed to be from?
A customer who’d really like to pay you!
What’s the Premise?
In this phishing attempt, the hacker is posing as a customer who would like to pay for a service rendered. To do so, they’ve kindly attached some information to help you make sure that you get paid.
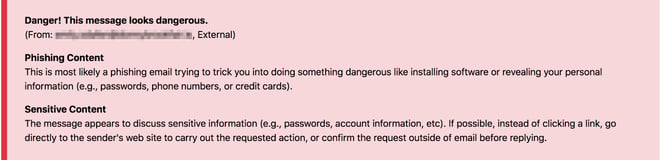
What did the INKY Banner say?
Phishing attack: Red Banner: Flagged as potentially dangerous, recognized as phishing scam, and flagged for sensitive content (financial information).
What gave it away?
The email met the profile for a phishing attempt, the content and cadence were suspect, and the attachment was found to be illegitimate and a simple attempt to solicit account details.
What did it look like?
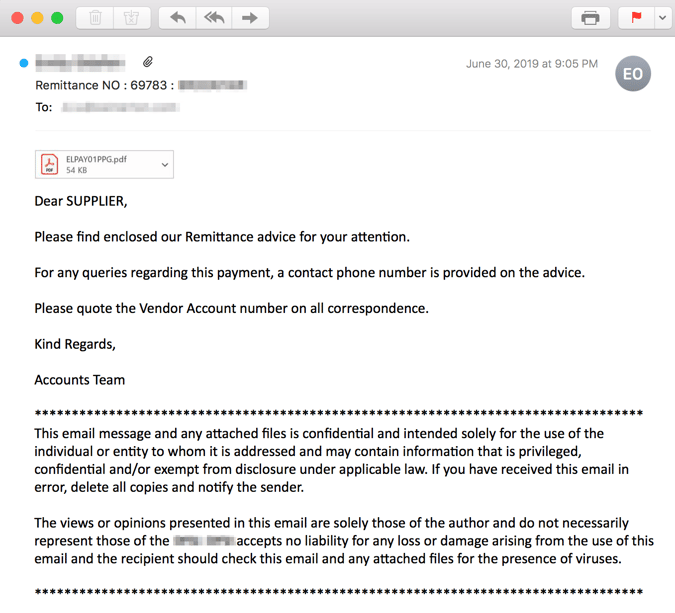
Phishing Email Example # 3
Who is it supposed to be from?
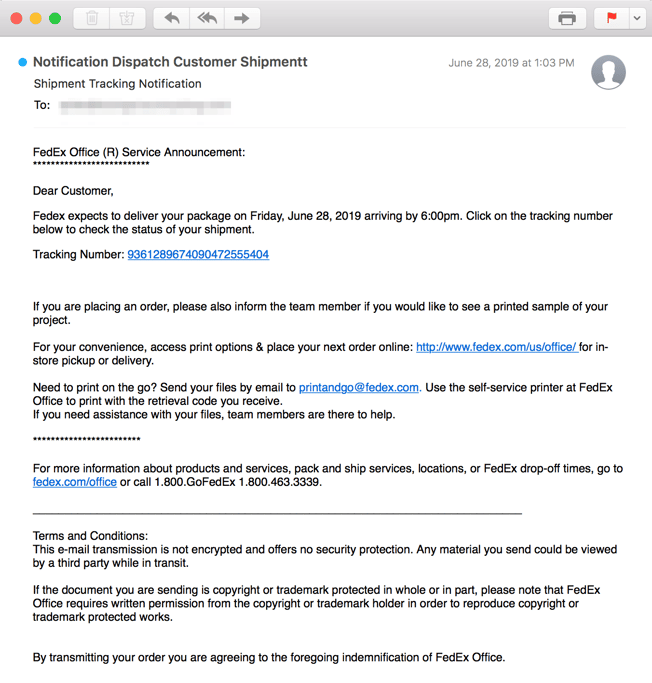
FedEx
What’s the Premise?
Your package is on its way! The tracking number supplied links off to a phishing site where credentials can be harvested.
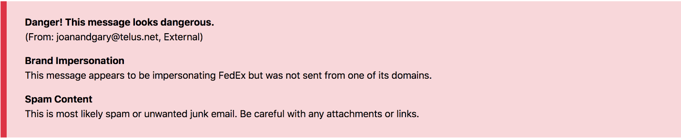
What did the INKY Banner say?
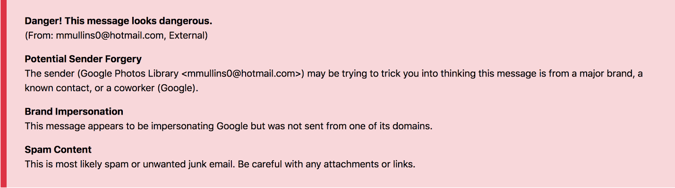
Phishing attack: Red Banner: Flagged as dangerous, not from a FedEx domain (Joan and Gary sent it), flagged as brand impersonation and the profile was recognized as likely spam content.
What gave it away?
Generally, FedEx is a shipping company; they don’t have to outsource shipping information to Joan and Gary. Once established that the sender was fraudulent, INKY recognized that the content was, in fact, a brand forgery.
What did it look like?
Phishing Email Example # 4
Who is it supposed to be from?
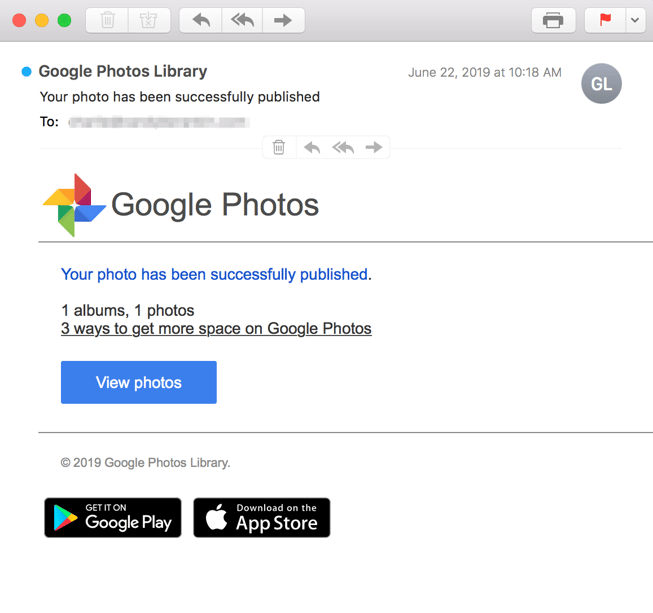
Google Photos
What’s the Premise?
Good news your photos have been published! Or, at least that is what the hacker wants you to believe. Given that you haven’t published any photos lately, you might hesitate but in our voyeuristic society who isn’t rushing to open that?
What did the INKY Banner say?
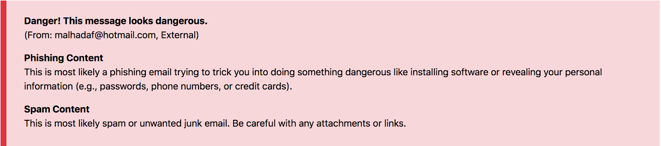
Phishing attack: Red Banner: Flagged as dangerous, not from a Google Photos, flagged as brand impersonation and the profile was recognized as likely spam content.
What gave it away?
In this case, Google has outsourced their photo album notifications to M Mullins, a dodgy chap who sticks it to Google by using a Hotmail account. Our Computer Vision engine analyzed the graphics and recognized them as fake.
What did it look like?
Phishing Email Example # 5
Who is it supposed to be from?
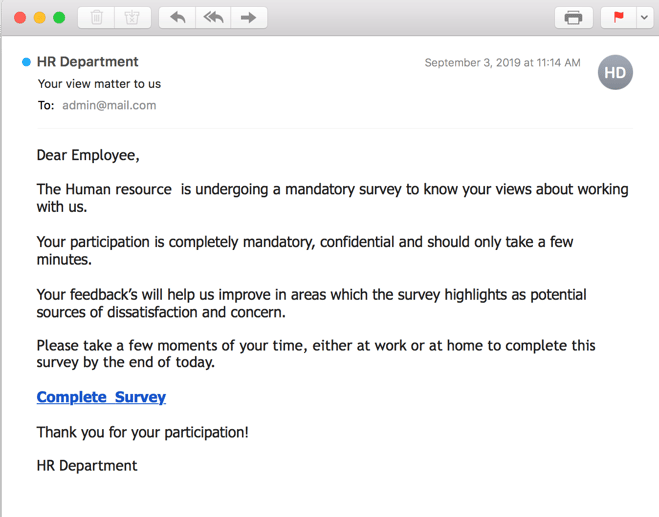
The HR Department
What’s the Premise?
Your Human Resources department cares about you very much, so much in fact that they’d like to get your views on how the company is doing. This is mandatory... don’t mess with HR.
What did the INKY Banner say?
Phishing attack: Red Banner: Flagged as dangerous, the content profile that is highly suggestive of a Phishing attempt
What gave it away?
Normally when your HR emails you, they do it from an internal account. It is pretty unlikely that old malhadaf is an actual representative of your company. Further, the email’s grammar and word usage is poor andthese types of solicitations set off INKY’s algorithms and are quickly recognized as phishing attempts.
What did it look like?
Phishing Email Example # 6
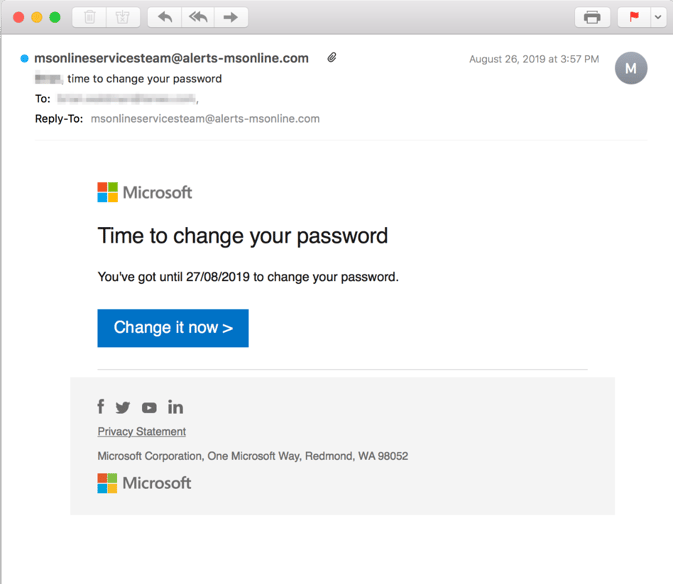
Who is it supposed to be from?
Microsoft
What’s the Premise?
Well shucks, buddy it’s time to change your password. Lucky for you, the fine folks at Microsoft are all over it!
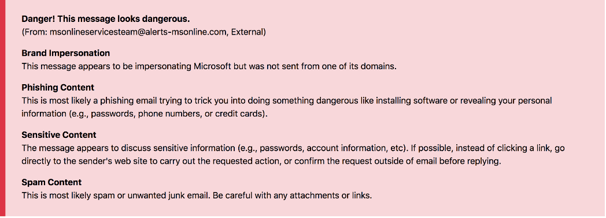
What did the INKY Banner say?
Phishing attack: Red Banner: Flagged as dangerous, brand impersonation, phishing content, spam content, and sensitive contact flags were all tripped.
What gave it away?
Despite the hacker’s best attempt at spoofing a Microsoft email, INKY was able to recognize that the incoming domain was not associated with Microsoft. Further, the computer vision engine picked up on the faked graphics and iconography. The content itself was particularly Phishy in that it was requesting a password reset.
What did it look like?
These were scarily convincing, right? The fact is, without INKY it is hard NOT TO fall for most if not all of these phishing attacks. It’s time to get ahead of the threats. Learn more about INKY’s email security solutions and how we can help you reduce risk and stay secure. If you're a Managed Service Provider (MSP) in search of a new email security solution for you and your clients, make time for a free INKY demonstration. After all, seeing is believing!
________________________________
INKY is an award-winning, behavioral email security platform powered by artificial intelligence/Gen AI, machine learning, and computer vision. INKY blocks phishing threats, prevents data leaks, and coaches users to make smart decisions. Like a cybersecurity coach, INKY signals suspicious behaviors with interactive email banners that guide users to take safe action on any device or email client. IT teams don’t face the burden of filtering every email themselves or maintaining multiple systems. Through powerful technology and intuitive user engagement, INKY keeps phishers out for good. Learn why so many companies trust the security of their email to INKY. Request an online demonstration today.



