The first known ransomware attack occurred in 1989 when AIDS researcher Joseph Popp, Ph.D., distributed 20,000 floppy disks to AIDS researchers throughout the world. The instructions that came with the disks explained that by completing the questionnaire that would appear on their screen, they would receive a confidential report detailing their risk of exposure to AIDS. They also promised a set of best practices for reducing their risk of contracting the deadly disease. Sadly, AIDS wasn’t the only infection spreading. Unbeknownst to the users, the disks were infected with malware. Dormant at first, the malware encrypted the user’s files and within days the computer would display a ransom message demanding that a payment of $189 be sent to a P.O. Box in Panama in exchange for the safe recovery of their system.
Sometime later, Popp was arrested for spreading what would become known as the AIDS Trojan or PC Cyborg ransomware attack. While in the end, Popp was declared mentally unfit to stand trial, he had launched what would become one of the most lucrative types of cybercrime in the world.1
A lot has changed in the world of cybercrime since 1989.
With inflation, Joseph Popp’s 1989 ransom demand is the equivalent of $410.13 today. That’s certainly another piece of the ransomware industry that has changed over time. Colonial Pipeline paid almost $5 million to hackers in order to end their ransomware attack in 2021.2 Meat distributor JBS shelled out $11 million just weeks later.3
Technology has also improved dramatically since the first ransomware attack. Clearly, the cybercriminals who have superseded Joseph Popp have a lot more tools at their disposal and, over the years, they have gone to great lengths honing their ransomware development skills. Floppy disks have been replaced with sophisticated spear-phishing campaigns which target unsuspecting recipients across all industries. And, cybercriminals have even started their own enterprises. Many work in groups in order to have expertise in multiple areas. Others develop ransomware programs that are sold to cybercriminals with lesser abilities, allowing almost anyone to enter the dark world of cybercrime.
How do we stay ahead of the many Joseph Popps of today’s world? There are two keys to fighting ransomware every business should follow.
First, you need to be protected. Because most ransomware attacks begin with a phishing email, the best way to do this is with the help of a third party who is a proven expert in email phishing solutions.4
Threat actors are continually improving their game, developing new and sophisticated programs that go undetected and ultimately rob companies and individuals of their hard-earned money, wreaking havoc on the lives of others. To many, this battle in the war against phishing appears to be an uphill climb. But at INKY, we feel differently about the fight. We are relentless and determined in all that we do.
Powered by computer vision, artificial intelligence, and machine learning, INKY is relentlessly effective and catches pretty much everything from daily spam to the most sophisticated phishing scams and ransomware attacks. How? INKY gets to know the people with whom you exchange emails and, with the help of social graphing and stylometry, learns to spot imposters. INKY uses intelligent machine learning algorithms to catch abnormalities in emails, even if the threat has never been seen before. The more that INKY sees, the more the system learns; and the more the system learns, the more INKY sees. This allows INKY to adapt in real-time to the evolving threat landscape and keep you protected 24/7/365.
Secondly, you and your employees need to stay educated. Every year the threats get worse. Reviewing simple industry facts keeps cybercrime and ransomware right where it should be - front of mind. Here is a quick overview of the current state of ransomware.
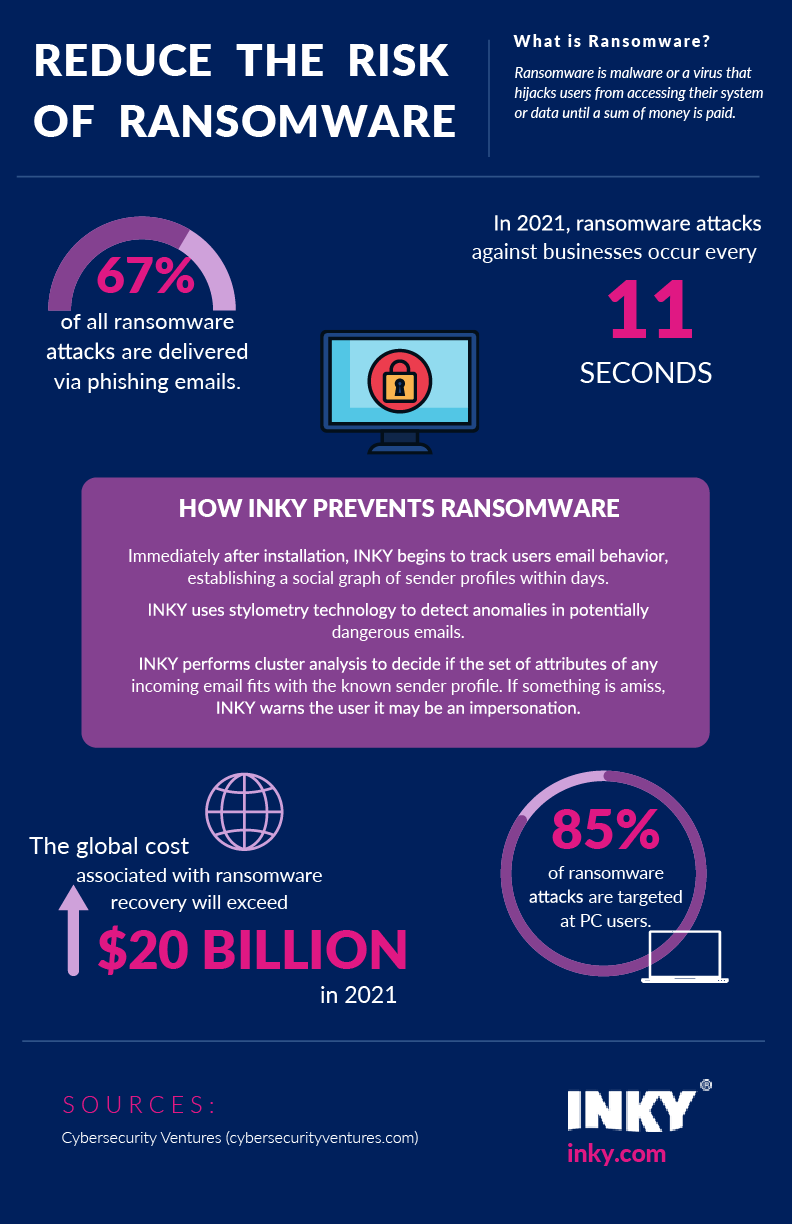
As for employees – the very ones most likely to set a ransomware attack into motion with a simple click of a link or attachment – they need to be trained continuously. Phishing simulation exercises are not enough. The best way to keep employees in tune with potential threats is by using a system that shows them the safety level of each email they receive.
We call the ingenuity behind INKY lies in its banner system. The INKY banners can prevent disastrous phishing threats while regularly educating and informing your staff. Curious about how it works? The power behind the INKY Banner is known as the INKY Phishfence – stopping phish in a matter of seconds. To do so, INKY performs a high-level analysis using computer vision, artificial intelligence, and machine learning. Once the phishing analysis is complete, INKY applies a banner to every email. The banners educate the user of the email’s phishing threat level with a short explanation of what it has encountered. Gray is safe. Yellow advises caution. Red signals danger. Whether it’s on a desktop, laptop, or mobile device, each INKY protected email is evaluated. The banners also employees the option of using a “Report This Email” link in order to communicate or confirm the status of phishing emails. That information goes straight to INKY’s head, making her even smarter.
Isn’t it time to do more to prevent phishing and ransomware attacks in your organization? See how INKY can help you stay protected from the myriad of devastating cybercrimes occurring every minute. Sign-up for your free demo today.
----------------------
INKY® is the most effective hero in the war against phishing. An award-winning cloud-based email security solution, INKY® prevents the most complex phishing threats from disrupting or even immobilizing your company’s day-to-day business operations. Using computer vision, artificial intelligence, and machine learning, INKY® is the smartest investment you can make in the security of your organization. INKY® is a proud winner of the NYCx Cybersecurity Moonshot Challenge and a finalist in the 2020 RSAC Innovation Sandbox Competition. Learn more about INKY® or request an online demonstration today.
2Source: https://www.nytimes.com/2021/05/13/us/politics/biden-colonial-pipeline-ransomware.html
3Source: https://www.cbsnews.com/news/jbs-ransom-11-million/
4Source: https://www.ic3.gov/Media/PDF/AnnualReport/2020_IC3Report.pdf



