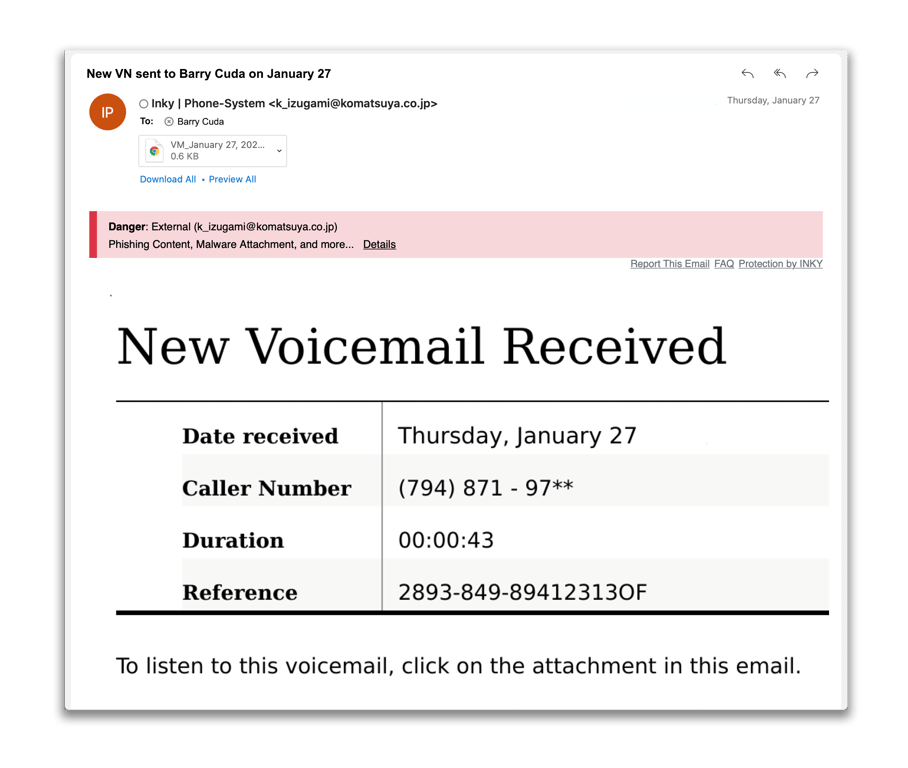
One of the golden rules in the war against phishing is this: Don’t open attachments if you don’t know who they’re from. The reason is simple – malware. Malicious software, known as malware, is a harmful program or code that is designed to invade, disable, and damage your computers, networks, or systems.
Malware comes in many forms, including ransomware, spyware, worms, viruses, trojans, rootkits, cryptojacking, and keyloggers.1 It’s a favorite among cybercriminals who use it to steal, delete, or encrypt data; hijack your computer’s functions, or plant something insidious.
The most common delivery method for malware is…you guessed it…phishing emails. And it’s no small problem. There are more than 1 billion malware programs out there and while hundreds of thousands of files become infected by malware every day, most are existing infections that are running rampant.2 The results are staggering. In 2021, U.S. cybercrime attacks that contained malware totaled $5,596,889 in losses.3
Has your computer been infected by malware?
Not all malware is easily detected. It can quietly hide in your computer, doing all sorts of damage without giving you the slightest indication that you’re infected. However, there are some obvious signs too. Malware will slow down or crash your computer, set off a series of annoying pop-up ads, steal your disk space, and even disable your antivirus software.
There is a solution – INKY Advanced Attachment Analysis
Until recently, the best solution for minimizing the risk of a malware-infested attachment being opened was to detect signs of foul play within the phishing email itself. Of course, that tactic alone won’t solve the problem, especially if your company relies on a mediocre email security solution. Millions of malicious attachments get past Secure Email Gateways (SEGs) – often in the form spear phishing or Business Email Compromise (BEC) – because the email itself appears to be safe.
That’s where INKY comes in. INKY sits downstream from the SEGs and with the help of its unique Advanced Attachment Analysis, malicious links hidden in attachments are identified and stopped.
INKY Offers Two Choices for Attachment Analysis
Attachment Analysis isn’t new to INKY. Its Standard Attachment Analysis is part of the INKY process and includes file-level checks for known virus signatures, URL analysis, and a deep analysis of the rendered content of linked websites. This provides a solid first-line defense mechanism for email attachments.
INKY Advanced Attachment Analysis takes the process to a whole new level by breaking attachments down into separate parts or objects and analyzing them separately. Each object is then broken down further into sub-objects. Every sub-object leverages a file inspection platform to check for RFC or document-type standards violations. Objects are evaluated for consistencies with Criminal Enterprise Malware Platforms, ransomware families, malware families, malicious documents, executable and macro functions, and multistage exploit tactics. This approach uses the tactics, techniques, and procedures (TTP), rather than file hashes or known pattern matching, to identify the trickiest exploits that threat actors dish out – including zero-day attacks.
 Other email security companies in the market rely on sandboxing attachments to attempt to guard against these threats, but this approach burdens IT and creates a poor experience for end-users. INKY Advanced Attachment Analysis transforms the way organizations protect against these threats. With a confidence rate of 99.97% and a deep attachment analysis speed of less than a second, INKY is the frontrunner. INKY also ensures the analysis data is kept private and because it is designed to handle high volumes, the cost of INKY Advanced Attachment Analysis is well below the competition.
Other email security companies in the market rely on sandboxing attachments to attempt to guard against these threats, but this approach burdens IT and creates a poor experience for end-users. INKY Advanced Attachment Analysis transforms the way organizations protect against these threats. With a confidence rate of 99.97% and a deep attachment analysis speed of less than a second, INKY is the frontrunner. INKY also ensures the analysis data is kept private and because it is designed to handle high volumes, the cost of INKY Advanced Attachment Analysis is well below the competition.
The Whole Nine Yards
There’s no doubt that INKY Advanced Attachment Analysis is as impressive as it is powerful. However, it’s just the tip of the iceberg. INKY is the industry’s best solution for the security of your email. Award-winning and cost-effective, INKY uses computer vision, artificial intelligence (AI), and machine learning, to search for signs of fraud on every inbound, internal, and outbound email. It works on any device - including mobile - and places one of nearly 60 warning messages directly in the email.
To truly have a handle on phishing threats — including malicious attachments — you need a third party’s assistance. So, take the next step and see what INKY can do for your company by requesting an online INKY demonstration today. We feel confident that before long, the only problem you’ll have with attachments, is your newfound attachment to INKY.
----------------------
INKY is an award-winning, cloud-based email security solution developed to proactively eliminate phishing emails and malware while simultaneously providing real-time assistance to employees handling suspicious emails so they can make safer decisions. INKY’s patented technology incorporates sophisticated computer vision, machine learning models, social profiling, and stylometry algorithms to effectively sanitize emails, rewrite malicious links, detect and block security threats, mitigate sender impersonation, and more. Cost-effective and powerful, the INKY platform was developed for mobile-first IT organizations and works seamlessly on any device, operating system, and mail client. Learn more about INKY™ or request an online demonstration today.
1Source: https://www.malwarebytes.com/malware
2Source: https://dataprot.net/statistics/malware-statistics/
3Source: https://www.ic3.gov/Media/PDF/AnnualReport/2021_IC3Report.pdf



