Email is nearly ubiquitous in the workplace. It is one of the most durable and effective forms of communication. It is also exceptionally vulnerable to attacks. While it may be easy to spot the fake emails from the British lawyer or Nigerian prince wanting to give you millions, today’s hackers are sophisticated and targeted.
When you take into account that 76% of organizations report they experienced phishing attacks, it’s no laughing matter.
Spear Phishing Attacks
Unlike the bulk email attacks that spread a wide net and hope to catch someone, spear phishing is used to target one, or a select few people, within an organization with a personalized attack. By doing a little research, often found publicly available online, criminals can find very specific information about the target. By scanning company websites, social media networking sites, public filings, and third-party databases, hackers find details to sprinkle into an email to convince unsuspecting users. With the info in hand, they can customize emails to appear more legitimate.
These emails may impersonate a company executive, specific employees, or members of a group.
They usually include an urgent explanation as to why you need to provide information or act immediately.
The more specific they are, using familiar names, companies, and similar email addresses, the more successful they have been. Because of the personal level these emails display, it is difficult for people to identify spear phishing attacks on their own.
Examples of Spear Phishing Attacks
You might receive an email from your company CEO inviting you to attend a meeting with a link to click to accept. An email might hit your inbox that appears to be from an airline or HR department that asks you to confirm travel arrangements.
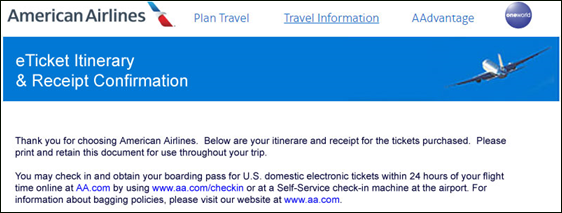
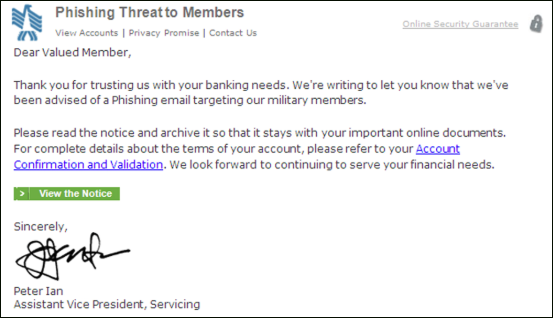
Members of the military might even get a warning about a phishing attack asking them to confirm account information.
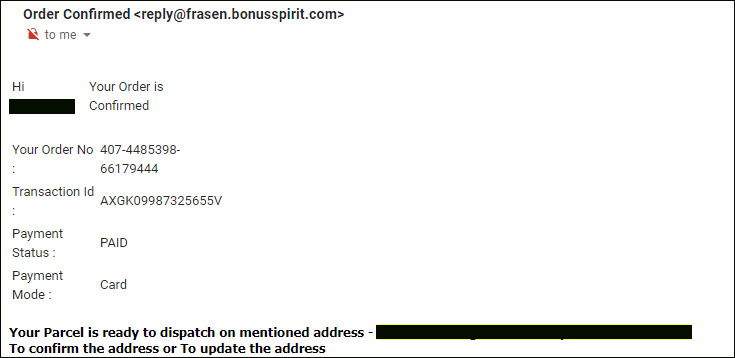
An email may let you know the item you order is on the way, but they need you to confirm the mailing address.
Clicking any of these might allow hackers to gain access to sensitive information, launch malware attacks, or attempt to induce you to wire money.
Two specific email phishing attacks have a nearly 100% click-through rate. One is an email from a spoofed address mimicking a company executive with an “updated building evacuation plan” and another scam purports to be from IT or HR asking employees to do an immediate “password reset.” Other highly successful email spear phishing attacks targeted company individuals with a link to an alleged voicemail from a company executive or system security update.
It’s a big-time enterprise. The FBI’s Internet Crime Report estimates the cost of business email compromise (BEC) scams cost U.S. organizations more than $675 million each year.
Combating Spear Phishing
Typical awareness training is ineffective because it only trains on known threats and not the ones lurking in the background. As a trained IT or CISO, spear phishing emails may be easy for you to spot. However, most employees – even those that have been trained – can easily get fooled.
People go quickly through emails, so the real environment is difficult to emulate in training sessions. Smart people fall victim to spear phishing because they are simply moving quickly to handle the high volume of email they receive. According to Intel, 97% of people are unable to detect a sophisticated phishing email.
Email was never designed to be secure. When it was created back in the 1970s security wasn’t a consideration because it didn’t need to be at the time. But at INKY we have a passion for email. We understand all its flaws and the imperative place it plays into today’s business world..We are here to protect is and that’s why Inky is one of the most significant investments you can make in the security and reputation of your organization.
The Best Spear Phishing Emails Solutions
The best solution to protect your employees from phishing emails is the Anti-Phishing Solution by Inky. It continuously scans email also providing state-of-the-art spam and malware protection. Both incoming and outgoing emails are checked for fraud automatically.
Sophisticated machine learning and computer vision is coupled with artificial intelligence and constantly updated algorithms to prevent even the most sophisticated phishing attacks that get through every other system. Inky® Phish Fence checks for spoofed email addresses, forgeries, and malicious links. It will either place the offending email in quarantine or deliver it with links disabled and a prominent warning message for the user.
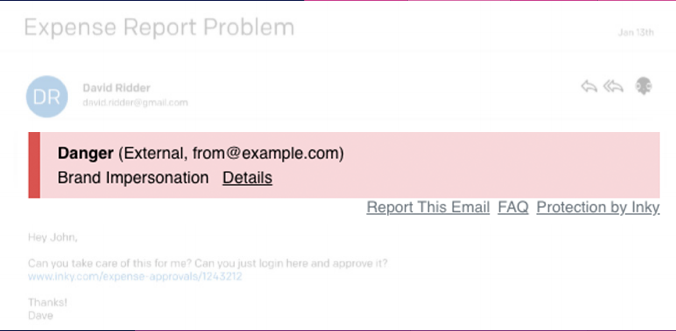
The banner literally jumps out at users and makes it nearly impossible to ignore. Unlike other anti-phishing solutions, it also works in mobile.
The Inky analytics dashboard is designed for deep analysis by system administrators. Providing both an overview and the ability to drill down to individual threats, attacks, or emails, a searchable interface makes it easy to isolate what you want.
Inky® Phish Fence can be set up in less than an hour and works with Microsoft 365, Exchange, Google Suite, and nearly every email system available.
Schedule a live, personalized demo and see how Inky® Phish Fence can provide you with maximum spear phishing protection for your organization.



