It sits there in your inbox daring you to click on it. It appears to be an important message from the folks at Microsoft’s Office 365 email security team. Either your mailbox storage is full, there is an important security notice you need to read, or your mailbox is about to be deleted and you need to act to prevent it from happening. It looks legitimate, but it is just a phishing attempt to try to get your login credentials or launch some malware.
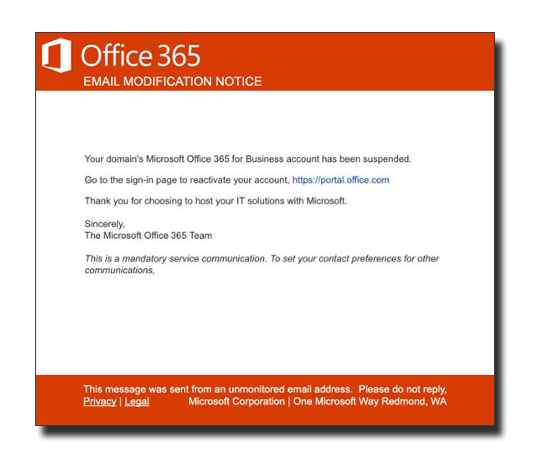
With all the Office 365 email security features built-in to the software, how does something like this get through the filters and make it into your inbox?
As technology and security evolve, so do the scammers. The bad guys have become incredibly creative in finding new ways to get past the Office 365 secure email filters. These aren’t just lone hackers sitting in the dark in their basement. Phishing scams have become big business for organized crime. The FBI says criminals using business email compromise campaigns stole $676 million last year. Even Facebook and Google fell victim and may have lost as much as $100 million.
Phishing Attacks
Phishing attacks are bulk emails sent to as many people as possible. The email looks like it comes from a trusted source and encourages you to click on a link. The link might launch malicious code or redirect you to a spoofed website to grab your login credentials.
Spear Phishing Attacks
Spear phishing attacks are targeted attempts. Scammers will scour online sources such as social media, public filings, and company documents to find out personal information about you and your colleagues. The attackers might impersonate a business colleague and try to get confidential information from you or send an email using your name and a familiar tone to try to get you to act.
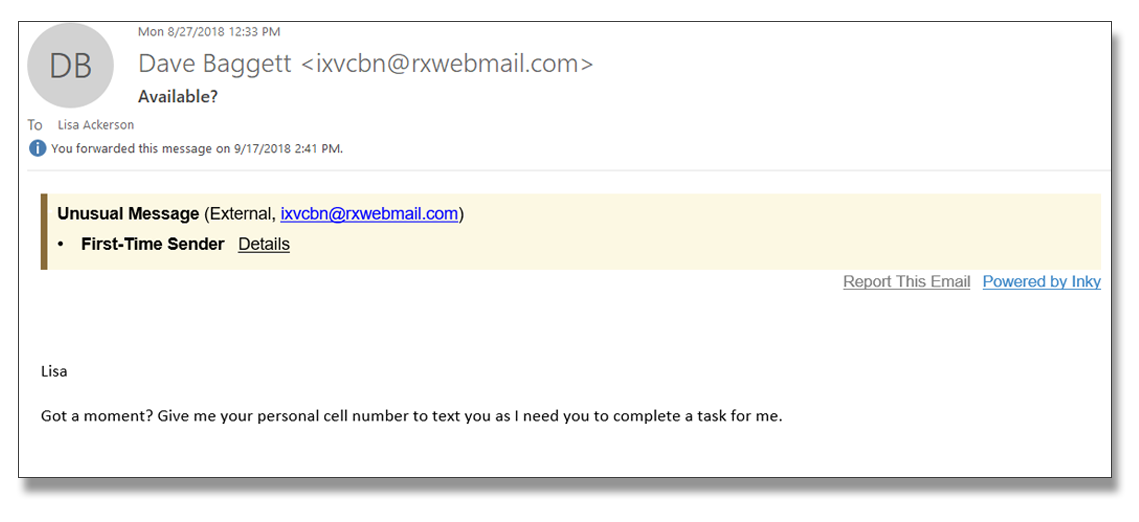
Whaling Attacks
Whaling attacks are using the same methods as spear phishing to do social engineering, but they are aimed at high-value targets. An email appearing to be from a CEO ask a CFO to complete a wire transfer on their behalf. Because these email phishing attempts are high stakes, the email will often include personal info or seemingly confidential information only the Executive would know.
Zero-Day Attacks
So-called Zero-Day Attacks prey on software vulnerabilities. Often, these are bugs or flaws in the coding that are known to the software vendor but a patch to fix it hasn’t been released yet. Such a flaw in Microsoft Excel allowed hackers to launch a zero-day attack by hiding malicious code in an Excel spreadsheet attachment.
You Need Better Security
All of these types of attacks have managed to get through various filters and Office 365 email security. Using Microsoft’s built-in defenses alone will not solve the problem.
INKY Phish Fence is the solution favored by the most successful CISOs because of its unique ability to stop phishing attacks that make it through Office 365 secure email filters. INKY goes above and beyond Microsoft’s Exchange Online Protection (EOP) and Exchange Advanced Threat Protection (ATP) in Office 365 secure email.
The Problem with Threat Feeds
EOP/ATP rely on threat feeds to identify phishing emails. That means URLs in emails are compared to known threats, from real time streams like Netcraft, OpenPhish and Phish Tank. Unfortunately, many phishing emails get through EOP/ATF in Office 365 because the attack uses a randomized URL, URLs not yet identified, or the email doesn’t have a URL in it at all.
Both Microsoft and INKY rewrite dangerous links in your email. If you do click on a link, you go first to a proxy page for examination. While Microsoft’s EOP/ATP security will look up the URL in known threat feeds, INKY will actually render the page and examine the HTML content for warning signs of phishing, malware, or credential harvesting. That means even if the page or URL has never been reported to a threat feed, INKY can determine the page is malicious and flag it.
Office 365 will flag brand forgery attempts if email addresses are similar, but not exact. This doesn’t catch everything because it is so easy to create plausible emails that can impersonate real company emails. INKY uses Computer Vision to scan the email as a human would. It can detect even the smallest difference in brand logos and text.
Warning Banners and Behavior Profiling
INKY also provides bold warning banners in the email itself to alert users. Office 365 email security does not. These banners provide protection while also educating users what to look for in phishing emails. These banners also work on mobile devices which is a unique technology that no other anti-phishing solution offers.
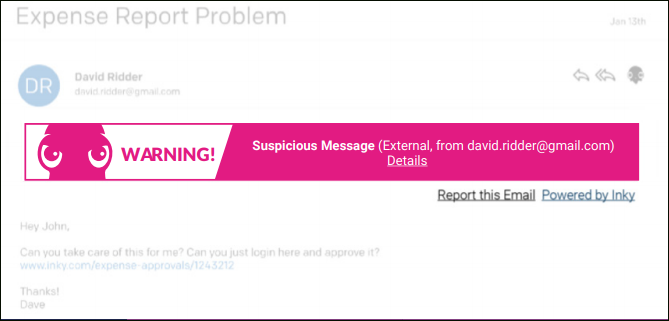
INKY uses Behavior Profiling through AI to build data-rich social graphs of senders. If an email contains information that varies from the profile, it will warn the recipient. Microsoft only uses simple address matching, mainly for executives, which only catches the most obvious spear phishing attempts. INKY’s technique is particularly effective against Spear Phishing attacks.
Protection from Zero-Day Attacks
Using a combination of Computer Vision, AI, and Machine Learning, INKY Phish Fence even identifies zero-day attacks. Other anti-phishing solutions rely on records of previously identified attacks. That simply can’t stop the increasing number of zero-day (new or unreported) threats like INKY can.
The Anti-Phishing Solution Favored by Successful CISOs
To learn more about how INKY’s cloud-based email security platform can better protect you and your team, contact us today at Sales@INKY.com.



