What is Phishing?
Phishing is an all too common cyber attack using deceptive emails, malware, and websites to gather personal information. Hackers use this tactic to gain access to business systems, con someone into clicking on a link that downloads malware, or trick someone into acting.
More than $12.5 billion worth of losses has been reported over the past five years, according to the FBI’s Internet Crime Complaint Center known as IC3. In the last two years, there has been a 136% increase in victims and losses.
With so much money at stake, hackers have become more sophisticated than ever, building fake websites that mirror legitimate companies and using social engineering to target CEO and other top executives with detailed and personal information.
Phishing Email Examples In 2018
Organized crime is now in the phishing pool. In 2018, we have seen an increase in the number of sophisticated attacks. Here are some recent examples of high-profile phishing scams and samples of actual phishing attacks that hit their target.
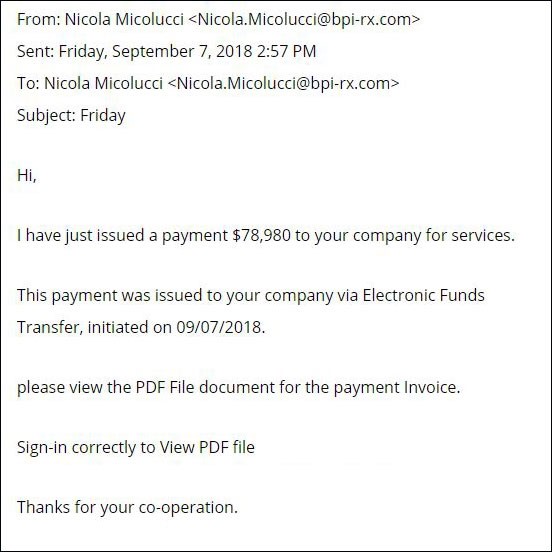
Employees at the University of Kansas responded to a phishing email requesting update payroll information. This provided login credentials to hackers who redirected direct deposit paychecks to their own accounts.
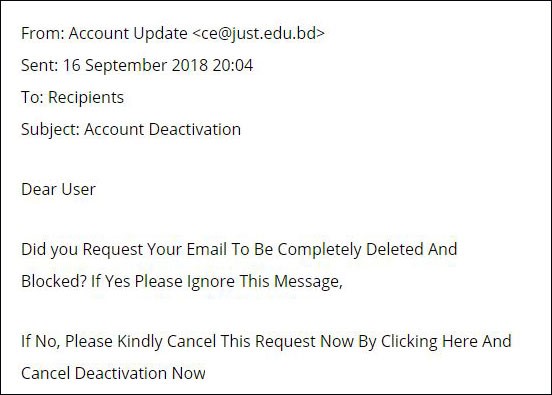
Ransomware is launched from malicious links in emails. These links may target individuals by letting them know their email box is full, their login credentials have been compromised, an order or invoice needs your review or any variety of scams that need your urgent attention. Clicking launches malware that locks up your computer until you pay the ransom. Two of the world’s largest shipping companies, A.P Moller-Maersk and Cosco, were both hit by phishing attacks that launched ransomware that cost the companies in excess of $200 million.
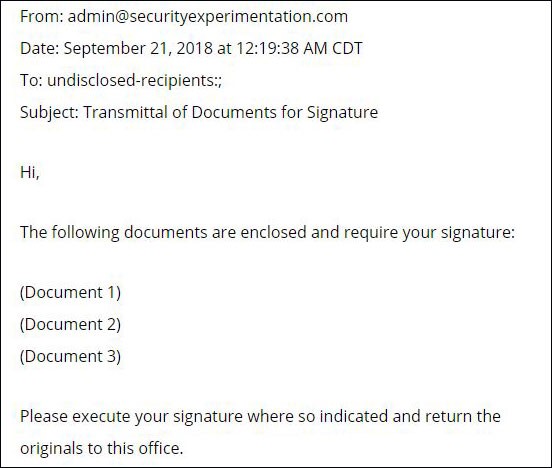
Hackers sometimes use one company’s compromised information to attack another one. That was the case when Fazio Mechanical Services, an HVAC contractor in Pittsburgh, fell victim to an email phishing attack that gave scammers access to their systems. The company was connected to Target’s electronic billing system, giving the bad guys a back door to steal credit card data for more than 100 million consumers. Patching the breach and repairing the damage cost Target an estimated $100 million dollars.
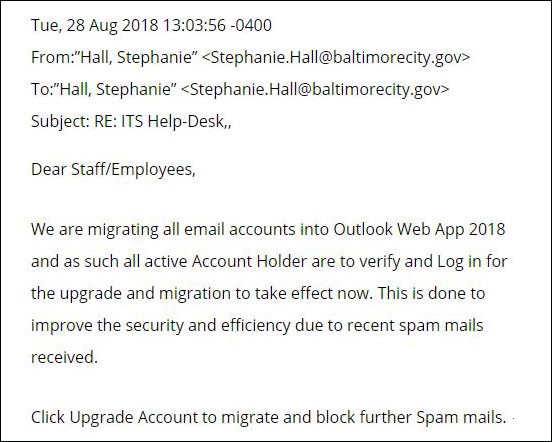
Plane manufacturer FACC was scammed for $56.7 million when its CEO, Waltar Stephan, acted on a fraudulent email impersonating someone in the company urging the need to take care of an immediate transaction.
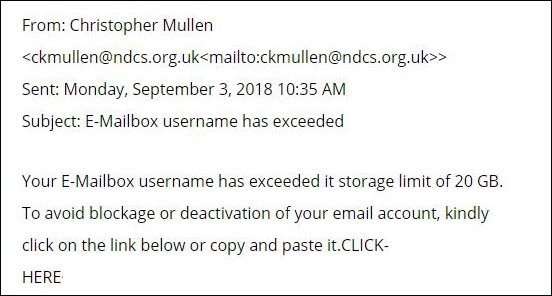
Attackers are also expanding beyond email. Facebook messages, SMS, iMessage, Android Hangouts, WhatsApp, Google Play, and Snapchat have been all been used for phishing.
Your Business's Reputation is on the Line
In addition to the costs of becoming a victim, there’s the cost to your reputation. Nothing hurts consumer confidence more than a breach that uncovers your customer’s data or compromises your employees. 90% of data breaches have been the result of phishing or social engineering schemes.
In addition, scammers are using access to your systems to trade on your brand name. In one case, a major financial services firm fell victim to a phishing email where the hackers gained access and created email accounts on company servers, which they then used to send phishing emails to other targets using the company’s name and email addresses.
The Best Phishing Solution
The best solution to fight phishing scams is the Anti-Phishing Solution by Inky. A comprehensive email phishing, SPAM and malware protection, Inky® Phish Fence continuously scans both incoming and outgoing emails for fraud.
Using sophisticated machine learning, artificial intelligence, and algorithms to block even sophisticated phishing attacks that get through every other system.
When it encounters a spoofed email address, a forgery, or malicious links, Inky® Phish Fence either quarantines the email or deliver it with disabled links and a warning for the user. Because the warning shows in the body of the email, rather than the header, it shows in mobile applications as well.
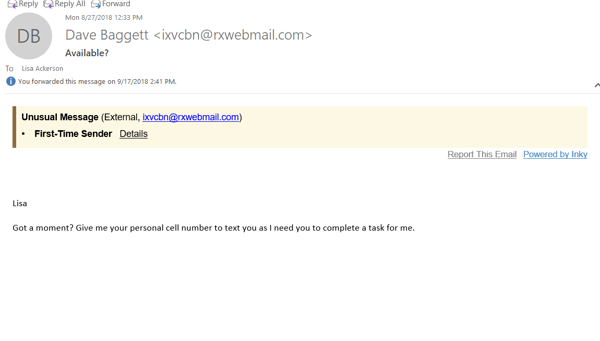
The Inky analytics dashboard allows system administrators the ability to look at all the threats that have been blocked or drill down to individual types of attacks and even individual emails. With a searchable interface, users can search by date, user, or types of malicious attacks.
Inky® Phish Fence is easy to set up in just a couple of hours. It works with Microsoft 365, Google Suite, and just about any email software or system on the market today.
Contact Inky today to schedule a live, personalized demo and see how Inky® Phish Fence can help protect your organization.
Phone: 1 (833) 727-4659
Email: sales@inky.com



