A Market RINGleader
An estimated 12 million video doorbell units are being used worldwide, and leading the market is the Amazon-owned home security system, Ring. The company’s primary product is a video enabled doorbell that detects motion, notifies you someone is at your door, and allows you to see, hear, and speak to your visitor in real time from anywhere. Customers purchase the doorbell and enroll in an inexpensive subscription service so they can store or share videos and receive notifications.
INKY Uncovers A Phishing Attack
In mid-January, INKY detected a brand impersonation and credential harvesting threat. Phishers posing as home security giant Ring, had created a phishing campaign designed to steal credit card information and social security numbers from unwitting customers.
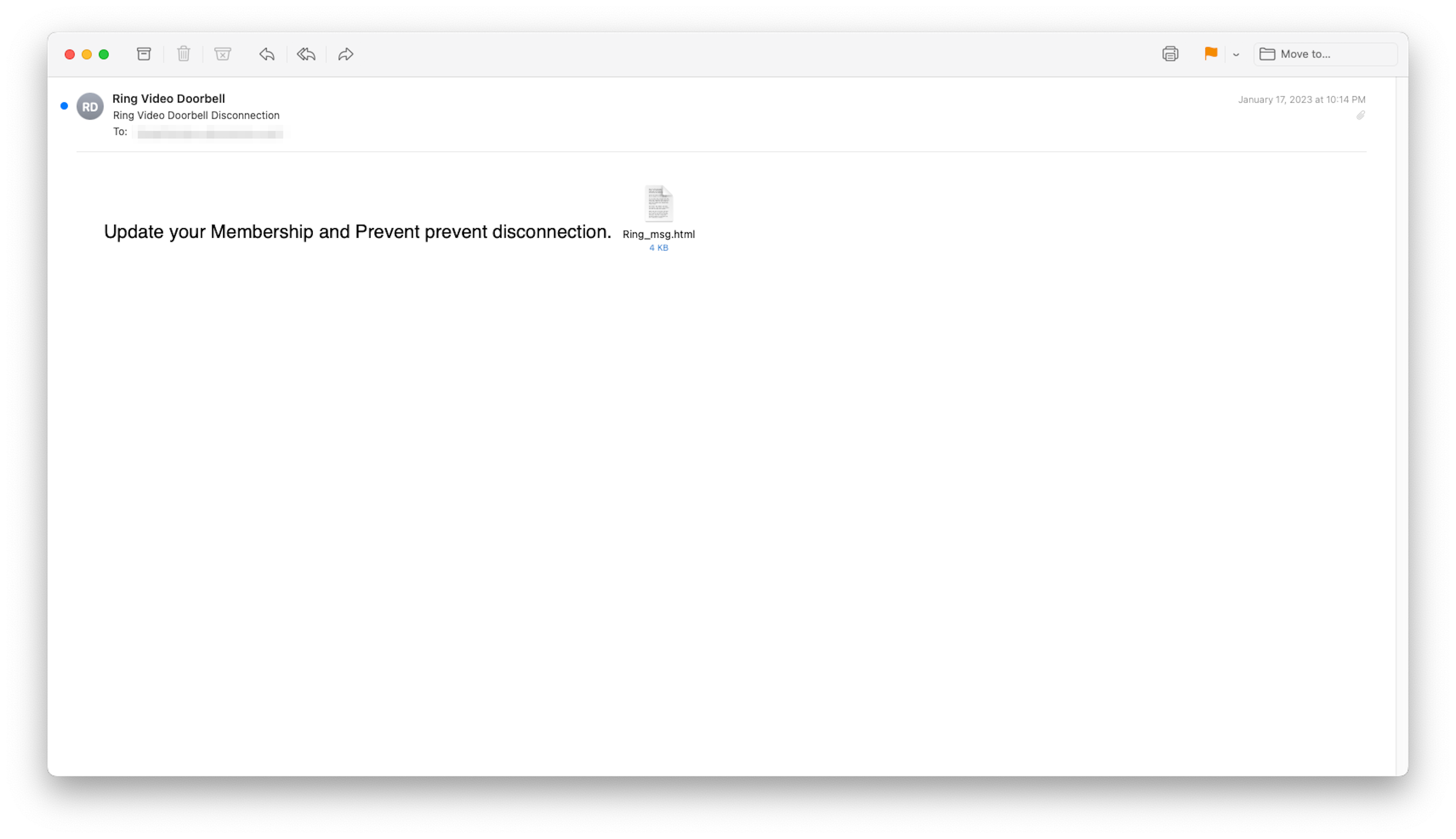
The ploy began with a simple, yet potentially alarming email with a subject line of “Ring Video Doorbell Disconnection”. Customers were told to update their membership to prevent their service from being disconnected. As you can see in the example below, the next obvious step for any concerned customer would be to click on the HTML attachment found in the email. Of course, that’s when the real troubles begin.
What INKY Wants You to Know About Malicious HTML Email Attachments
Malicious HTML email attachments, like the one found in this phishing email, give phishers a strategic advantage because they take users to a malicious website that is now hosted on the victim’s local machine instead of the internet. Standard URL reputation checks are avoided, and phishing content can’t be detected since nothing is hosted on the internet.
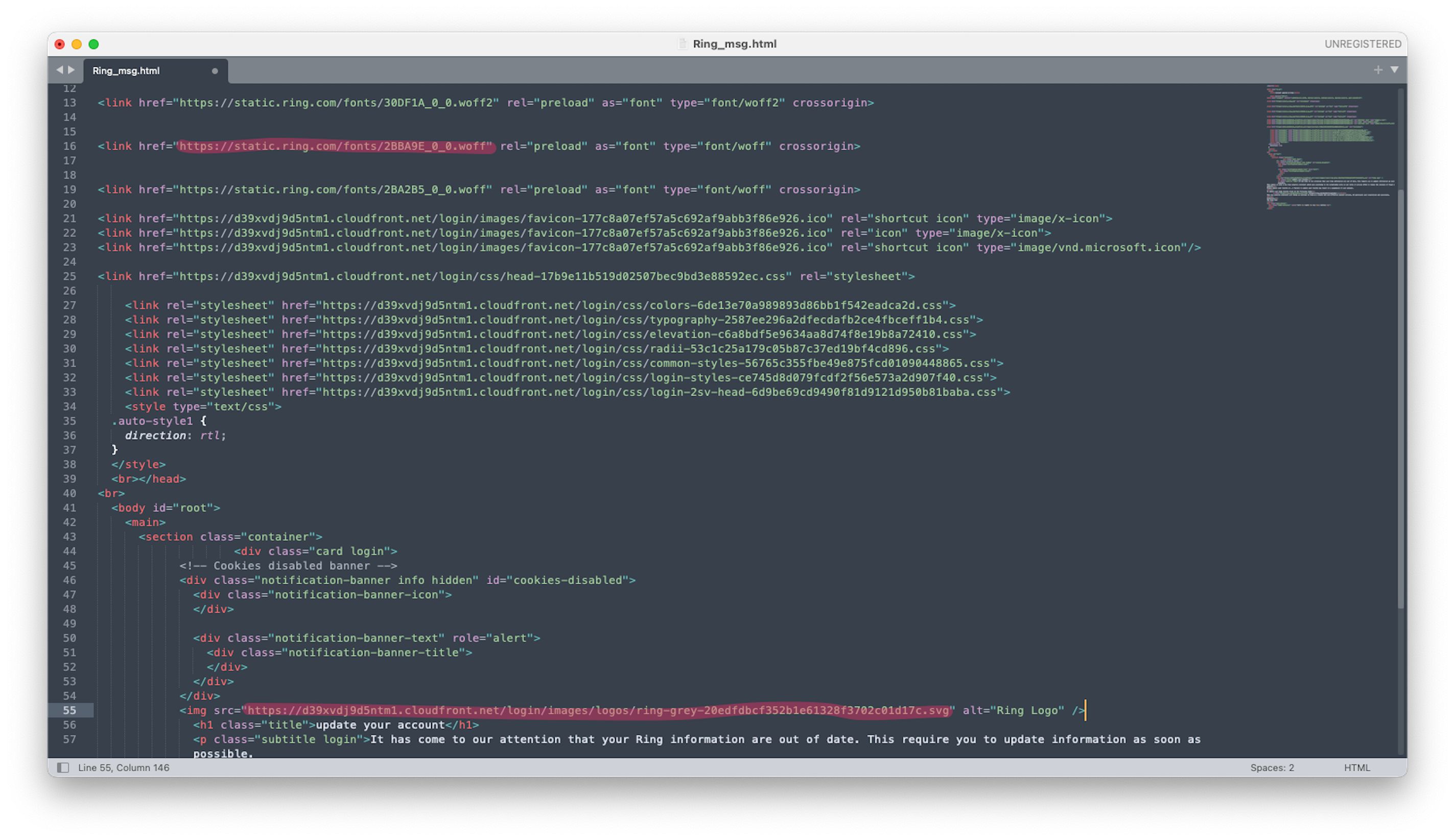
In this case, clicking on the HTML attachment builds a fake Ring website on the recipient’s local machine. An examination of the HTML and CSS code shows this attack using the same fonts, colors, and logo that Ring uses in their real website.
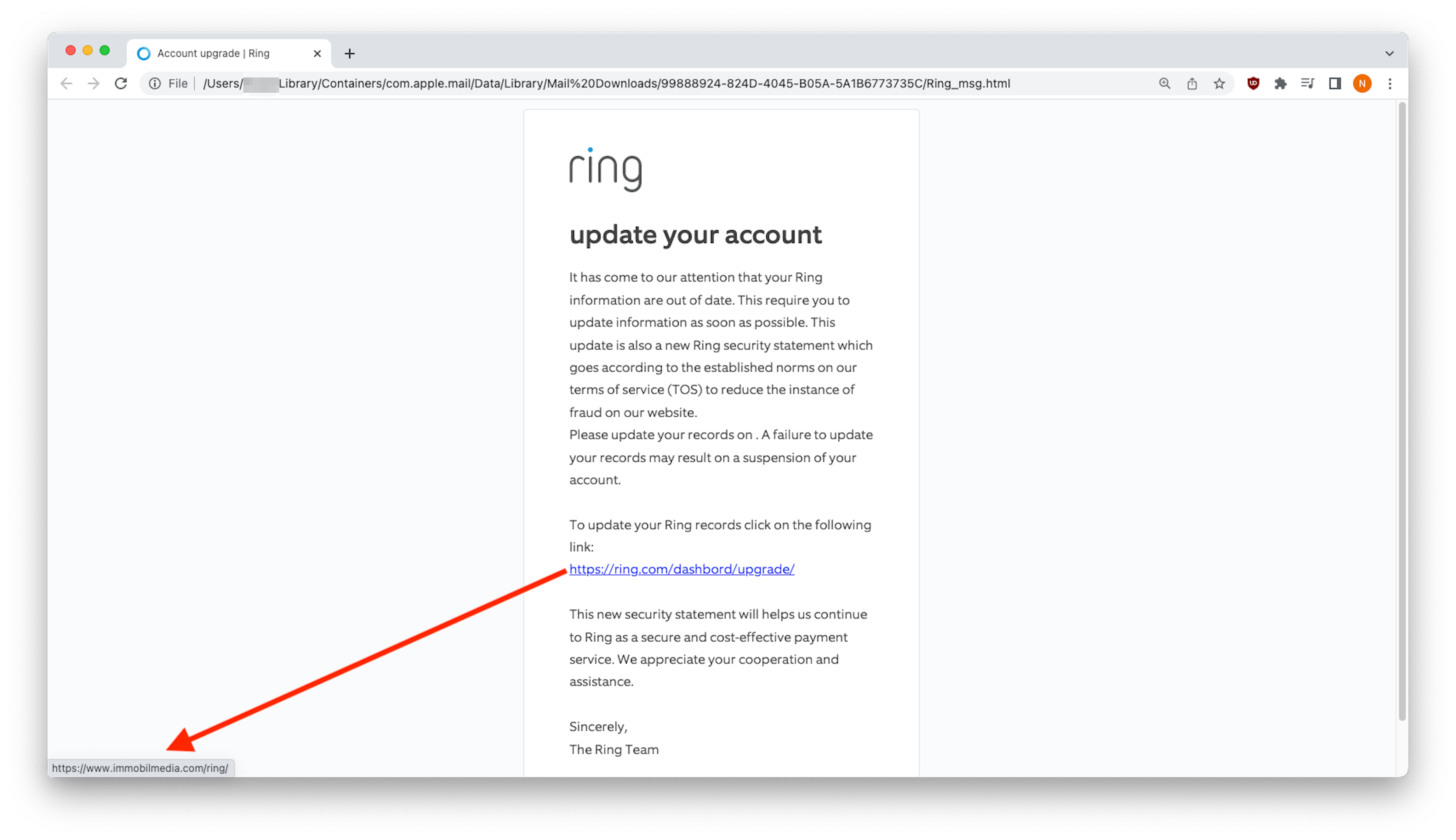
As you can see below, after reading instructions for resolving the issue, victims are given a link to log into their Ring account. Because the hijacked site impersonates a Ring login page (using their logo, colors, and fonts) customers can be easily fooled – especially since the cybercriminals are counting on victims being distracted by potential disconnection of their account. However, upon careful inspection, you can see that the link that appears to go to https://ring[.]com/dashbord/upgrade but is instead directed to https://www.immobilmedia[.]com/ring, an Italian real estate website hijacked to host phishing content.
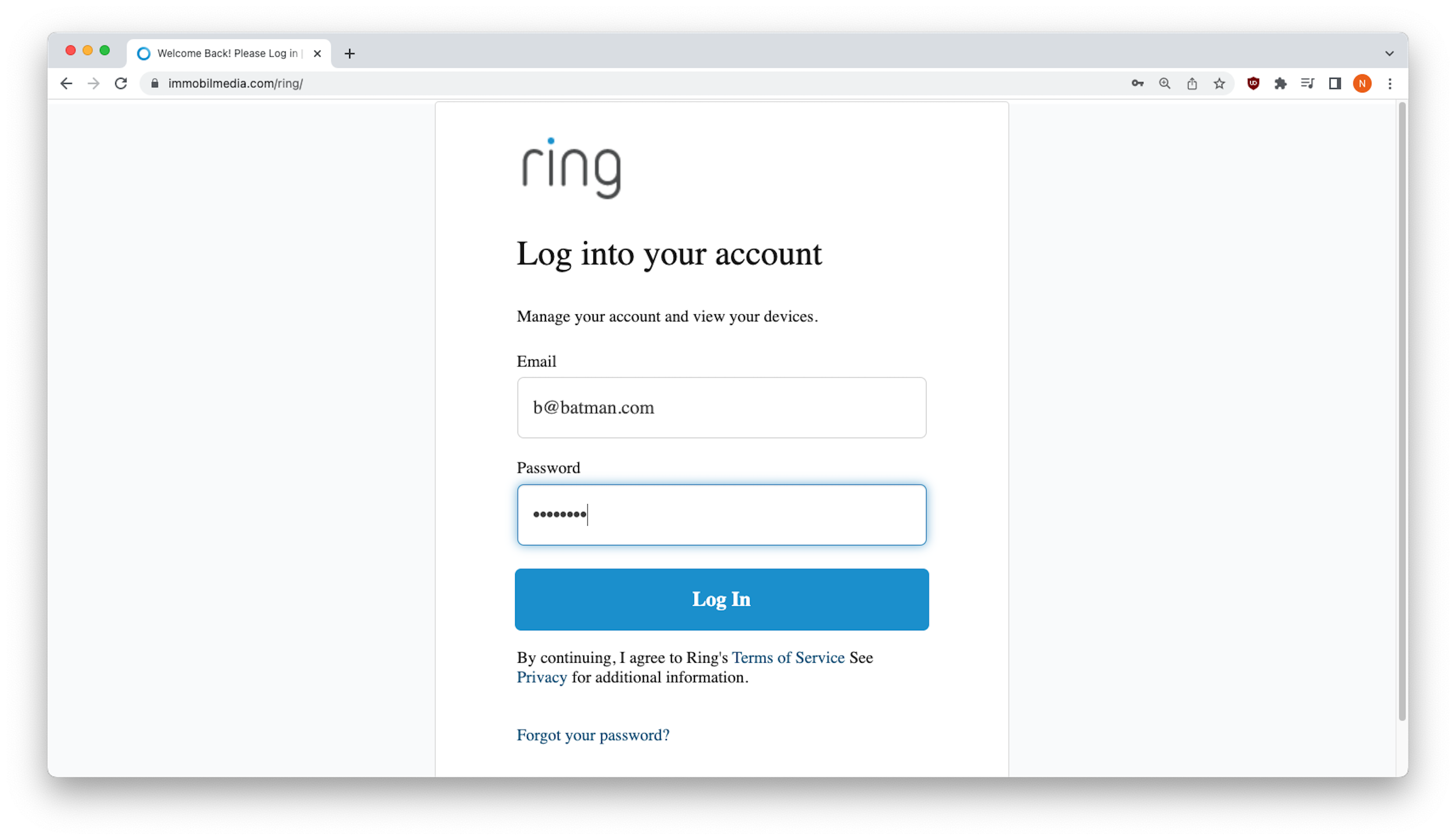
Once victims click on embedded link, they are taken to what appears to be a Ring account login page. What users might not realize is that even when fake credentials are used, the phishing form allows you to move forward…inching closer to the phishers ultimate objective of harvesting credentials.
After completing the login process, customers are presented with a form to update credit card information. The form also asks for a social security number, which is suspicious considering vendors rarely ask for your social security number and hardly ever along with credit card information.
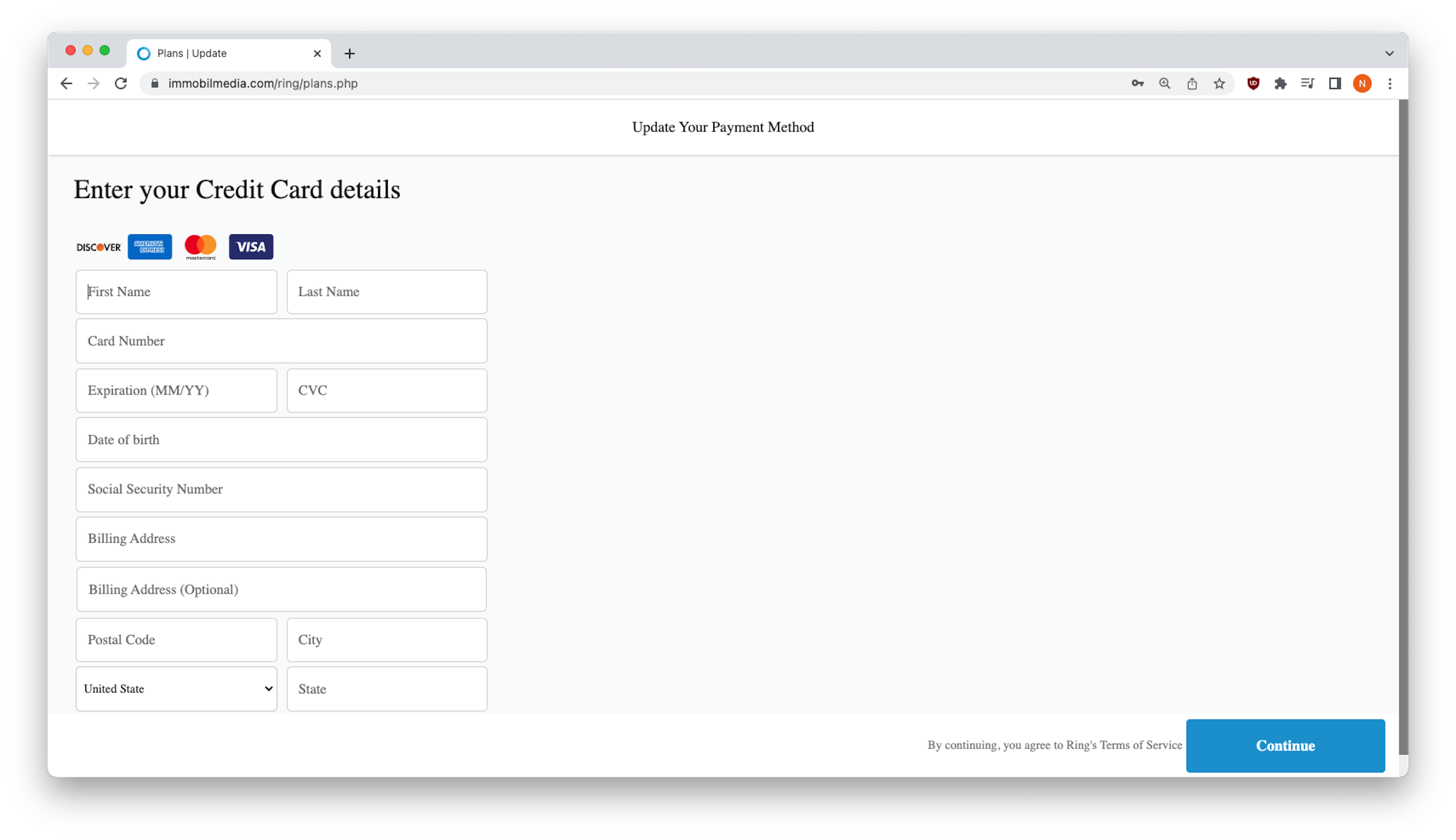
After entering their credit card number and other personal information, victims click on “Continue” and receive a fake account activation notification. Of course, this too should seem odd given that fact that the initial email asked customers to update their information to prevent being disconnected. The message they receive assumes they were actually disconnected.
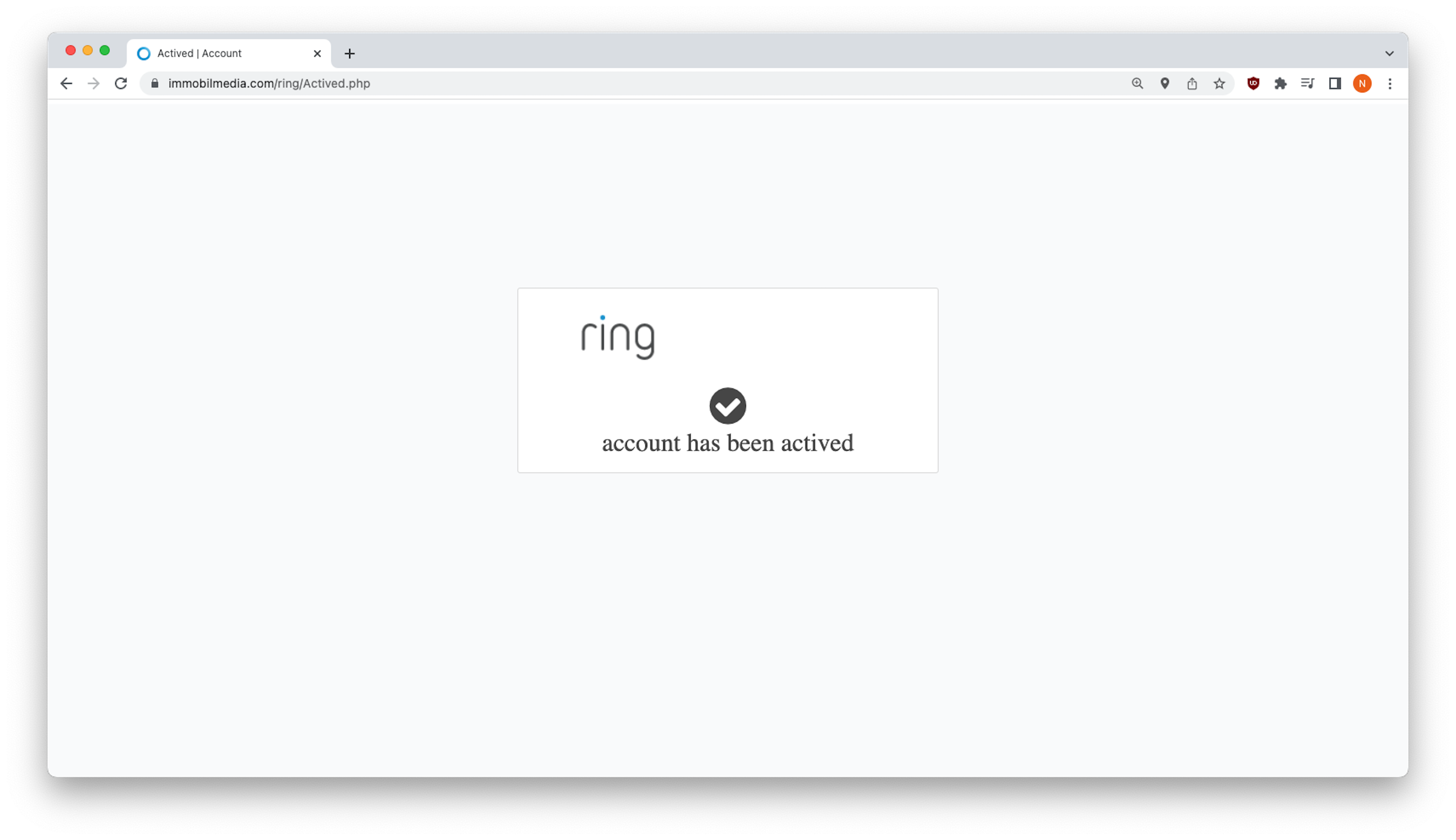
The account activation notification appears briefly and then the web browser redirects victims to the real Ring website. In the meantime, the victim’s data entered on the fake website is sent directly to phishers or stored on the servers of the hijacked website.
A Note from the Grammar Police
As you probably know, a common blunder phishing attacks share is poor grammar and basic errors in usage. While many of these are overlooked by distracted or panicked victims, we like to point them out in an effort to make everyone a little more phishing-conscious. Grammatical errors should be especially rare in instances of brand impersonation since sizable companies have their own writing and editorial teams helping to ensure each customer communication is clear and professional. Let’s take a closer look at our Ring phish.
The Initial Email
- The initial email consists of one direct sentence and has no salutation or signature.
- The word “prevent” is used twice, which is clearly a typo. “…and Prevent prevent disconnection”
The HTML Attachment
- The phishers did a better job with the branding of this message, using the Ring logo and brand colors. It’s even signed by “The Ring Team”. However, they could have used a proofreader.
- The first sentence is grammatically incorrect - “your Ring information are out of date”. Information is singular and therefore should be “is out of date.”
- Second sentence – “This require you” should be “This requires you”.
- The third sentence is just a jumbled hot mess. How can an update be a security statement? Established norms “on” should probably be “of” or “in”.
- The fourth s is not a complete sentence and begs for a paragraph break.
- The fifth sentence, “may result on a suspension”, is incorrect.
- There are other issues throughout, but sadly, most people probably scan the content and jump quickly to the sentence containing the account updating link.
Login Page
- The disclaimer should have two sentences but there is no punctuation separating the thoughts.
- “See Privacy for additional information” needs a few more words to make sense.
A Recap of Phishing Techniques
There were a number of common phishing techniques used in the Ring phishing scam.
Brand Impersonation — uses company logos and trademarks to impersonate well-known brands to make an email look as if it came from a legitimate source.
Data or Credential Harvesting — collecting personal data under false pretenses. In this case, the victims entered login credentials, SSNs, and credit card information into what they thought was Ring’s website.
Malicious HTML Attachments - encouraging recipients to click on an email attachment that harvests credentials and skirts most anti-phishing technology.
Time Pressure — adds a sense of urgency to the potential loss, again steering the target away from doing a common-sense analysis of the situation.
A Final Word
It’s always a good idea to stay current with the latest phishing scams, understand what’s really happening behind the scenes, and implement best practices whenever possible.
Best Practices: Guidance and Recommendations
- An account issue can be resolved by visiting a company’s website directly instead of clicking on email attachments and links.
- Use your browser’s address bar to confirm that you’re on a website instead of a local file.
- Confirm the domain of the website. In this case, recipients should be suspicious that the Ring login page is hosted on immobilmedia[.]com instead of ring[.]com.
- Be careful with display name spoofing. This example uses “Ring Video Doorbell” as the display name, but recipients should be suspicious that the sender’s email address isn’t an authentic Ring email address.
- Always be suspicious when receiving HTML attachments from unknown senders. Simply opening the file can run malicious code on the recipient's computer.
Always remember, urgency is a phishers best friend. When you feel rushed over an email you recently received, it could be a signal to slow down and pay attention. Of course, the best way to prevent phishing attacks is with the help of a third party. INKY watches out for fake account update messages and all other types of phishing emails every day, around the clock to keep companies safe. We provide the most comprehensive malware and email phishing protection available. INKY is also the only behavioral email security platform which means not only do we block phishing attempts, we also coach users to make safe decisions – everywhere, all the time. By signaling suspicious behaviors with interactive banners, INKY guides users to take safe action on any device or email client.
Find out what INKY can do for you. Request a free demonstration.
----------------------
INKY is an award-winning, behavioral email security platform that blocks phishing threats, prevents data leaks, and coaches users to make smart decisions. Like a cybersecurity coach, INKY signals suspicious behaviors with interactive email banners that guide users to take safe action on any device or email client. IT teams don’t face the burden of filtering every email themselves or maintaining multiple systems. Through powerful technology and intuitive user engagement, INKY keeps phishers out for good. Learn why so many companies trust the security of their email to INKY. Request an online demonstration today.


