In phishing attacks, scammers send out emails to attempt to trick users into taking a specific action. The action might be clicking on a link that launches a malware attack, requesting a wire transfer to a vendor, or revealing personal or financial information.
The attacks are increasingly sophisticated and growing in number. 76% of IT professionals report their organization has experienced a phishing attack within the last year with an average click through rate of 9%. In the latest iteration, scammers are targeting C-Suite executives.
What Is Spear Phishing?
In spear phishing, the email attacks have become highly customized. The bad guys take the time to gather highly personal information to convince the recipient that the emails are legitimate. They sometimes gather that information by hacking into an organization’s computer network, scouring their website or public filings, or visiting social networking sites.
Once they have the info, they craft a compelling email that looks like the real thing. They will offer all sorts of legitimate-sounding reasons as to why you need to click on the enclosed link or send your personal or financial information. They may send you to a custom, realistic looking website or landing page where you are asked to provide passwords, account numbers, User IDs, access codes, PIN numbers, routing numbers, or wire transfers.
Examples of Spear Phishing In The C-Suite
Under one scenario, scammers spoof the email address of a C-level executive using information listed in a company’s public filings. They then send an email, addressing by name the person in the company’s finance department that can send wire transfers. The scammer, impersonating the CEO or other top-level executive “authorizes” the wire transfer and directs the subordinate to make the payment.
In some cases, it goes beyond spoofing an email address. By sending a phishing email directly to the C-Suite executive, the hackers gain access to the victim’s email account and use the actual account to send the authorization.
A spear phishing attack at Ubiquiti Networks used a scheme similar to this to steal $46.7 million before being discovered. Another U.S. business, The Scoular Company was conned out of $17.2 million in installments when an exec received an email telling him to wire the money to a Chinese bank.
An executive at EMC Corp triggered malware when he opened an Excel spreadsheet attached to an email. The attachment was titled “Recruitment Plan,” but exploited vulnerabilities in Adobe Flash to open up a backdoor and harvest credentials. Not only did it impact the company under attack, but it potentially compromised sensitive data from defense contractors that did business with the firm.
The tactics vary. It can be as complex as those above, or as simple as making it seem like a delivery company is giving you an updated on a package being sent. The scammers will try anything to hack into your system.

Costs of Spear Phishing
When targeted email spear phishing attacks strike, it can be expensive. 80% of the companies that were victims of spear phishing report suffered monetary losses, according to a study of 1,000 companies in the U.S. and U.K. The larger companies that were victims of spear phishing attacks revealed an average loss of 1.6 million dollars. 15% of the companies surveyed also experienced a dip in stock prices.
It wasn’t just unsuspecting employees that fell victim to these attacks. The prime targets for spear phishing were IT employees, Finance department employees, and C-Suite Executives, according to the study.
Top Targets for Spear Phishing:
- 44% IT Professionals
- 43% Finance Department
- 27% C-Suite Executives
An aerospace manufacturing company in Austria, FACC, not only lost $50 million but terminated its CEO. Crelan Bank in Belgium fell victim to a C-Suite spear phishing attack. It cost them $75 million. Even Facebook and Google were tricked in phishing attacks to the tune of $100 million.
Anti-Phishing Solution by INKY
You can’t afford not to be protected. Inky’s anti-phishing solution is the most comprehensive solution to your email phishing and malware concerns.
Using sophisticated machine learning, artificial intelligence, and computer vision algorithms, it blocks deep-sea phishing attacks that other systems pass through.
Every internal and external email is scanned by Inky Phish Fence to ID and flag phishing emails. Unlike other systems on the market, Inky “sees” each mail as the recipient would. Unlike a human reading the email, however, Inky Phish Fence can tell if the email is a forgery or a phishing attempt. It can either quarantine the mail or deliver it with disabled links and a warning for users.
Automatic reporting flags phishing email within the email itself. This alert shows in desktop and mobile because the link is in the email and not just the header.
Dashboard analytics provide comprehensive reporting on blocked threats. In addition to an overview, the system administrator can drill down to individual messages and search by date, users, and types of malicious emails.
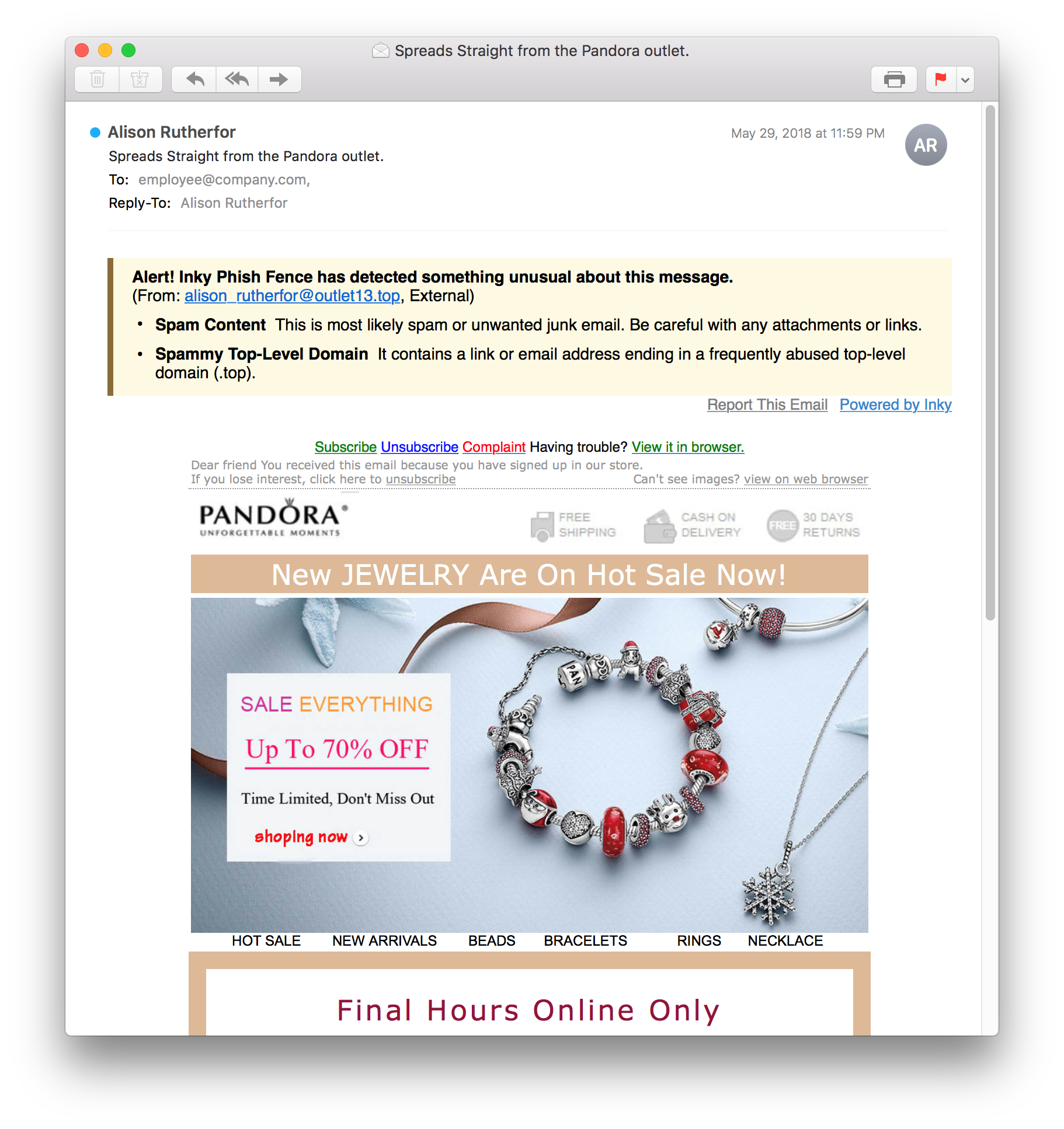
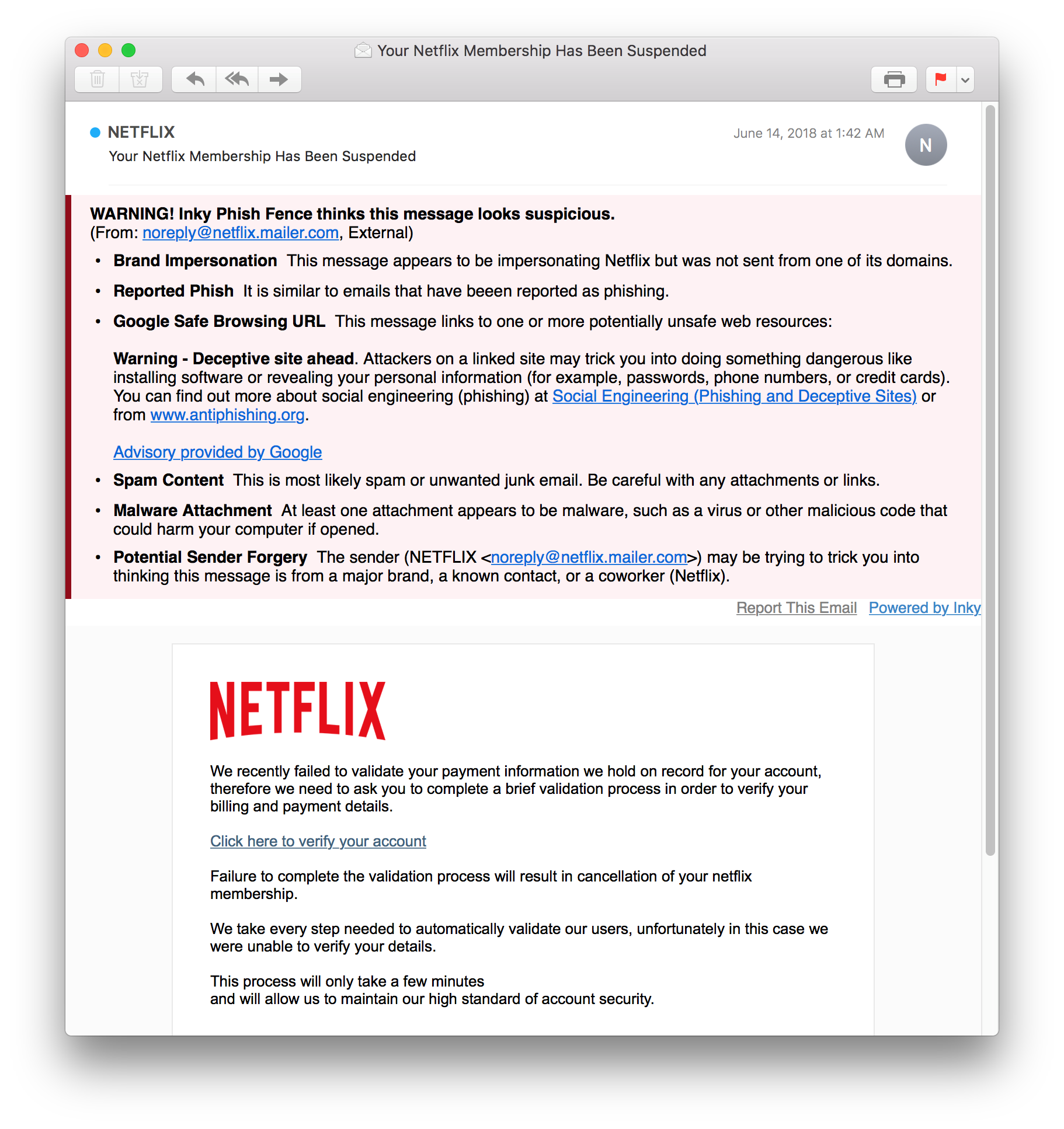
Automatic reporting flags phishing email within the email itself. This alert shows in desktop and mobile because the link is in the email and not just the header.
Dashboard analytics provide comprehensive reporting on blocked threats. In addition to an overview, the system administrator can drill down to individual messages and search by date, users, and types of malicious emails.
Inky sits on top of Microsoft Office 365, Google Suite, and other email systems and can be set up in just a few hours.
To see a demo of Inky Phish Fence in action, contact Inky.



