Over the past few years, the cyberattack landscape has shifted. Malware (malicious software), once the center of most cyber exploits, is used less and less. Cyber defenses, particularly from Microsoft, the primary business platform, have grown in effectiveness, narrowing criminal opportunities from that vector.
Black hats have adapted, seeking to probe the weakest link in the cybersecurity chain: the human. The most effective attacks these days come from compromised email, sometimes known as business email compromise (BEC). However, BEC doesn’t really capture the scope of these exploits, since many of the initial forays are aimed at individuals (rather than businesses) in their role as ordinary citizens. Once a phisher has harvested credentials from an individual, he uses them to probe not only that person’s other accounts, but frequently the soft underbelly of their organization, or perhaps one of that organization’s partners, suppliers, or distributors.
In order to fool an individual into giving up their credentials, phishers need to impersonate something or someone. The two broad categories of impersonation are brands and colleagues (often VIPs). The best impersonations look so much like the genuine article that most email security software gets fooled, too. The problem lies in the basic way these defensive products go about their business. Essentially, they refer to existing repositories of known exploits and try to match a new email to any known attack signature. Of course, this method misses anything not seen before, the so-called zero-day threat.
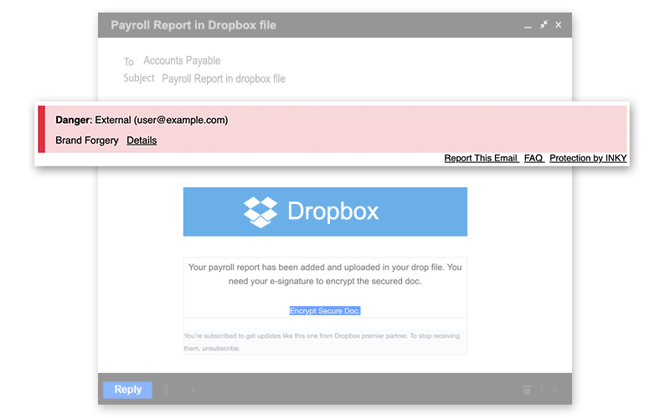 Example of a Brand Forgery email
Example of a Brand Forgery email
INKY's Email Assistant has flagged this email with a red warning banner.
Microsoft has made the best of this method, though. Millions of Microsoft 365 (M365) customers are now using the basic Defender package with telemetry turned on. When a M365 client in the field reports back that it has found something it thinks is bad, that information can be analyzed quickly and broadcast back out to all M365 customers, thus keeping everyone updated. Defender also does sandboxing (detonating a payload in a safe location, where it can’t harm other system resources) and URL rewriting (a process that inspects links before letting a user through to a website). These measures fend off many threats.
However, Microsoft’s approach is still backward-looking and doesn’t do well detecting BEC attacks because an email from a compromised account, particularly one with no easily-discernable payload, doesn’t hit tripwires. The sender looks legitimate, and the email may not match known threats. Perhaps the payload is simply a telephone number that, under some pretext, the recipient is requested to call (with the other end manned by an operator skilled at extracting personal information).
Social graphing is one way to mitigate BEC attacks. It goes like this: from the day a new mailbox is established, the social graphing model creates a sender-recipient pair for every sender to the new recipient. With various artificial intelligence techniques, a profile is built for each sender, based on many parameters, including hard data like the sending machine's make and operating system, but also soft data like whether this person’s salutation is normally, “Hi, Bob!” or whether they use ellipses in their text. In INKY’s case, it takes about 11 days of normal traffic to build a profile robust enough to be reliable. And, of course, it gets better with time and repeat senders.
Social graphing is only one model among many that INKY applies to impersonation detection. It is an important component of VIP (and other employee) impersonation, which itself is often associated with insider attacks and BEC. When a criminal poses as a VIP, it looks like an insider attack from the organization’s point of view.
In the area of brand impersonation detection, the greater emphasis is on deep machine learning, computer vision, and other advanced AI techniques. From a store of more than 300 major brands, INKY uses computer vision to render an email’s HTML in the cloud and “look” at it as an image (even though it is never viewed on an actual screen). AI models are trained to recognize logos and other brand elements, and even correctly recognize distorted images. By also analyzing the email’s pathway, a higher-level model can check to see whether the real original sending address is under the control of that brand’s organization. INKY’s detection raises a flag when the two differ.
In addition to analyzing behavioral aspects of black hats’ trying to deceive, INKY uses behavioral incentives to help email users understand the threat environment (without getting in their way). INKY’s smart banners coach protected recipients and senders on what’s sensitive, what looks dangerous, and what needs attention. This continuous training teaches employees without punishing them.
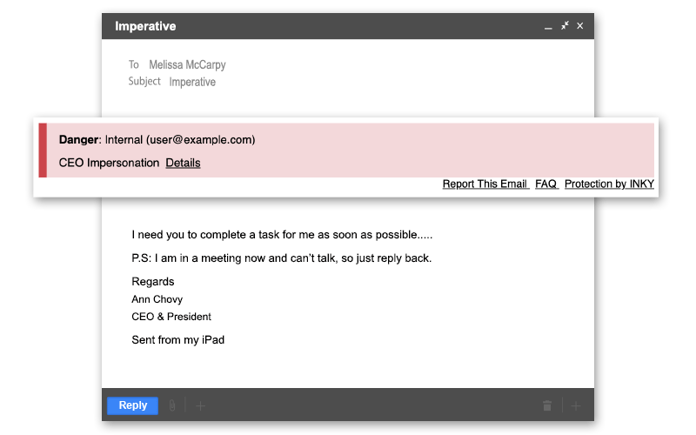 Example of a CEO Impersonation email.
Example of a CEO Impersonation email.
INKY's Email Assistant has flagged this email with a red warning banner.
Verizon’s 2021 Data Breach Investigations Report noted that more than 60% of all cyberattacks last year were based on credential theft through impersonation of some sort. At this point, email account takeover is the largest single threat vector.
Microsoft’s solution lacks important elements necessary for defending against this type of attack. Rather than building profiles automatically via social graphing, the company expects subscribers to define a maximum of 80 VIPs, whose mails gets an extra level of scrutiny. Also, Microsoft does not use computer vision on email, has no specific protection against impersonation and account takeovers, and makes no use of smart banners to guide email users’ decisions.
Gartner, among other analyst firms, recommends that M365 users add a layer of protection of the type that INKY offers to guard against impersonation, which is now the most prevalent type of cyberattack.
------------------------
INKY is the behavioral email security platform that blocks threats, prevents data leaks, and coaches users to make smart decisions. Like a security coach, INKY signals suspicious behaviors with interactive banners that guide users to take safe action on any device or email client. IT teams don’t face the burden of filtering every email themselves or maintaining multiple systems. Through powerful technology and intuitive user engagement, INKY keeps bad actors out for good. Learn more about INKY™ or request an online demonstration today.


