I am a Certified Information Systems Auditor. I’m Certified in Risk and Information Security Controls, I’ve been working in the IT Governance and Compliance space for the better part of 20 years, have taken organizations through ISO27001 and SSAE 16 certifications, yet without INKY’s Phish Fence would have struggled to recognize today’s “Catch of the Day”.
What is Email Spoofing?
Email spoofing or brand forgery is a form of fraud, and is often a key technique in the execution of identity theft. A great brand forger is an artist. Whether they are copying paintings, fabricating currencies, or passports, a forger is often the equal of those they seek to emulate. Sadly, despite their powers, the forger’s energies are directed at hurting and defrauding others.
As you'll see in the forgery example below, painstaking effort has been taken to create to a masterful phishing email. This specific example is masterful in its design, yet fruitless in its efforts, because INKY adapts as quickly as the phishing attackers do.
Here's the scam email without INKY's banners in place:
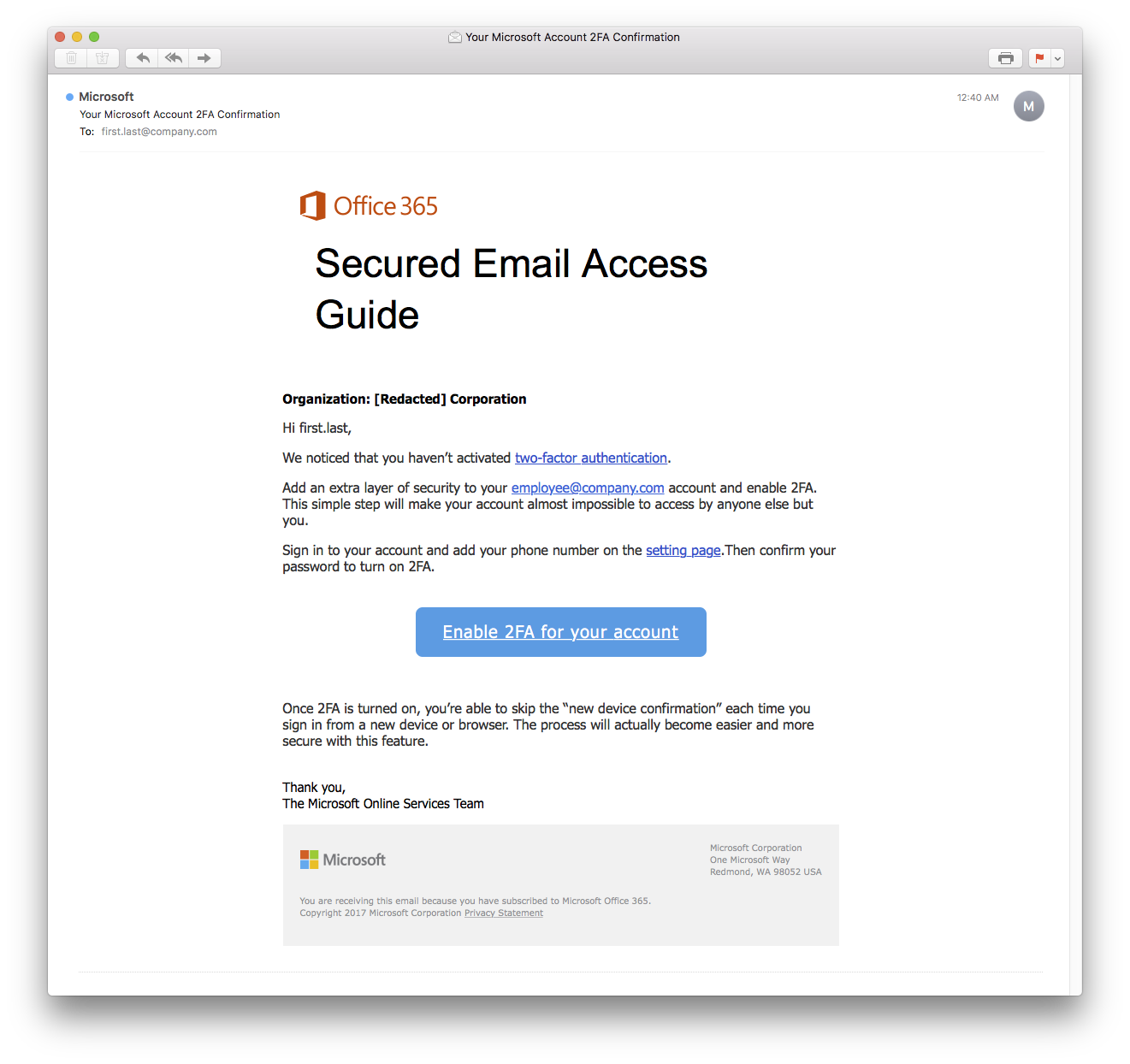
Looks like a pretty legitimate email, right? I probably wouldn't have questioned it, but I have INKY anti-phishing software running, and this is what the email that came into my inbox looked like with INKY's flagged red banner:
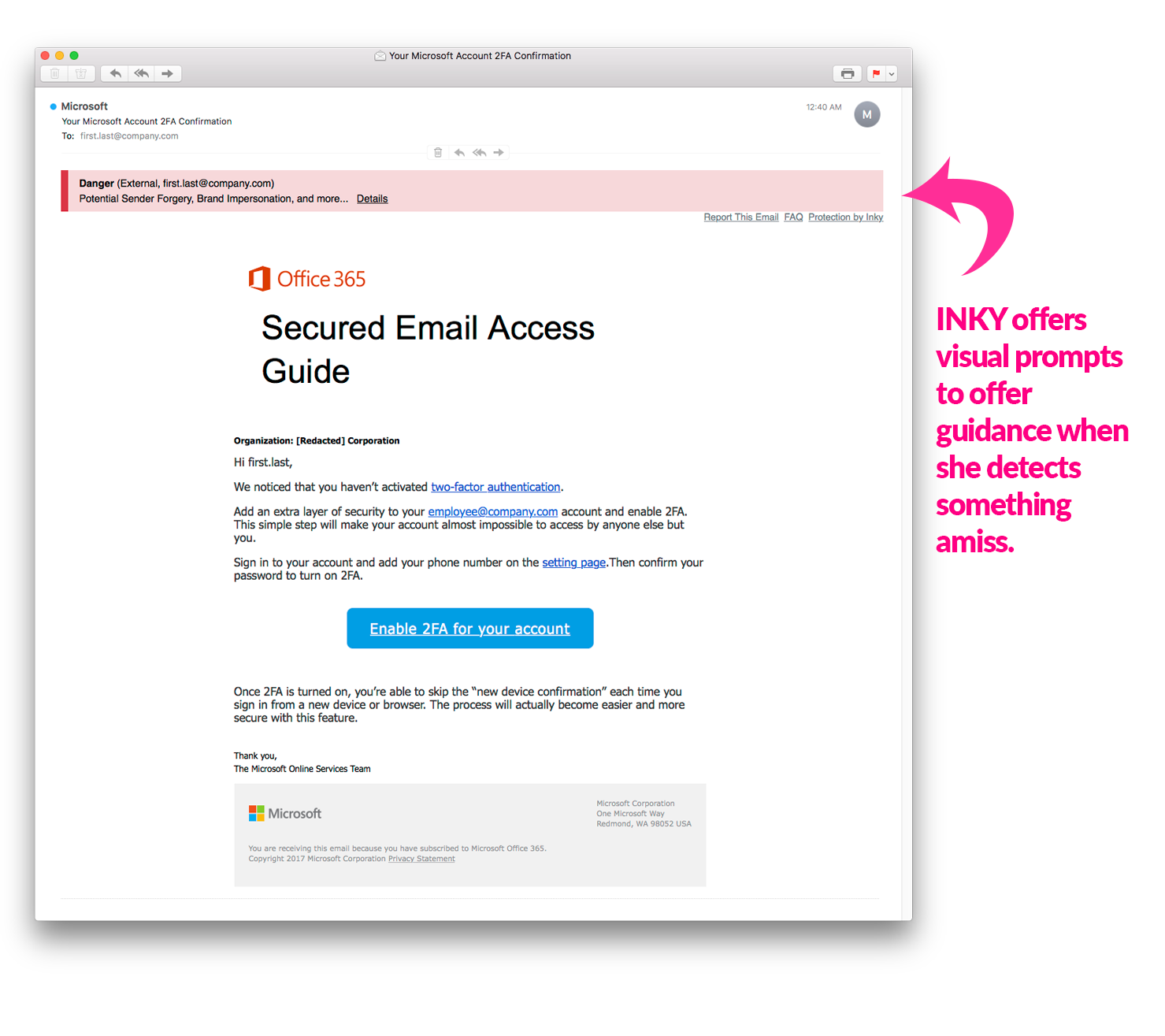
I'm not often fooled by these emails, because again, I am a security expert. I live and breathe this stuff. But the attackers are getting more clever by the day, and I had to really take a deep look at this one.
They’ve taken a legitimate email from Microsoft, copied the HTML, and made a few minor tweaks that are nearly impossible to catch with the human eye, and made the email look like it was coming from myself.
How do phishing attacks get through Microsoft Outlook filters?
Often phishing attempts like this bypass internal spam filters, and in this case even Microsoft's Exchange Online Protection (EOP) filter, likely because it claims to be from my own domain.
Critical to many of the phishing attempts, the criminal has gone to great lengths to provide careful visual diversions. In this case, the email links all terminate at web.core.windows.net, which is used by Microsoft to park all new Azure hosted websites until a customer selects a custom domain name. Again, for the cybercriminal, making the email look as legitimate as possible is critical for the scam to have any chance of success at baiting the user to take action.
The page linked from the ‘call to action’ is a clever replica of an Office365 account login page, that is has been hosted at ‘windows.net’.
The images in the original email are pointing to images hosted by the Google proxy (googleusercontent.com/proxy/…) which is akin to running your fake Benjamin’s through the tumble dryer, the images have been carefully laundered to create the illusion of authenticity.
In the end, despite their best efforts, another Phishing boat finds itself strewn across the rocks, INKY immediately spotted the questionable IP and, combined with some dodgy grammar, alerted me that this email was, in the end, another clever forgery.
Phish Fence intact. INKY victorious.
Ready to see how easy it is to add INKY to your business email system, to ensure your users don't get baited by these cyber-crime attempts?
Request a DEMO today to see how INKY is the most effective solution available.




