9 out of 10 successful cyber-attacks start with some kind of email phishing attack. It’s big business for criminals and it’s expected to be an even bigger threat to the enterprise in 2019. Cyber criminals are increasingly sophisticated in their attacks methods and traditional software solutions are not adequate protection. In a recently released report from the FBI, they note an increase of 136% in less than 18 months and attacks in all 50 US states and 150 countries around the world.
While phishing schemes typically try to gain access to user credentials or launch malicious code on an organization’s computers, criminals are using spear phishing techniques to go a step further. Using a sophisticated scheme targeting businesses and individuals, the crooks are conning people into transferring large sums of money.
Spear Phishing Definition
A concise spear phishing definition is characterized as the act of sending emails from a known or trusted sender in order to trick specific individuals to reveal confidential information or perform an act like purchasing gift cards. It takes the form of impersonation or uses enough relevant information to be believable.
The typical low-level phishing attempt may start with something like a request from “Microsoft Security” to reset your account to continue receiving email.
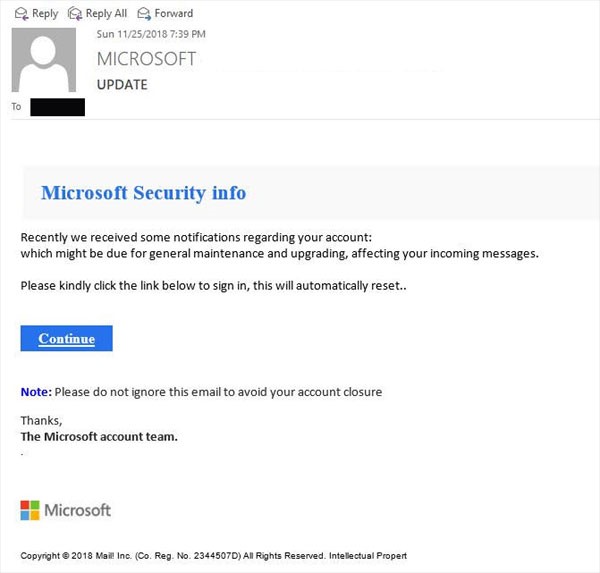
Or it might look like an email from your company's bank asking you to verify a transaction. Knowing you didn’t make one, you might not look too closely and click to a fake web page and provide your login info to dispute the charge. Instead, the bad guys now have access to your accounts and can transfer money.
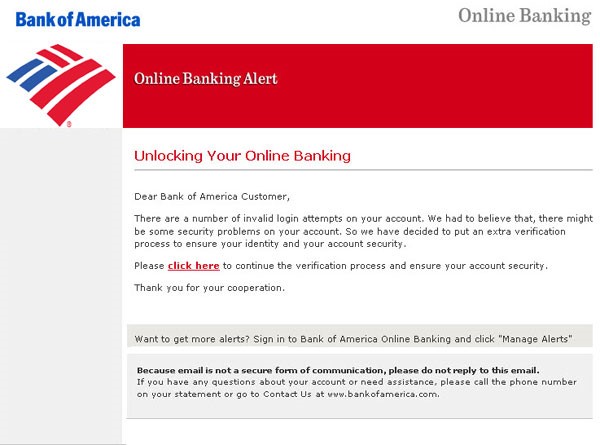
It may just be an email with a link that entices you to click. Clicking may release malicious software or give hackers access to your email or passwords.
Spear phishing takes a more focused approach and is more insidious. The attackers do research and find specific ways to set the hook. They troll Facebook, Twitter, LinkedIn, and other social media to find the right individual and specific information. They might go through public filings or financial reports. Using social engineering, they then craft a custom message that looks legitimate.
They may create a legitimate looking email address designed to look like it is your boss or senior person at your company and use that to send a message to a colleague or subordinate requesting them to take action. Since it appears to come from you it can come off as legitimate. In some of the biggest attacks, scammers target CEO’s, CFO’s, and HR people because they have access to confidential information and the authority to make things happen.
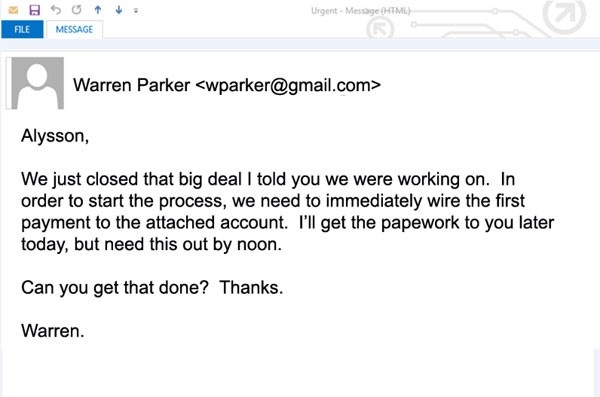
The biggest targets are called whales. That's when the CEO or CFO might be spear phished to wire money. The FBI more formally calls it BEC (Business Email Compromise) and counts $12.5 billion dollars in losses from companies that have been hit since 2013. That’s an average of $2.6 billion a year or more than $712,000 every single day over the past five years.
While it’s important to train your staff on the dangers of email phishing schemes, it’s impossible to train for every scenario and there are new ones popping up almost daily. No amount of training will fix the problem by itself. When it comes to spear phishing prevention, all it takes is one person to click on the wrong link and things can go wrong.
Spear Phishing Definition & Prevention
The best solution to fight phishing scams is INKY’S cloud-based software solution. The Anti-Phishing Solution by Inky provides the most comprehensive email phishing, SPAM and malware protection on the market.
Inky® Phish Fence continuously scans both incoming and outgoing emails using sophisticated machine learning, artificial intelligence, and algorithms to block even the most sophisticated phishing and spear phishing attacks that other systems miss.
When Inky sees a spoofed email address, a forgery, or malicious link, Inky® Phish Fence immediately disables the links and quarantines the email. INKY also uses warning banner in the body of the email. The banners empower employees, giving them important cues as to the content of the emails they are receiving In essence, this helps in training users what to look for and the dangers of phishing email attacks.
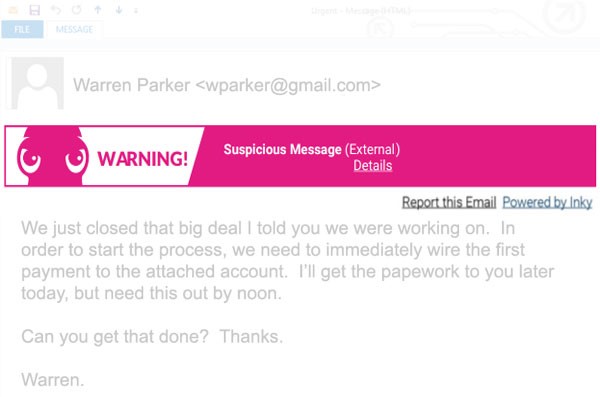
Inky provides a comprehensive dashboard for CISO’s and Admins to view threats in total or look at any individual attack or email in-depth.
Inky® Phish Fence can be ready in just a couple of hours and is fully compatible with Microsoft 365, Google Suite, and just about any email software or system on the market today. Contact Inky today to schedule a live, personalized demo and see how Inky® Phish Fence can help protect your organization.
Inky
Phone: 1 (833) 727-4659
Email: sales@inky.com



