What is Phishing
In fishing, you cast your bait into the water to see what you can hook and reel in. Phishing works the same way. It is a cyber-attack that uses email as a weapon to try to get personal information, financial information, money, or launch malware. Using social engineering techniques to gather information, the attacks have become increasingly customized and dangerous.
Types of Phishing Attacks
There are several ways the scammers try to get you to fall for their schemes. Maybe your employees won’t fall for the Nigerian Prince looking to share his wealth, but what about a message from the boss authorizing payment or an email from you telling them to click here to free up space in their email archive?
The attackers craft emails to look like a trusted brand, such as Microsoft or a well-known bank. Email return addresses may be close to the real ones. They may steal someone’s identity or pose as someone within your company.
In so-called spear phishing attacks, the email may contain highly customized information targeting an individual. The bad guys will go to great lengths to make it appear to be a legitimate contact, including scouring online resources for personal information and even setting up legitimate-looking websites and landing pages to back up their claims.
Attackers also use email phishing scams to launch ransomware attacks on executive computers, locking up data unless a ransom is paid.
Common Phishing Attacks
Wire Transfer Scams are becoming more popular. An email that suggests an overdue bill with late payment fees, or unpaid invoices appearing to be from a legitimate vendor, have hit companies hard in the last year. The scammers have even been successful attacking even the industry’s biggest players. Facebook and Google found themselves victims of an elaborate wire transfer scheme that starting with phishing emails. Targeting the companies accounting departments, the bad guys stole $100 million in payments before they were caught.
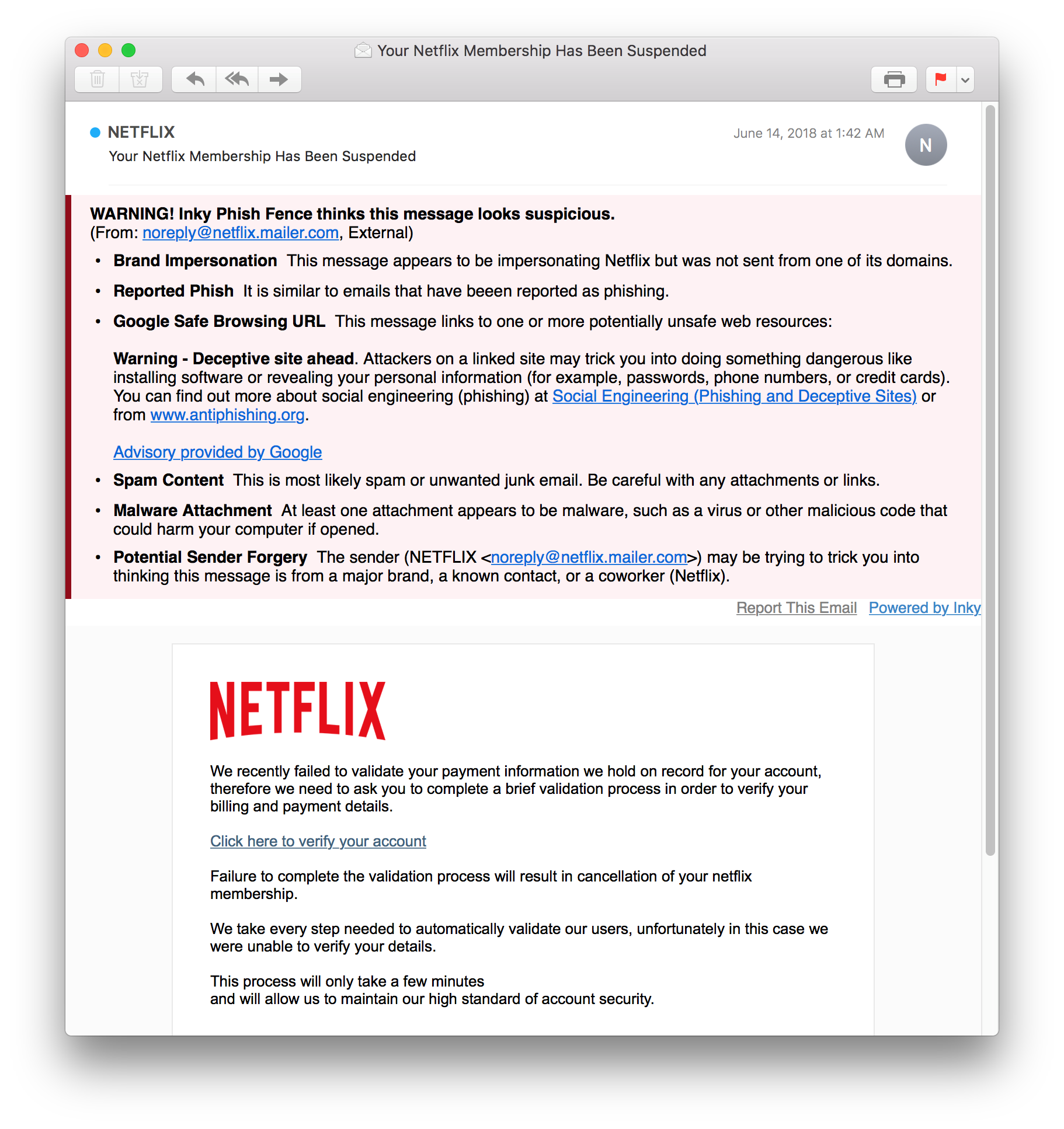
Deactivation scares may claim your email account will be suspended if you don’t verify your information immediately. Email may appear to come from your company’s IT department, or the boss, and ask you to take immediate action. In some cases, scammers will spoof email addresses to make it even tougher for employees to detect.
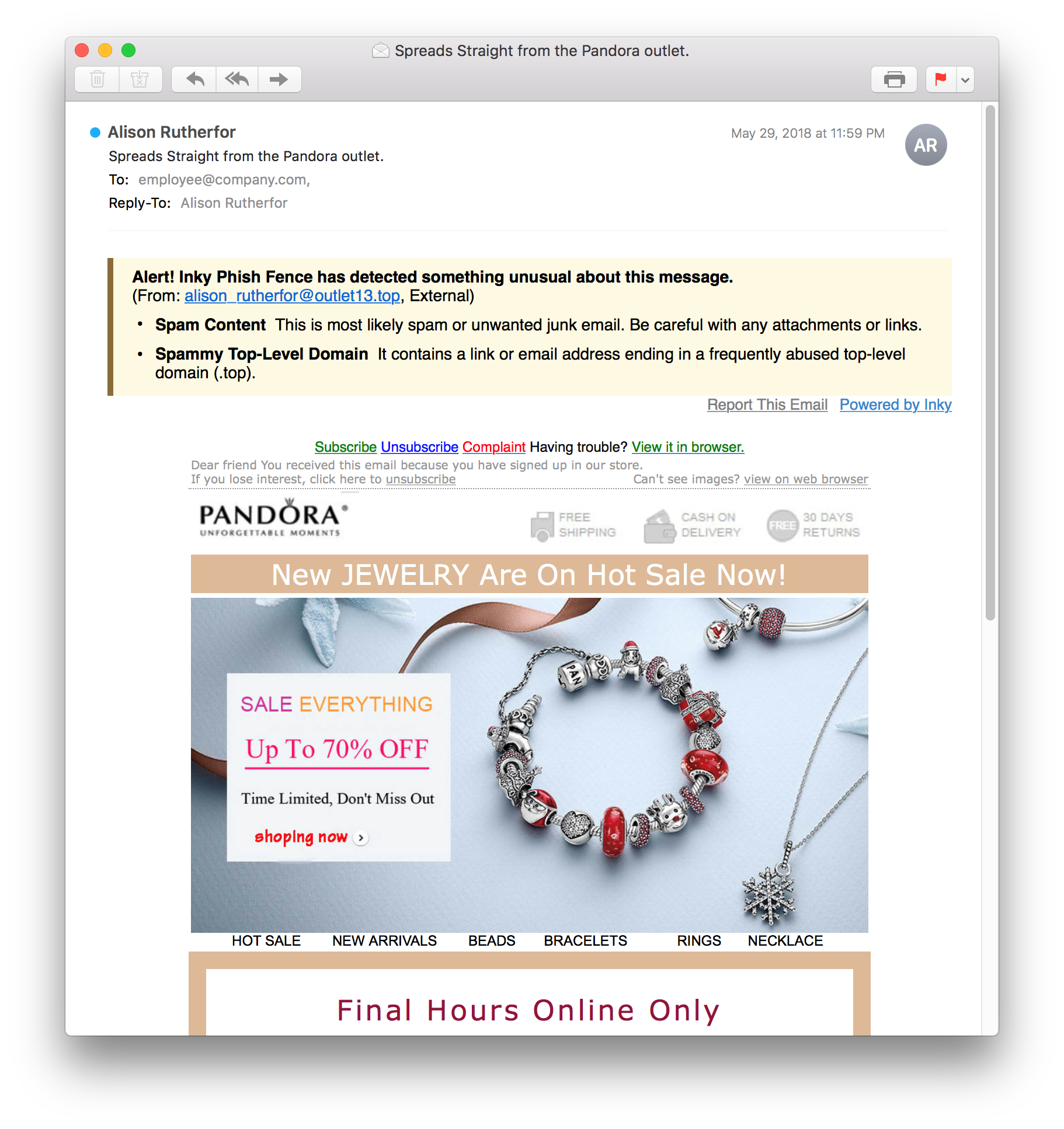
The Save a Friend scam can take several forms. Scammers sometimes hijack social media accounts, or spoof email addresses, to send a personal plea for financial help from someone you know. With so much personal data available online, the messages can sound very convincing. These attacks often peak around natural disasters where you may legitimately know your friends or relatives are living or visiting.
With the rise of smartphones and mobile email, cell phones are no longer safe. Pleas sent through company email will show up on phones. SMS phishing, sometimes called smishing, also target cell phone users.
Phishing Is a Top Concern for CISOs and CIOs Globally
It should come as no surprise that phishing is the top global threat to security at every level. Infosecurity Magazine reports that nearly half of CISOs and CIOs surveyed ranked phishing attacks as their #1 security concern. The rise in the number of attacks has experts rightly concerned. 77% of businesses in the survey say they expect to be the victim of email fraud within the next year.
What Business Are Doing To Prevent Phishing Attacks
Most typically, organizations are doing nothing. While 90% of cyber attacks start when someone clicks on a phishing email, according to cyberintelligence experts at Barclays Bank, 91% of businesses have no solution other than relying on users to spot attacks.
Training users is critical, but it simply will not stop the problem. A study done at Freiedrich-Alexander University in Germany proved that fact. 56% of email recipients and 40% of Facebook users clicked on links for unknown senders even when they knew of the risks. 78% said they were aware of the risks, but their curiosity got the better of them. Those are dangerous numbers to the people responsible for guarding the security of IT systems.
What Are Top CISOs and CIOs Doing About Phishing?
The top internet security professionals are taking action, and not leaving things to chance. Don’t leave your system open to human failings. The Inky Phishing Solution not only safeguards your emails and prevents attacks, it leverages Artificial Intelligence to monitor emerging threats.
Try a free demo of Inky Phish Fence.

About Inky Anti-Phishing Solutions
Inky Phish Fence is the ultimate tool to prevent phishing attacks. By automatically scanning internal and external emails, Inky provides flags and warnings on every suspicious email.
Inky’s Phish Fence sits on top of Google Suite or Office 365. Using artificially intelligence, the system both learns and predicts. The longer you use it, the smarter it gets. It will automatically quarantine malicious and phishing emails.
For Chief Information Security Officers (CISOs) and IT Managers, Inky provides a comprehensive dashboard that allows you to see both an overview and drill down to individual messages to examine the nature of any attack. A searchable database allows for date ranges, targeted users, and specific types of emails.
To try Inky for free, click here to contact us and request a demo.



